In the world of cybersecurity, a new threat has emerged. Known as “SubdoMailing,” this new attack cunningly bypasses some of the safeguards that DMARC sets up to protect email integrity.
In this blog we will focus on how the strategic investments we have made at Red Sift allowed us to discover and protect against this attack rapidly. We will break down how we were able to identify this attack in customer environments and make sure all of our customers were protected within 48 hours of the attack being widely reported.
While we will cover some details on the attack here, if you are looking for all the details on how this attack works, check out our SubdoMailing guide.
Identifying early instances of SubdoMailing with our customers
A couple of weeks before the SubdoMailing attack was surfaced by Guardio Labs, we discovered what we thought was an isolated incident of bad senders passing SPF checks and sending emails fraudulently on behalf of one of our customers.
In a customer instance of Red Sift OnDMARC, we noticed mail was coming from a sender with a poor reputation and a subdomain that appeared unrelated to our customer’s main domain. This subdomain had a CNAME and pointed to an SPF record authorizing services we had never seen. Upon investigating the includes and IPs, it all looked suspicious.
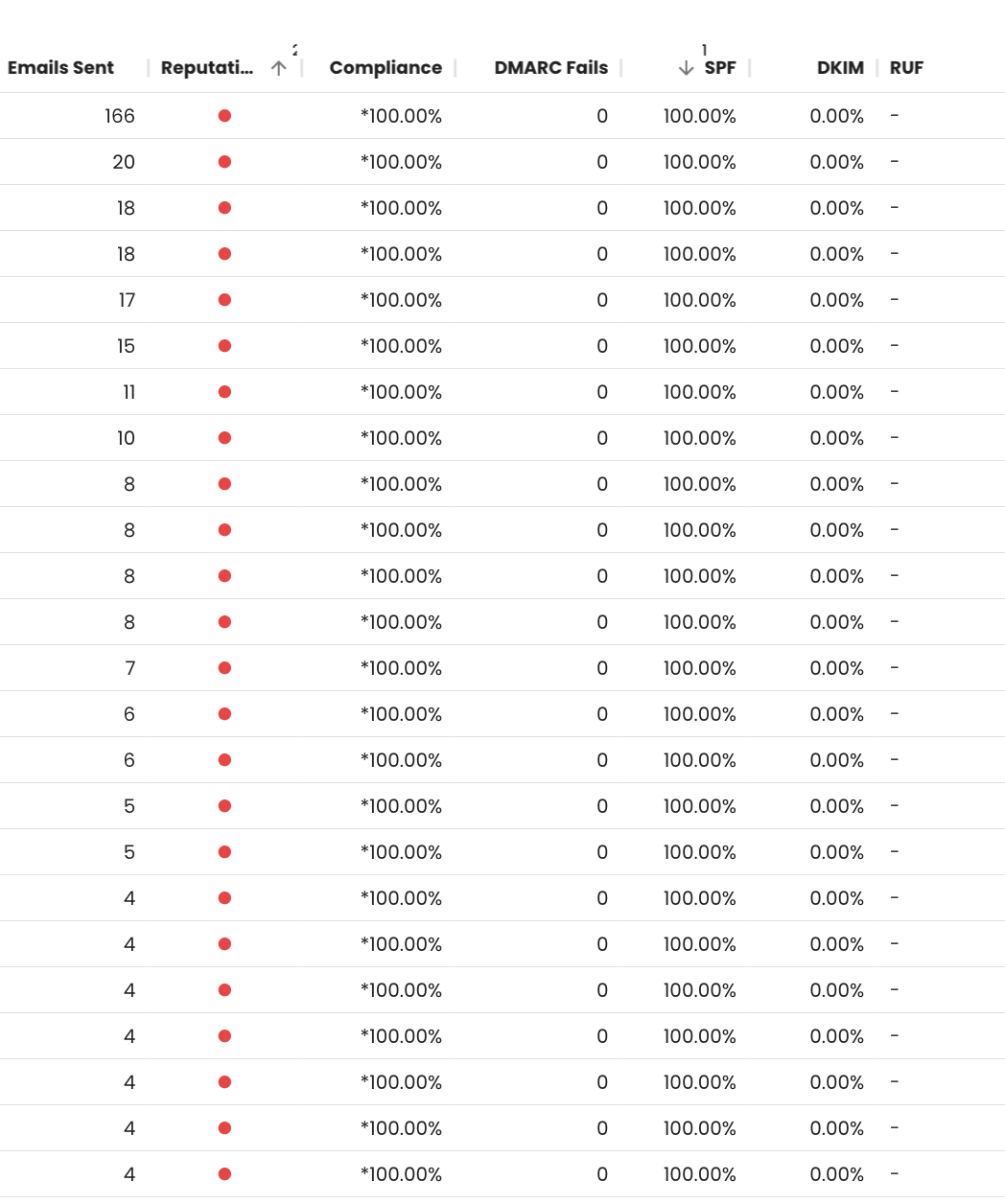
Examples of emails being sent on behalf of our customer with a bad reputation but fully passing SPF
We notified our customer and asked the team to double-check that the subdomain sending mail was legitimate. The customer confirmed it was not, and deleted the subdomain.
