In response to the ever-evolving challenges posed by spam, phishing, and email-based fraud, email service giants Google and Yahoo are set to implement significant changes for bulk senders (businesses that send 5,000+ emails a day) from February 1, 2024. The changes center around bolstering email authentication protocols, ensuring low spam rates, and making it easy for recipients to unsubscribe from promotional mail.
The driving force behind these new policies is a collective commitment to make inboxes safer and less spammy. Through their united stance, Google and Yahoo are signaling that email security is no longer a nice to have. And so, for bulk senders who rely on business email communications and can’t afford to have their deliverability severely impacted, the email security standards once deemed best practice will soon become a mandated reality. Those who fail to meet these requirements will see Google and Yahoo limiting sending rates or marking legitimate messages as spam.
Whether you’re a marketer, an IT professional, or a small business owner who sends more than or around 5,000 emails a day to Gmail and/or Yahoo inboxes, this article will help you understand the upcoming requirements, their benefits, and provide guidance on how you can get ready for February 2024.
| 📣 Google has now extended its original timeline for enforcement from April to June 2024, giving senders more time to action the requirements and avoid their messages being blocked. 📣 |
What are the requirements?
The requirements cover three core areas. In the table below, we’ll break down each area and its specific requirements (including sub-requirements), starting with the meatiest, most time-consuming requirement – email authentication.
Please note that these requirements will need to be put in place for every sending service and/or platform you send mail from – more on that below.
| Requirement | Explanation | Benefit | Enforcement timeline |
| Email authentication | |||
| Set up SPF and DKIM for each domain that sends mail | SPF and DKIM are two email security protocols. You will need to define records for each protocol and add them to your DNS or the platform you use that hosts SPF and DKIM for your domain. SPF validates the sender’s IP address and DKIM ensures the integrity of the message. Together with the protocol DMARC (another requirement explained further down), these protocols stop your domain from being impersonated. | Improves email integrity and sender verification. | Gradual enforcement from Feb 2024 with error codes on non-compliant email traffic. From April 2024, increased rejection rate for non-compliant email traffic. Read more on Google’s enforcement timelines here. It is assumed that Yahoo will align with Google’s decisions. |
| Send with an aligned `From` domain in either the SPF or DKIM domains | SPF and DKIM alignment ensures that the sender’s domain specified in the “From” address aligns with the domains authorized by SPF records and covered by DKIM signatures, respectively. Google and Yahoo will require either SPF or DKIM alignment. Without it, DMARC will not pass. It is therefore essential that at least one of the underlying protocols passes and aligns. Google/Yahoo will permit relaxed alignment, which means that the domains in either SPF or DKIM can be subdomains of the From domain. | Without having achieved alignment, you are risking your emails ending up in spam rather than in the inbox of the recipient. Also, if you achieve alignment across your email-sending services, you will be ready to protect your domain and reach a DMARC policy of reject. | |
| Publish a DMARC policy for each domain that sends mail with at least a policy of “none” | DMARC is another email security protocol. Together with SPF and DKIM, it protects your domain from exact email impersonation. You will need to set up a DMARC record in a policy of none. This is the first step in a DMARC project – you should eventually progress to a policy of reject for full protection. As of Dec 21, 2023, Yahoo has said “including a “rua” tag, which is properly set up to receive reports, is strongly recommended to allow monitoring during initial setup”. | Once a policy of reject has been reached, DMARC helps block exact domain impersonation attacks thus protecting your employees, customers and partners from malicious emails being sent on your behalf. | |
| Ensure that sending domains or IPs have FcrDNS set up | FCrDNS stands for Forward Confirmed Reverse DNS. It is used to show the relationship between an IP address and domain name. FCrDNS is set up by both the domain and IP owner respectively. If you don’t own the IP address, you may need to contact your hosting service provider or ISP to set up the reverse DNS. | Helps with email deliverability. Without FCrDNS, certain mailbox providers may block or deliver mail to spam. | |
