This early into 2024, the cybersecurity space is already buzzing with activity. Emerging standards, such as Google and Yahoo’s bulk sender requirements, mark a new era of compliance for businesses reliant on email communication. At the same time, the prevalence of sophisticated cyber threats, such as the SubdoMailing campaign, emphasizes the continual hurdles posed by bad actors getting around standards-based security measures.
In light of this, Red Sift’s 2024 Spring Release features innovations that help organizations better detect and remediate common misconfigurations and exposures while meeting the latest industry requirements.
Here’s an in-depth look at Red Sift’s latest releases.
Free tools that help meet evolving attack vectors and new requirements
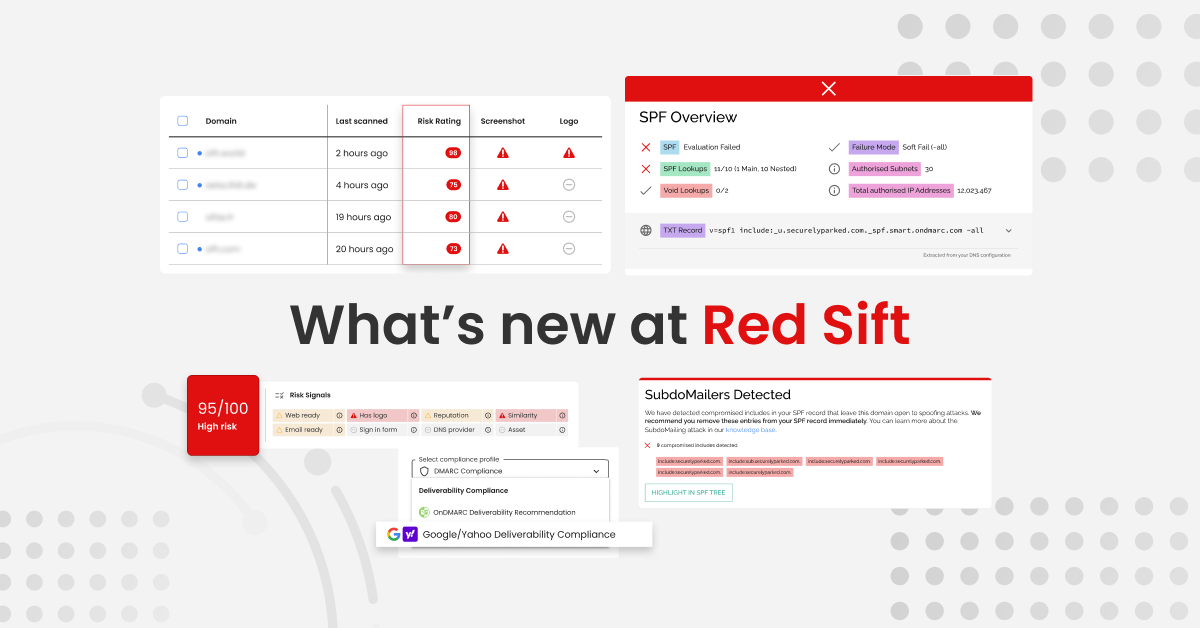
SubdoMailing Checker
In light of the recent SubdoMailing attack, Red Sift made updates to its free tools, Investigate and SPF Checker, within 48 hours of the news breaking. These updates empower users to quickly identify any domains utilized for SubdoMailing within their email environment.
Investigate surfaces a ‘SubdoMailers’ card to show if poisoned includes have been found. The same card was added to the SPF Checker, along with functionality that creates a dynamic visualization of the SPF tree. This allows users to easily pinpoint the location of any poisoned includes and remediate them quickly.
Google and Yahoo Compliance Checker
In response to Google and Yahoo’s bulk sending requirements, Red Sift introduced a version of its free email analysis tool, Investigate, that allows users to get instant insight into how their email-sending domain stacks up against these new requirements. The tool achieves this by dynamically checking a user’s email in less than 30 seconds.
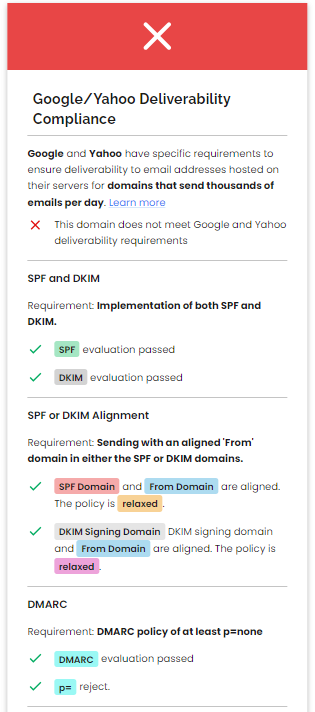
Red Sift Investigate is the only free tool on the market that provides this kind of real-time insight. It checks for the majority of requirements, namely:
- Implementation of both SPF + DKIM
- Sending with an aligned `From` domain in either the SPF or DKIM domains
- Sending from a domain with a DMARC policy of at least p=none
- Using a TLS connection for transmitting email
- Valid forward and reverse DNS (FCrDNS)
- One-click unsubscribe
- Low spam reported rate (Investigate does not check for this final requirement)
OnDMARC
Automated SubdoMailing alerting
Red Sift OnDMARC added first-class support for SubdoMailing detection to its hosted SPF solution, Dynamic SPF. It automatically surfaces if domains used for SubdoMailing are present prompting customers to quickly take remedial action.