We began to work on automated ways to identify instances like these where DMARC and SPF were configured correctly, but someone had capitalized on stale, forgotten or misconfigured records that were wrongfully included in the DNS to send spam. We recognized that this approach could be exploited more widely as it capitalized on poor hygiene of DNS records.
The discovery of a widespread “SubdoMailing” campaign
After this first example, we saw a handful of additional instances of what we began referring to as “poisoned” SPF records appearing in customer DNS. But, the true scale of what we were up against was made clear when Guardio Labs published their findings on SubdoMailing.
Following Guardio’s findings we realized that we were uniquely positioned to understand the far-reaching nature of this attack due to applications, our investment in cybersecurity intelligence data, and the security expertise we employ across our organization. We had to move with urgency to make sure that our customers were protected.
Understanding the scale of SubdoMailing
At Red Sift, we realize the days of deploying a patch to protect from a security attack are mostly behind us. Our customers are trading vulnerability management for exposure management – they are continuously evaluating the visibility and security status of their entire digital estate across patchable and non-patchable attack vectors. As seen in the case of SubdoMailing, once discrete threats are becoming more interconnected.
To make sure our customers have the information they need, we’ve been investing in feeds of cybersecurity intelligence signals – like passive DNS feeds, private data channels with key providers, real-time spam trap feeds, IP level threat and reputation information and ASN Metadata. We furthered this with our strategic acquisition of Hardenize.
This became the foundation of understanding the customer impact of SubdoMailing.
Seeding discovery with CNAME takeovers and poisoned SPF includes
Guardio reported that bad actors had leveraged dangling CNAME records and SPF include statements to be able to send fraudulent emails on behalf of legitimate brands. This was consistent with our own findings as well.
What is a CNAME takeover?
The first step for the attackers to send on behalf of someone else involved examining the DNS records to find instances where one domain was linked to another via the CNAME record. If a subdomain that was referenced in the DNS was abandoned, the bad actors reregistered it to be able to inherit the DMARC policy of the root domain and combine it with their own email farm.
As an example, in our own customer base, we have come across this with CNAME records that point to abandoned Marketo hosts.
go2.{customerdomain}.com CNAME mkto-lon123456.com
What is a poisoned SPF include?
Once the CNAME takeover was complete, the attackers added domains that had been forgotten or taken over to SPF records by manipulating the include statements.
One example that we were particularly fond of was surfaced by Guardio Labs. In the SPF policy for msnmarthastewartsweeps.com was the following:
v=spf1 include:harrisburgjetcenter.com include:greaterversatile.com -all
This means that senders in the harrisburgjetcenter.com SPF are now authorized to send on behalf of msnmarthastewartsweeps.com and perhaps more significantly on behalf of marthastewart.msn.com.
(Please note that as of March 12, 2024, harrisburgjetcenter.com and greaterversatile.com have been taken down.)
Identifying other poisoned SPF includes
Using suspicious includes we had seen internally in customer environments and examples surfaced by Guardio like harrisburgjetcenter.com, we began to compile a list of domains that we suspected had been weaponized to send fraudulent mail.
We were able to build this list further by analyzing our own data feed that examines 70 million apex domains every day. Part of this data feed includes SPF discovery which we typically use to discover legitimate sending services. But in this instance, we realized that we could use this to discover likely fraudulent sending services.
By combining these signals with domain registration data and passive DNS feeds, we began to identify patterns that indicated a domain was being used for SubdoMailing. By visualizing DNS changes over time for specific domains, we can begin to see when anomalous behavior starts to appear and domains are therefore hijacked.
Take the example of greaterversatile.com (a poisoned SPF domain flagged by Guardio). We can see very normal changes over time, with TXT records happening occasionally in the lead up to the SubdoMailing campaign – represented by blue dots. However, in late 2023 and early 2024 we see a flurry of activity where the NS is changed – represented by the pink dot – and an overwhelming number of TXT changes that would rarely happen in a legitimate circumstance.