| Use a TLS connection for transmitting email | TLS encrypts the communications between two points (the sender and the recipient) to ensure messages cannot be read in transit. | Prevents fraudsters from snooping on your emails. | |
| One-click unsubscribe | |||
| Enable one-click unsubscribe for recipients of promotional mail | Make it easy for your recipients to opt out of receiving your emails with a one-click unsubscribe link and ensure this is processed within 2 days. | Decreases chances of being marked as spam (and improves chances of landing in the inbox) thus having a positive impact on spam rates – the final Google and Yahoo requirement! | June 1, 2024 (for more details on specifics, read the Google policy enforcement timeline) |
| Low spam rates | |||
| Keep spam rates under 0.10% | Google and Yahoo recommend keeping spam rates below 0.1%. You should avoid ever reaching 0.3%. To check your rates, consult Google’s Postmaster Tools or Yahoo’s Complaint Feedback Loop program. | Improves sender reputation and deliverability rates | Feb 1, 2024 |
Google’s new temporary error codes
SMTP (Simple Mail Transfer Protocol) error codes are three-digit codes that are returned by mail servers to indicate the status of an email delivery attempt. These codes help in diagnosing email delivery issues by providing information about why a message was not delivered successfully.
If you’re not yet meeting the new bulk sender requirements, chances are you will have seen these new codes and may be wondering what they mean. These error codes signal that your unauthenticated mail has been temporarily rejected and help you identify and remediate domain-related issues.
Though Google has not yet updated its SMTP errors and codes article yet, we are aware that the following 421 error codes are now in existence:
- SPF and DKIM both failed:
421-4.7.26 This mail has been rate limited because it is unauthenticated. Gmail 421-4.7.26 requires all senders to authenticate with either SPF or DKIM.
421-4.7.26
421-4.7.26 Authentication results:
421-4.7.26 DKIM = did not pass
421-4.7.26 SPF [redacted] with ip: [redacted] = did not pass
421-4.7.26
421-4.7.26 For instructions on setting up authentication, go to
421 4.7.26 https://support.google.com/mail/answer/81126#authentication [redacted] - gsmtp (in reply to end of DATA command))2. The message was sent by a bulk sender whose setup failed DKIM:
421 4.7.30 This mail has been rate limited because DKIM does not pass. Gmail requires all large senders to authenticate with DKIM. Authentication results: DKIM = did not pass3. The message might have passed SPF and/or DKIM, but neither was in alignment with the visible From domain, as required by DMARC:
421 4.7.32 This mail has been rate-limited because there is no DMARC alignmentIf you are seeing these messages, we recommend you look into remediating these errors as soon as possible to avoid your mail being blocked when requirements are enforced in June.
Help! Where are Google and Yahoo’s requirements configured?
In the table below, we break out which requirements are configured at the email service provider (ESP) level (Hubspot, MailChimp, etc) and/or at the domain level. This will help you figure out where you need to action each requirement.
It is important to note that if your organization uses multiple ESPs, you will need to configure these items in each platform. The same is true for the use of multiple domains.
Requirement | Configured at | |
| ESP/Platform level | DNS | |
| Implementation of both SPF and DKIM | Yes | Yes |
| Sending with an aligned `From` domain in either the SPF or DKIM domains | Yes | Yes |
| Sending from a domain with a DMARC policy of at least p=none (including a RUA tag, as recommended by Yahoo*) | No | Yes |
| Using a TLS connection for transmitting email (added as a requirement in December 2023) | Yes | No |
| Valid forward and reverse DNS (FCrDNS) | Yes | Yes |
| One-click unsubscribe (RFC 8058) | Yes | No |
| Low spam reported rate | Yes** | No |
*Though the inclusion of the RUA tag is currently only recommended and not mandated by Yahoo, we strongly agree with their stance. The RUA tag specifies where DMARC aggregate reports should be sent which provide a daily overview of a domain’s email traffic. These reports provide crucial insight into your SPF, DKIM, and DMARC authentication status as well as where your domain is being used, which makes it easy to find mail currently not meeting authentication requirements.