SubdoMailing detection has also been added to the My Domains view, Investigate, and Domain Analyzer.
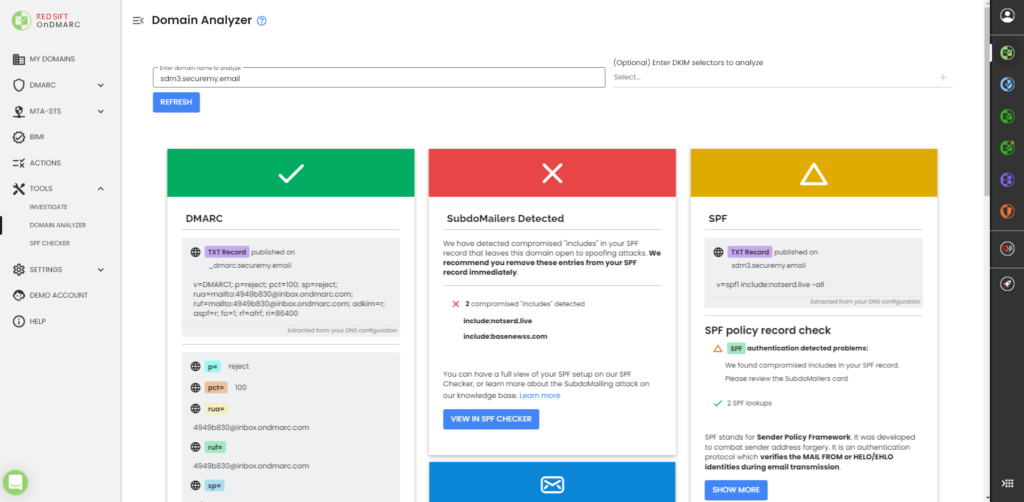
Google & Yahoo Bulk Sender’s Compliance Profile
OnDMARC customers can benefit from Investigate’s new Google and Yahoo compliance profile inside the application. This compliance profile quickly determines if an email-sending service is set up for bulk-sending success.
Overview Dashboard
Red Sift OnDMARC released an enhanced Overview Dashboard to facilitate informed decision-making and prioritization of actions.
To better support its large brands and their complex email-sending domain estates, OnDMARC’s enhanced Overview Dashboard now offers users a comprehensive view of their DMARC status across all active domains. This new and improved dashboard serves two purposes as it:
- Provides summary metrics for all active domains an organization has within OnDMARC, including:
- How many domains are at p=none, p=quarantine, and p=reject
- The total amount of emails sent across all domains
- How many domains have MTA-STS configured
- How many BIMI applications are in progress
2. Helps to identify domains that should be prioritized for DMARC policy advancement based on domains with high sending volume or consistently high DMARC compliance rates.
DNS Alerts
The DNS Alerts feature in OnDMARC has been upgraded with over 15 new alerts to provide users with comprehensive notifications regarding changes made within their DNS records. These enhancements enable users to promptly identify and mitigate potential risks. The new alerts cover various statuses, including missing, configured, updated, and delegated, across DMARC, SPF, and MX records.
Brand Trust
SubdoMailing Detection
Red Sift’s lookalike domain discovery application, Red Sift Brand Trust, periodically checks lookalikes against a new Red Sift threat intelligence feed and flags whether the lookalike domain is involved in a SubDomailer attack. If a SubdoMailer is detected, the risk score is increased to high risk, signaling a need for prioritized remediation to the end user.
A new column called SubDomailer has been added to the Activity table, enabling users to filter lookalikes that have been detected. When drilling down into the details page of a lookalike domain, the risk score section has also been updated to show whether a SubDomailer has been detected.
