This week’s blog comes from Yanna-Torry Aspraki, Business Development & Deliverability Specialist at EmailConsul. In this blog, she gives expert insight into the world of email deliverability and covers the ins and outs of how you can improve yours…Continue Reading: Mastering the Art of Email Deliverability, by Yanna-Torry Aspraki
Security
CRN® Recognizes Red Sift on the 2021 Emerging Vendors List
With a commanding grasp of the IT industry’s unique needs, technology vendors featured on the CRN 2021 Emerging Vendors list allow solution providers to tackle complex IT market challenges, increase bottom-line revenue across the board, and deliver customer-facing solutions that ensure the IT channel’s ongoing success well into the future…Continue Reading: CRN® Recognizes Red Sift on the 2021 Emerging Vendors List
Every day should be Computer Security day
Happy Computer Security Day! Since its inception in 1988, Computer Security Day has been celebrated annually on the 30th of November, but we’ll forgive you if you’ve never heard of it. …Continue Reading: Every day should be Computer Security day
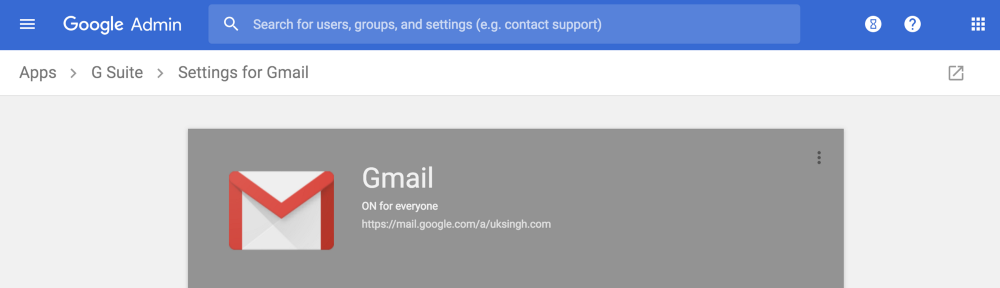
How to make the most of Google’s new anti-phishing and malware capabilities
Google updates include added phishing protection and better defence against malware injection attempts. We’ve written this blog to help you assess the options available to you and help you make the most of them…Continue Reading: How to make the most of Google’s new anti-phishing and malware capabilities
Identity Theft: How attackers get hold of your details
Ever wondered how someone got hold of your details? As per recent headlines, it turns out it’s easier than you think… If you haven’t seen the film Identity Thief, spoiler alert! It’s a perfect rainy day movie and stars the ever hilarious Melissa McCarthy in the brilliant but ridiculous story of a guy who gets his…Continue Reading: Identity Theft: How attackers get hold of your details
12 email security terms everyone should know about
We’ve compiled a short, jargon-busting, no-nonsense overview of what these email security terms mean that will take you from beginner to boffin…Continue Reading: 12 email security terms everyone should know about