Alex Jenkins explains how both OnDMARC and OnINBOX can work in harmony to close the net on the phishing problem with 360° email protection for any size organization.

Alex Jenkins explains how both OnDMARC and OnINBOX can work in harmony to close the net on the phishing problem with 360° email protection for any size organization.

TLS is one of the most widely adopted security protocols in the world allowing for unprecedented levels of commerce across the internet. At the core of the TLS protocol is TLS certificates. Organizations must deploy TLS certificates and corresponding private keys to their systems to provide them with unique identities that can be reliably…
Read more
According to Gartner, Attack Surface Management (ASM) refers to the “processes, technology and managed services deployed to discover internet-facing enterprise assets and systems and associated exposures which include misconfigured public cloud services and servers.” This broad category of tooling is used within Continuous Threat Exposure Management (CTEM) programs, with many vendors within it having…
Read more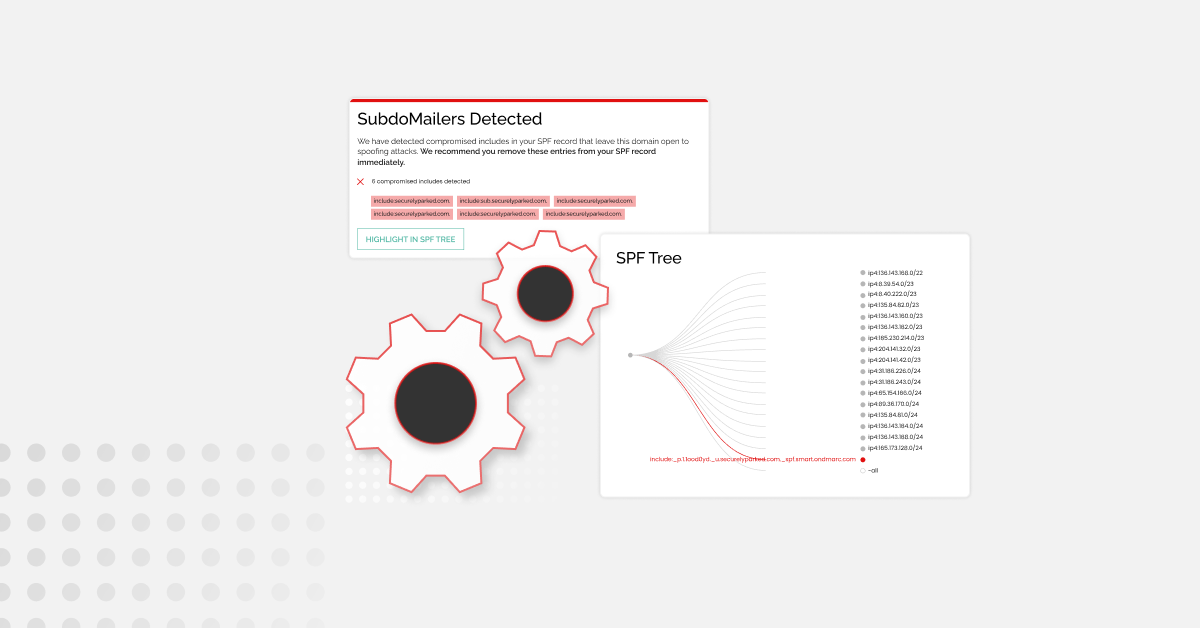
In late February 2024, ‘SubdoMailing’ became a trending search term overnight. Research by Guardio Labs uncovered a massive-scale phishing campaign that had been going on since at least 2022. At the time of reporting, the campaign had sent 5 million emails a day from more than 8,000 compromised domains and 13,000 subdomains with several…
Read more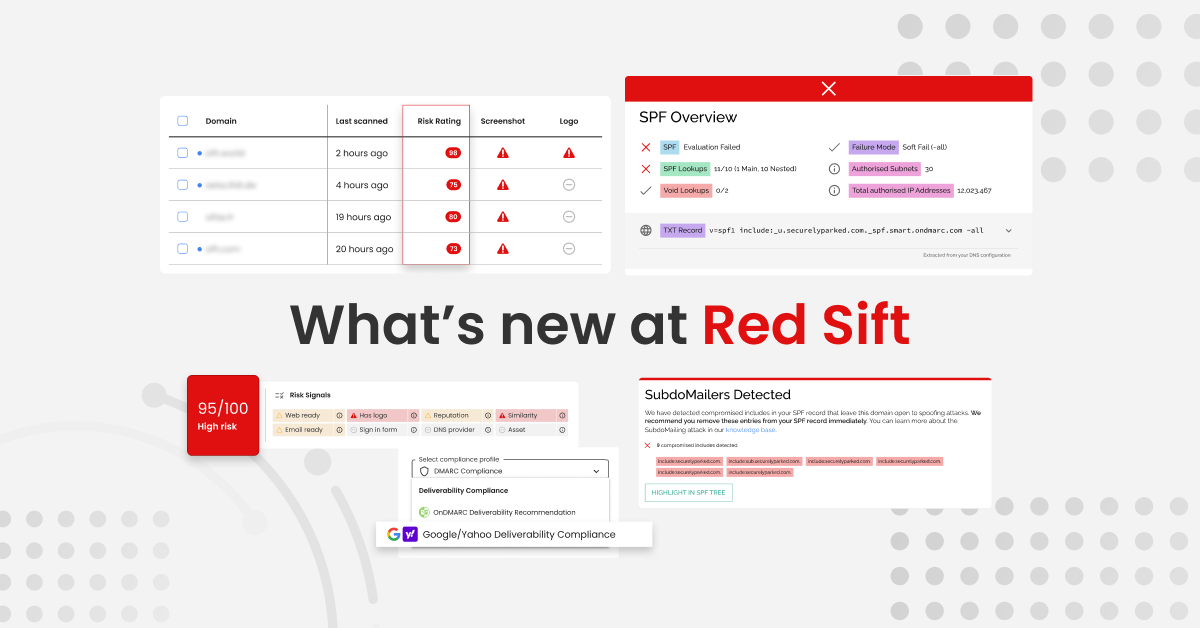
This early into 2024, the cybersecurity space is already buzzing with activity. Emerging standards, such as Google and Yahoo’s bulk sender requirements, mark a new era of compliance for businesses reliant on email communication. At the same time, the prevalence of sophisticated cyber threats, such as the SubdoMailing campaign, emphasizes the continual hurdles posed…
Read more