As reported by APWG, the third quarter of 2022 saw 1,270,883 recorded phishing attacks, out of which the financial sector was the most heavily affected, burdened with a significant 23.2% of attacks. Lately, spear phishing, a type of targeted phishing attack, has been expanding in volume and complexity, targeting big business brands and causing chaos for them. Cybercriminals design spear phishing attacks smartly and use social engineering tactics so that they pass security checks without getting detected.
In this blog, we discuss the spear phishing definition, real-life examples, and ways to protect your business.
What is Spear Phishing?
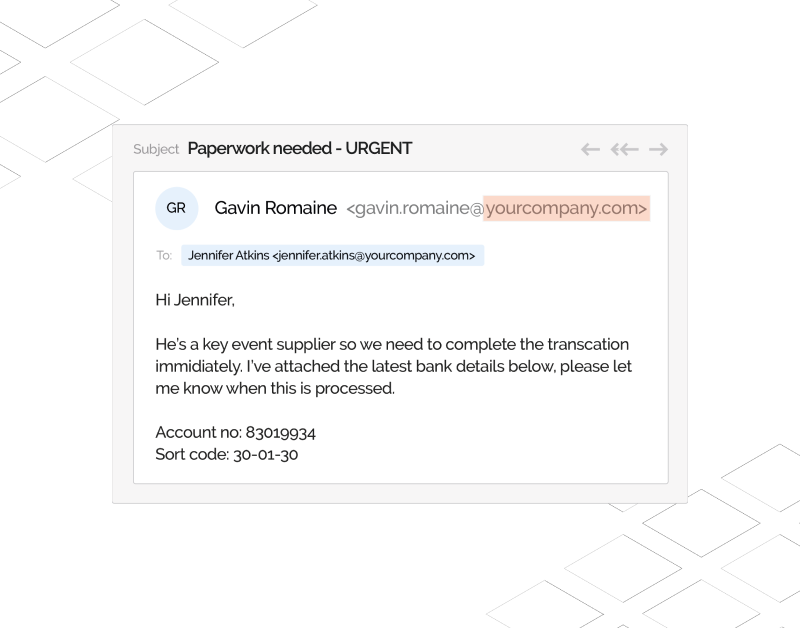
As per the spear phishing definition, it’s a scam where cybercriminals send fake emails manipulating recipients into sharing sensitive and confidential information like financial details, official reports, social security numbers, medical reports, login credentials, etc. They may also ask you to download malware-infected files or links that can access your computer to steal or intercept sensitive and confidential information.
A spear phishing attack is a customized and personalized email message usually based on the information found about the recipient that’s readily available in the open i.e. on LinkedIn. This can include their expertise, interests, relationships, public and residential tax information, etc. Such specific details make emails look more legitimate and reliable, convincing recipients to reply back with the requested information.
Spear Phishing Vs. Phishing
Spear phishing vs. phishing is a common topic. Spear phishing is designed to target a particular individual, group, or business. It requires reconnaissance and knowledge of the target’s interest, user patterns, personal details, etc. to make the email look legitimate.
On the other hand, general phishing attacks are not targeted towards a specific individual, group, or business. These are fraudulent emails sent to random people in bulk; whoever falls into the trap becomes the victim.
Cybercriminals may also use a domain that’s similar to an official one, but has minor spelling alterations. We call these ‘lookalike’, ‘cousin’, or ‘typosquat’ domains. For example, they may send emails from amaz0n.com instead of amazon.com. This wins recipients’ trust and they end up sharing the requested information or downloading malware-infected attachments.
Red Sift’s Brand Trust monitors 150 million newly active hostnames every day, helping businesses to spot when these ‘lookalike’ or ‘typosquat’ domains are being used and initiate their takedown, thus preventing phishing attacks.
What is Social Engineering?