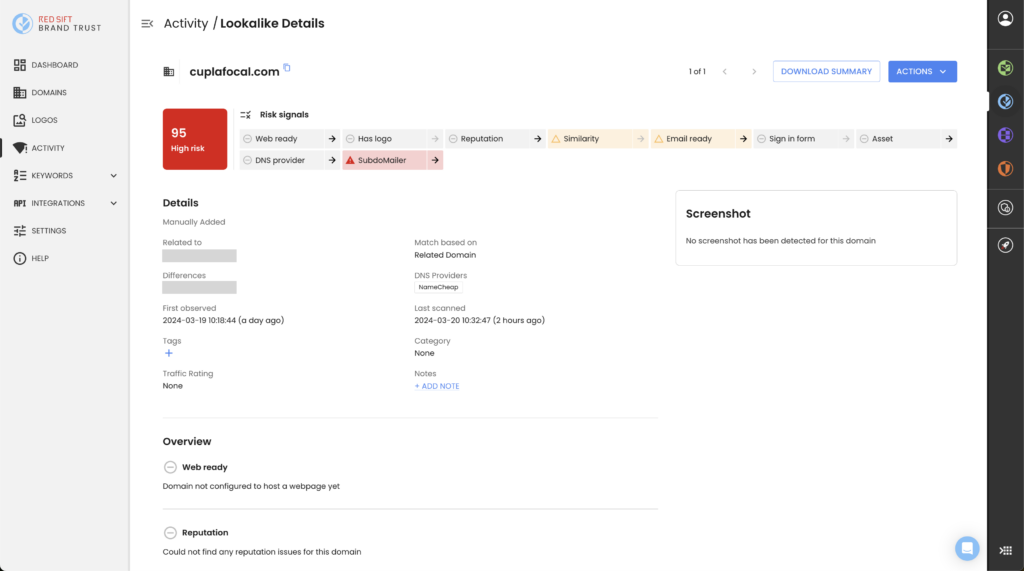
New and improved risk rating system
In addition to the above, Red Sift Brand Trust has improved its lookalike risk rating functionality by introducing new risk signals and updating its scoring system. This enhanced overview provides a quantifiable measure of the threat posed by lookalike domains, empowering users to triage threats in priority order, take action faster, and reduce overall noise in the system.
Each lookalike will receive a score between 0 and 100, depending on which risk signals are active and contributing to the score. The score is mapped to three risk buckets:
- High risk (71-100)
- Medium risk (37-70)
- Low risk (0-36)
The new risk rating now calculates how similar a lookalike domain looks to an owned asset, with closer resemblances being more heavily weighted. This rating is updated dynamically on each scan so users can confidently track the weaponization of domains in real time.
The risk rating is impacted by sign-in forms on web pages that could be used to harvest credentials – discovered thanks to AI computer vision – as well as the security rating of DNS providers.
In the coming months, the Brand Trust team plans to add more signals such as HTML analysis of a web page and the most abused registrars, both of which could increase the risk score.
Visual enhancements to lookalike & domain details pages
In conjunction with the new risk rating, Brand Trust’s lookalike details and domain details pages have been revamped to make it easier than ever to see important information at a glance.
A new risk section at the top of every lookalike details page shows which risk signals are contributing to the risk rating, demystifying how we’re scoring each lookalike domain.
Brand Trust uses numerous AI computer vision algorithms to scan screenshots gathered from domains. With the screenshot now located prominently above the fold, it’s clear to see which signals have been detected on a page (logo, detected keywords, sign-in forms, page type, etc).
In addition, we’ve introduced a concept similar to email – users can now clearly see when new lookalikes have arrived in Brand Trust, marked by the bolded text and blue circle next to it. Clicking on one of these domains marks the lookalike as read, so users can keep track of what they’ve triaged. Just like email, lookalikes can be marked as unread and revisited later.
Red Sift ASM
Web Technologies
Ensuring compliance with frameworks and regulations like NIST, NIS2, HIPAA, and PCI-DSS necessitates maintaining an inventory of software utilized for service delivery. Red Sift ASM addresses this need by automatically compiling and updating a comprehensive inventory of a customer’s domains, hosts, certificates, IP addresses, and cloud resources. With the launch of Red Sift ASM’s latest feature, Web Technologies, users gain deeper insights into the technologies running in their environments, thus enhancing their understanding of the services across their digital infrastructure.
The new Web Technologies feature in Red Sift ASM offers a range of benefits:
- Facilitates precise identification of potential risks within your estate, simplifying the management of both existing vulnerabilities and those arising from new threats.
- Enhances compliance adherence by providing in-depth visibility into the technologies used.
- Supports a Continuous Threat Exposure Management (CTEM) program as knowing what technologies are used across the attack surface is a critical part of identifying exposure as part of the scoping stage.
During the assessment process within Red Sift ASM, if HTTP or HTTPS is detected on a host, its headless browser automatically identifies and displays the web page, along with the technologies, libraries, and third-party services utilized. It identifies technologies across over 100 different categories. Any discovered technology will be displayed on the host assessment and will also appear in the downloadable PDF assessment.
Red Sift customers who had early access to this feature described it as a “beautiful way to triage and prioritize an issue with an asset. It gives us more information than our existing tools do in a single place.”
Oracle Cloud Infrastructure integration
Having comprehensive data readily available facilitates making informed decisions – a key requirement in cyber. So, as part of Red Sift ASM’s ongoing cloud integration enhancements, Oracle Cloud Infrastructure (OCI) has now been integrated into its platform. This integration enables customers to seamlessly import new domain names, DNS zones, and their associated name records. Moreover, it empowers them to effortlessly support their cloud resources daily, all without requiring manual intervention.