Looking for patterns like these allowed us to validate that our hypotheses for hijacked subdomains were correct. We can take one of our suspected bad domains and look for anomalous DNS activity like with jacksonbox.com.

This was the foundation of our ‘known bad list’ – which encompasses the core domains used for SubdoMailing. As we continue to dig into this data further, our list grows every day.
Identifying impacted customers
Once we had our ‘known bad list’ of domains, we were able to use Red Sift ASM to programmatically examine the SPF records for all of our customers to see if any of their SPF includes were poisoned.
We discovered organizations of all sizes, regions and markets that were impacted and quickly got to work notifying and remediating. We had communicated with all impacted customers within 24 hours of the initial Guardio report being published. We then worked hand in hand to help impacted customers remove the records within 48 hours following the published report.
Where to go if you need help
Red Sift Investigate & Red Sift SPF Checker
If you are wondering if you have been impacted by SubdoMailing, the best place to start is Red Sift Investigate. Should Investigate reveal any ‘SubdoMailers’ – also known as poisoned includes – the Red Sift SPF Checker allows you to visualize them in a dynamic ‘SPF tree’, allowing you to quickly pinpoint where they are and speed up remediation efforts.
We have distilled all of our findings from our ‘known bad list’ so that any domain in the world can be checked to see if their SPF includes are poisoned. We are continuously working on expanding the list – it has grown 500% in one week and we are finding more domains every day.
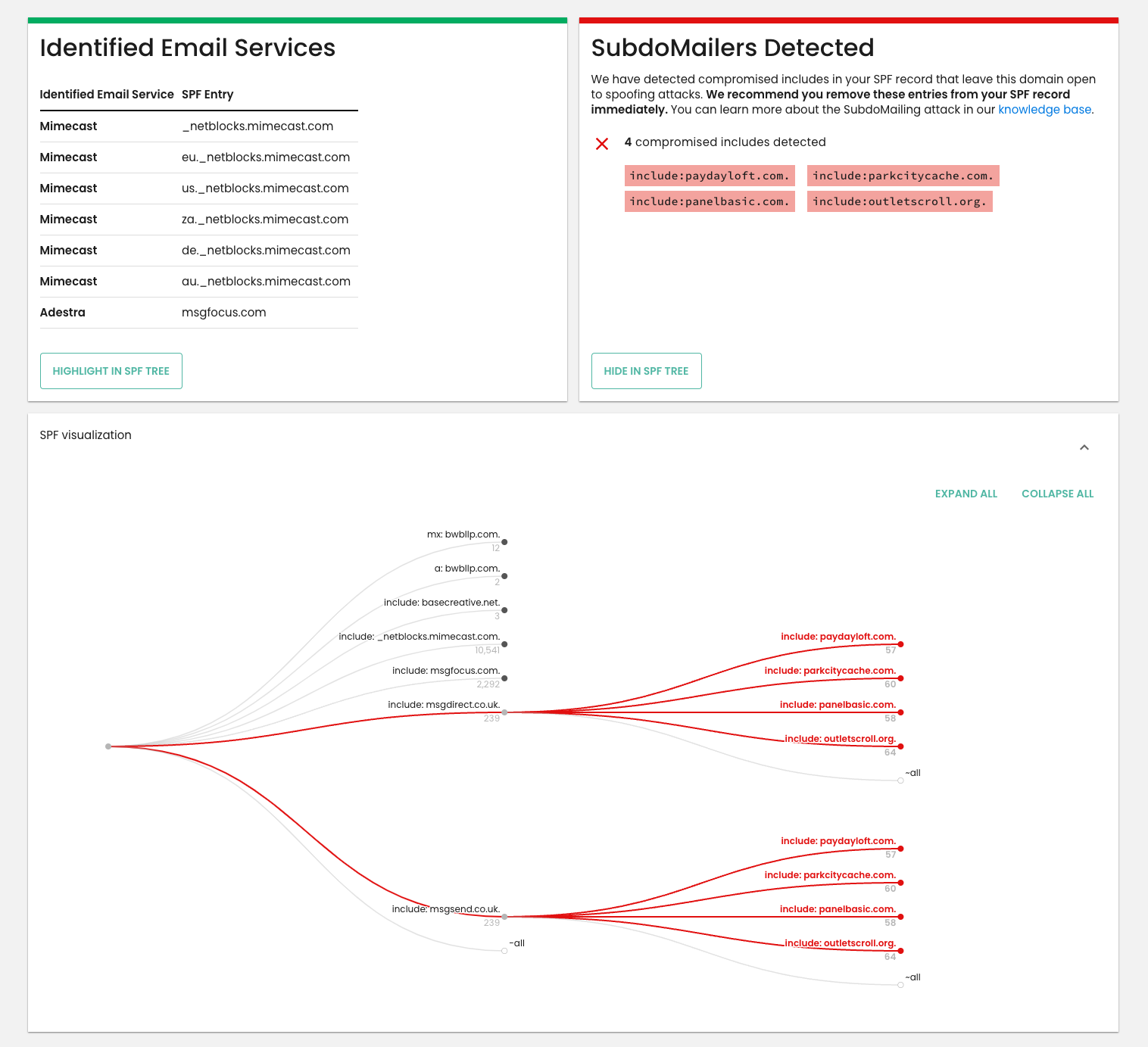
Red Sift OnDMARC
For Red Sift customers, our teams have been working furiously to roll out SubdoMailing protection capabilities. We are thrilled to say these are live for our customers and will automatically surface if any domains used for SubdoMailing are present in your DMARC environment.
