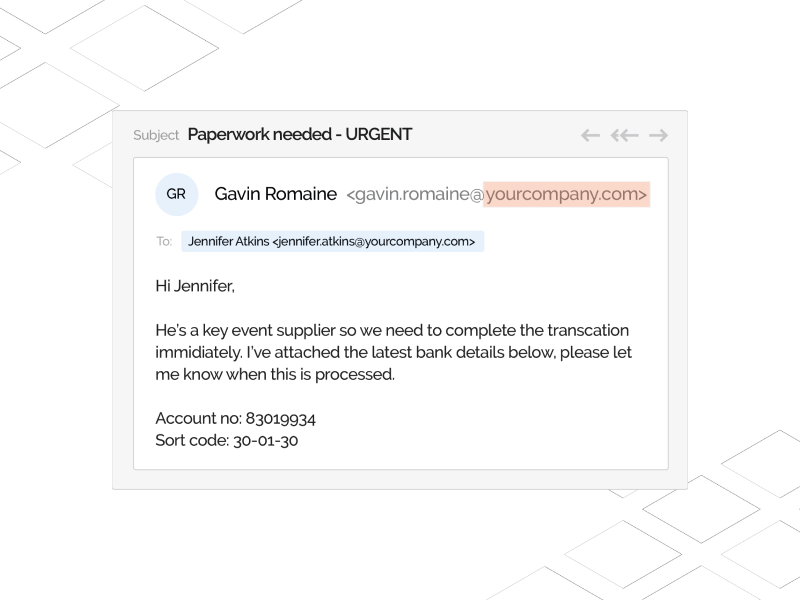
Lately, spear phishing, a type of targeted phishing attack, has been expanding in volume and complexity, targeting big business brands and causing chaos for them. In this blog, we discuss the spear phishing definition, real-life examples, and ways to protect your business…Continue Reading: What is spear phishing and how to protect your business?
Phishing
Spam vs Phishing: What’s the difference and why it matters?
Spam is generally harmless as it’s for marketing and sales purposes. Phishing, on the other hand, has a malicious intent of obtaining personal and sensitive details to attempt cyberattacks…Continue Reading: Spam vs Phishing: What’s the difference and why it matters?
NHS DCB1596 compliance is a great start, but here’s why your domain is still fair game
Healthcare remains one of the most targeted industries when it comes to cyberattacks. But DCB1596 compliance isn’t enough. In this blog, we’ll highlight the areas NHS trusts should address to secure themselves and their patients for the long term. …Continue Reading: NHS DCB1596 compliance is a great start, but here’s why your domain is still fair game
How to prevent phishing attacks
Phishing is a form of social engineering and one of the most common cyber crimes on the web today. According to Cisco, 86% of organizations had at least one user try to connect to a phishing site in 2021. Find out how to prevent it in our blog. …Continue Reading: How to prevent phishing attacks
3 ways your organization is open to brand abuse right now
The larger the digital footprint a brand has, the larger an attack surface it has for brand abuse.
Here are 3 ways that your organization may be open to online brand abuse right now…Continue Reading: 3 ways your organization is open to brand abuse right now
Lessons from the biggest email-driven cyberattacks of 2022
Cybercrime is a lucrative and continuously evolving business that impacts companies of all sizes. Let’s dive into the biggest email-driven cyberattacks of 2022 and the lessons they offer to enterprises. …Continue Reading: Lessons from the biggest email-driven cyberattacks of 2022