Social engineering is a technique adopted by cybercriminals to exploit human errors to obtain personal information, access, or valuables. They manipulate unsuspecting users into disclosing data, spreading malware, or giving access to confidential and password-protected files.
Social engineering attacks are attempted with intention of theft (information, money, or access) or intercepting or corrupting data to cause harm or inconvenience.
There are usually four steps to a successful social engineering attack:
- Preparation: Cybercriminals start by collecting background information about you or a group that you are a part of.
- Infiltration: They penetrate by establishing a relationship or building a conversation with you.
- Exploitation: You trust the recipient and end up sharing personal information or downloading malicious files which they take advantage of.
- Disengagement: Once you have taken the action requested by the cybercriminal they pull the plug and take a safe exit.
How Many Businesses are Targeted by Spear-Phishing Attacks Each Day?
There’s no specific answer to this, however, according to one source, 88% of companies experienced a spear phishing attack in 2020. This means many businesses are attacked every single day.
What Helps Protect Against Spear Phishing?
Now that you know what is spear phishing in cybersecurity, it’s time to understand techniques for protecting against it. Spear phishing causes more intense damage than general phishing as it’s customized to harm you only. Let’s see how you can stay safe.
Conduct Regular Penetration Testing and Vulnerability Assessments
Penetration testing and vulnerability assessments are often used interchangeably but they aren’t exactly the same. Penetration testing is an authorized simulated attack performed by a real person on a computer or entire IT network. Its aim is to detect system vulnerabilities that cybercriminals can exploit to invade a system.
On the other hand, a vulnerability assessment also looks for system weaknesses but it’s done using automated tools instead of a real person. There’s a higher chance of false positives using this method.
Use Email Authentication Protocols
Email authentication prevents hackers from spoofing your domain or sending fraudulent emails by impersonating a reputed business. The deployment of SPF, DKIM, and DMARC ensures only legitimate emails sent from your domain land in recipients’ inboxes; all unauthorized emails are either marked as spam or are completely barred from entering the mailboxes.
Deploy Multi-Factor Authentication
Multi-factor authentication adds an extra layer of security to your devices and accounts apart from passwords. These may be biometrics, OTPs, answers to special questions, etc. So, even if your password is compromised, a cybercriminal won’t be able to access your account.
Refrain From Clicking Suspicious Links and Downloading Unrecognized Attachments
Before clicking a link, hover your cursor over it (without clicking it), and you will see the website it’s going to redirect you to in the bottom left corner of your computer screen. Click only if you trust it otherwise you may become a victim of a spear phishing attack. Also, don’t download unexpected, unrecognized, or unrequested attachments as these could be infected with malware. Malware can take over your system to steal or intercept information on your computer. Finally, using a Secure Email Gateway (SEG) alongside other inbound email protection tools can help you and your team to identify and avoid malicious emails easier.
Keep Your Software Updated
Updated software has the ability to combat new strategies of spear phishing attacks. Out-of-date applications are easy targets for cybercriminals. You can set them on auto-update mode for effortless protection.
Use a Strong Password
Avoid using the same password for all your accounts and devices. Instead use strong, long, and distinct passwords for all accounts. A strong password is a combination of numbers, upper and lower case letters, and special characters. It’s also good practice to use a password manager to prevent executive phishing.
Educate Your Employees
Lastly, all these preventive measures are of no advantage if you don’t educate your team on how to use them. Humans are the weakest security links, hence they should be aware of spear phishing vs phishing and cyber hygiene practices. However, make sure you have put the technical measures in place to help employees, such as DMARC and personalized inbound threat detection.
Final Thoughts
Spear phishing attacks target specific individuals to steal and intercept confidential and sensitive information. Red Sift’s Brand Trust shuts down phishing sites while also discovering and protecting legitimate domains. OnDMARC also prevents spear phishing attacks by helping you deploy SPF, DKIM, and DMARC for your email-sending domain. This ensures cybercriminals don’t misuse your domain to send fraudulent emails in your business’s name.