**While a low spam rate is under the control of the sender, the mail originates at the ESP level. If for example, you use Salesforce Marketing Cloud for marketing mail and SendGrid for transactional with Mailgun as a backup, your overall spam complaint rate regardless of the sending platform(s) needs to be below the 0.3% threshold.
Who is impacted by these changes?
As of Jan 3, 2024, Google’s Email Sender Guidelines state that the requirements apply to businesses sending emails to any personal Gmail inbox, so an “account that ends in @gmail.com or @googlemail.com”. They further clarify that “the requirements don’t apply to Google Workspace inbound and intra-domain messages.”
Yahoo’s ruling applies to “all domains and consumer email brands hosted by Yahoo Mail”.
How Red Sift can help you get ready
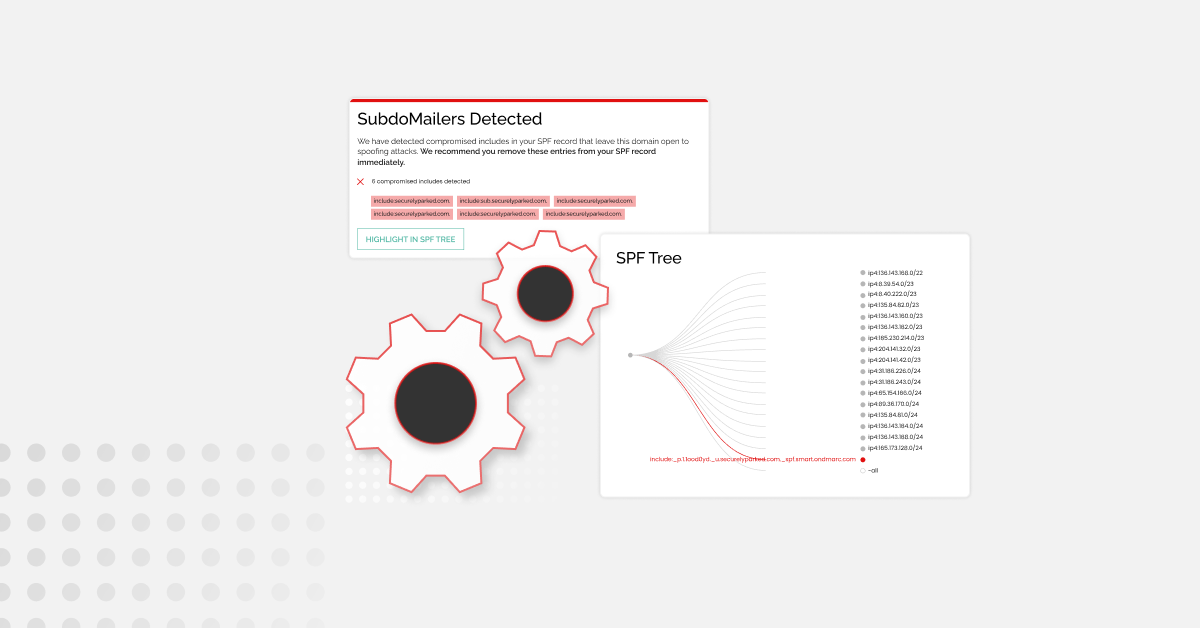
If you want an easy way to make sure your email-sending domains are ready come February 1, 2024, Red Sift makes it easy.
In under a minute, our free Investigate tool checks how you stack up against Google and Yahoo’s requirements and provides a visual breakdown of exactly what you need to action.
| All that is required to get going with Red Sift Investigate is for users to send an email to a test inbox. Check your readiness now |
We’ve got a dedicated webpage that explains how Investigate works, explanations of the checks it performs, and a link to the tool. Visit the page to get started now!