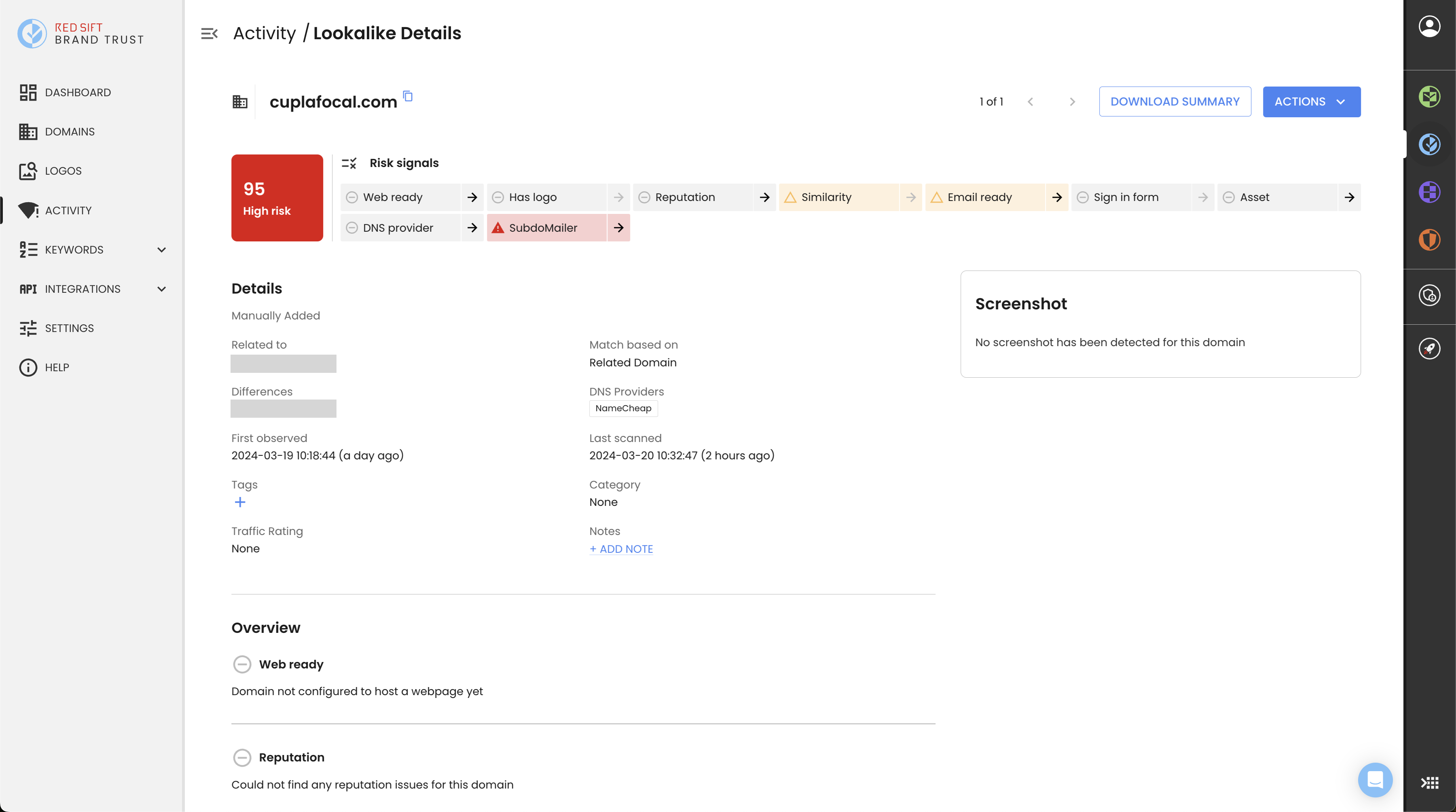
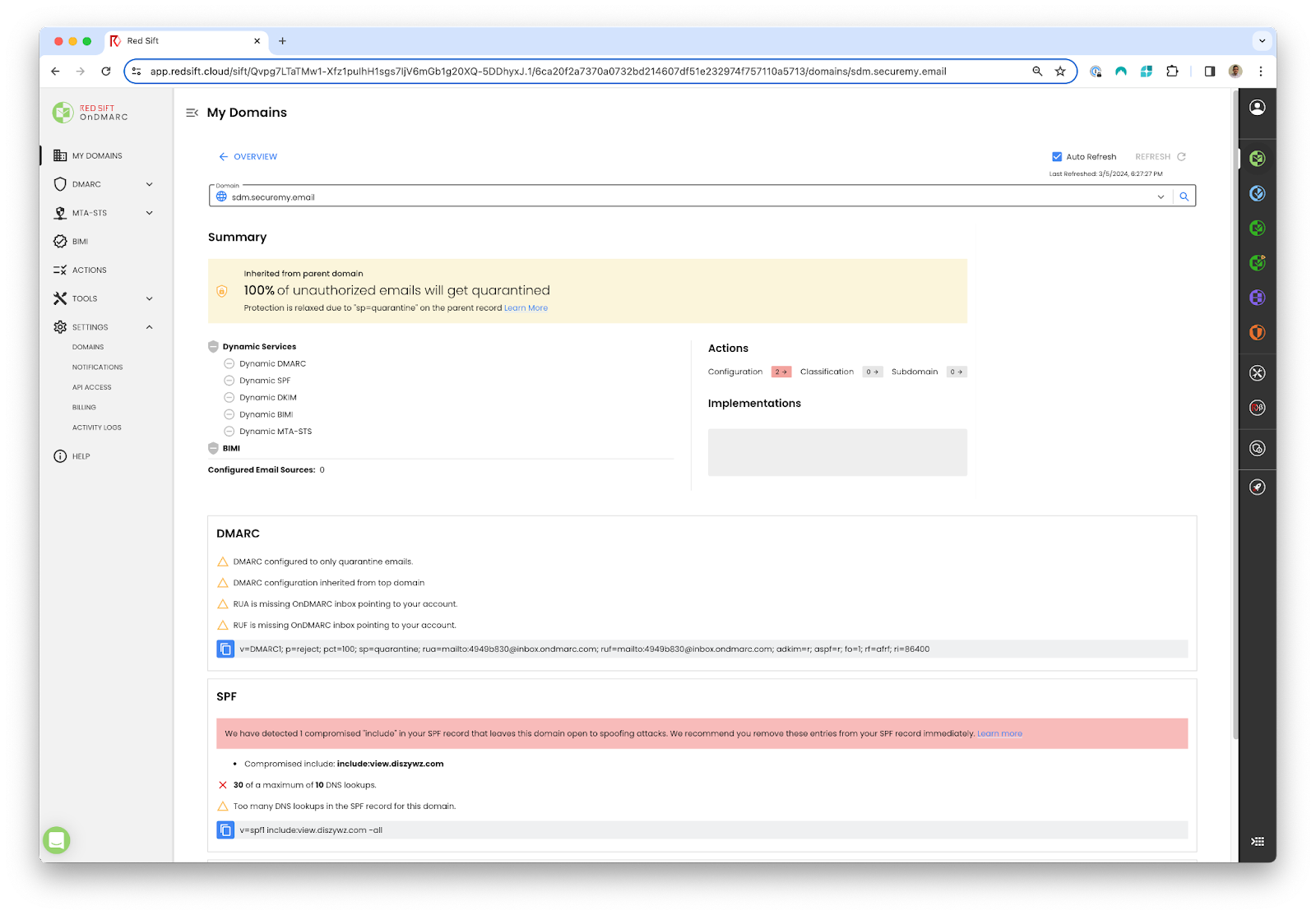
Red Sift ASM
And for those businesses that want to be more proactive in monitoring their domains and subdomains to prevent this pattern of attack in the future, make sure to check out Red Sift ASM. Red Sift ASM performs the key checks needed to prevent similar threats to SubdoMailing—domain name expiration monitoring so that you don’t lose control of your domains and finding dangling records and services so that you can clean your DNS. Asset discovery and monitoring is often in real-time, giving your team important knowledge when it’s needed—not in days, weeks, or months.
To learn more about SubdoMailing and how Red Sift discovered and protected its customers against the attack, sign up for the on-demand live briefing below.