At Red Sift we often get asked “what next?” after someone has thrown the p=reject switch. Yes, a lot of the really hard work has been done, but like with all things security-focused, constant care and attention are needed to stay one step ahead of phishers, spoofers, and hackers.
Maintain existing email sending services
For your DMARC record to carry on protecting your organization it needs regular care and attention, take your eye off the ball and SPF or DKIM might break at some point and you’ll have your emails rejected without knowing it has even happened. There are a few reasons why this might happen:
- Email Forwarding
When someone forwards an email, SPF is broken.
- Misalignment
If you’re using a third-party sending service then DKIM keys can get out of sync.
- Server Overload
Sometimes an ISP, during high email peaks, may turn off DKIM checking as it requires high processing resources.
Without OnDMARC you’ll struggle to pinpoint when this happens or be able to fix the underlying root cause.
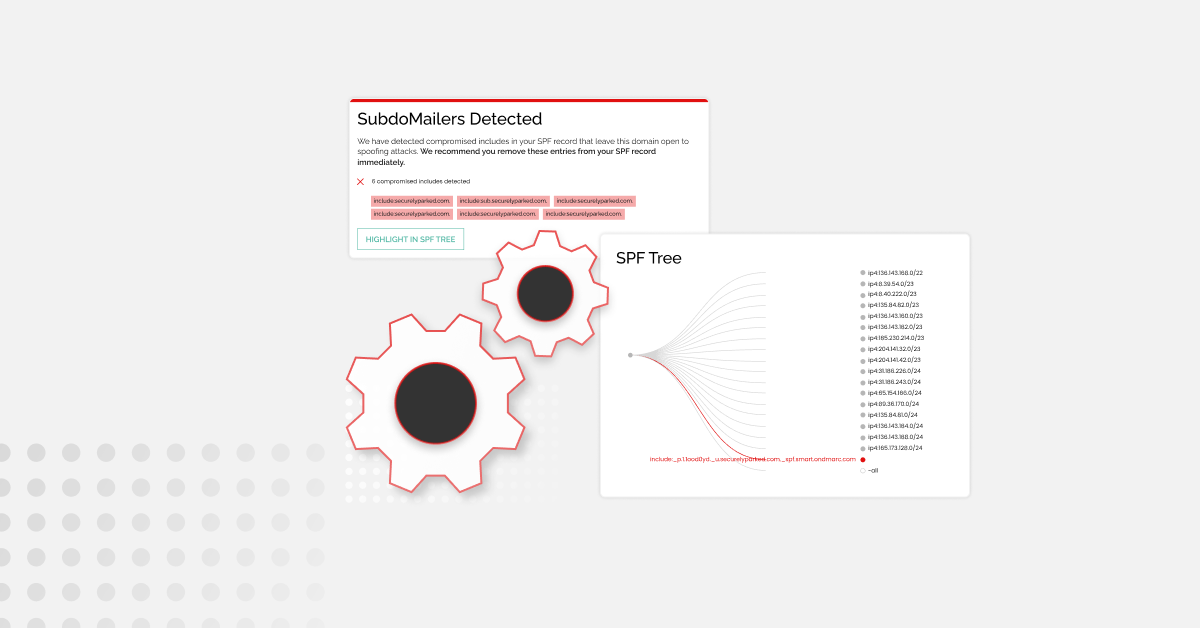
Knowing what’s going on across your email landscape is particularly valuable when you’re using third-party sending services and may not otherwise have direct control over the exact configuration. Indeed, it’s not uncommon for third-parties sending emails on behalf of their customers to suddenly stop DKIM signing emails, all because a small change has been made. Without the reporting functionality of OnDMARC you won’t know if and when this happens so you won’t be able to reach out to them for answers or have this corrected.
Add new email services
The ongoing reporting capability of DMARC has the added benefit of highlighting new legitimate (and illegitimate) sources of email. Once you’ve seen them pop up on the OnDMARC radar you can go ahead and either properly configure them with SPF and DKIM, or block them altogether.

- A common scenario is a department, such as Marketing, deciding to use a new application like Hubspot or Mailchimp, to manage email campaigns to customers.
- Unfortunately, IT and email teams aren’t always involved in these decisions, and so the new email sending application becomes part of an organizations’ “shadow IT”.

- The problem with sending emails “from the shadows” is that with your DMARC record in p=reject none of these emails will reach their intended recipients.
Of course, the moment you know about the new application you can help correctly configure it to maximize deliverability rates.
Building a futureproof email architecture
It’s inevitable that over time new domains and subdomains will be added, this is commonly known as domain creep, and eventually, most organizations end up with far more domains under DMARC control than they first imagined when they started their journey.
Our experience of thousands of DMARC deployments has taught us that most organizations will want to make use of dedicated domains or subdomains for individual business groups, perhaps even with different policies for these domains. There will also be parked domains, purchased to protect domains you own but do not send email from.
Being able to simply, and correctly, manage an ever-growing number of domains is vital because what your email landscape looks like today, isn’t an indication of what it will look like tomorrow.
To find out more about how OnDMARC helps make DMARC implementation simpler and easier, start your 14 day free trial or get in touch with us below today!