Attack Surface Management or ASM is an emerging priority for IT-driven businesses aiming to complement their existing security testing and monitoring. It’s the process of continuous asset discovery, inventory, classification, and monitoring of a company’s technical architecture…Continue Reading: What is an Attack Surface? Understanding Attack Surface Management (ASM) and Monitoring
Archives for 2023
What is Typosquatting? Everything you need to know and how to prevent it
A social engineering tactic that targets internet users who unintentionally type incorrect URLs into their web browsers, we discuss how best to protect against the threat…Continue Reading: What is Typosquatting? Everything you need to know and how to prevent it
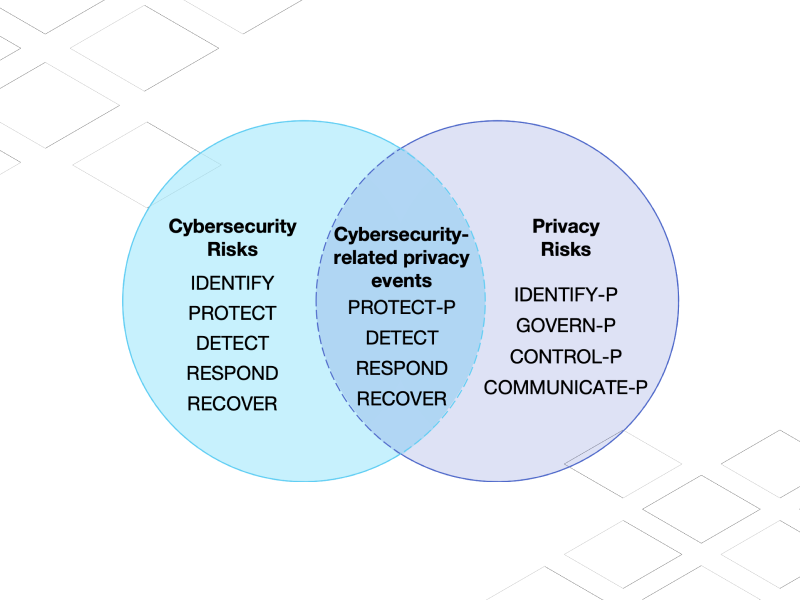
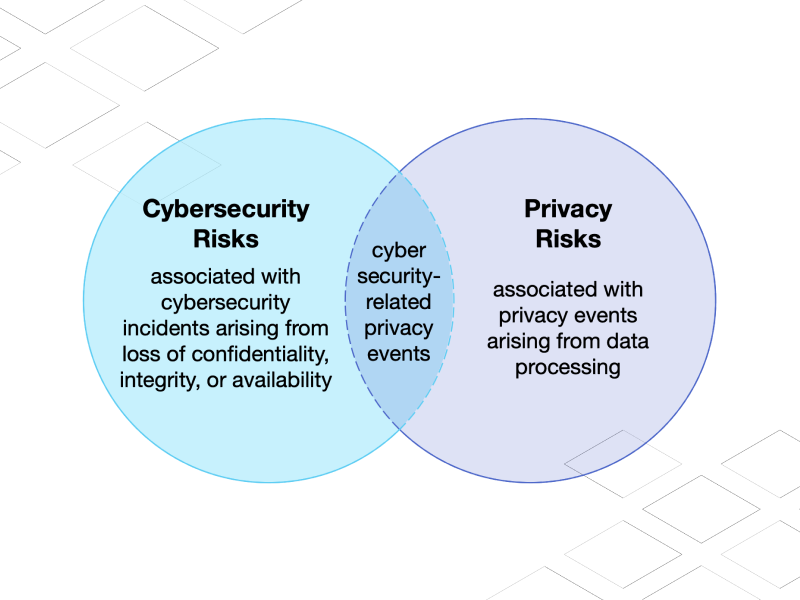
The Data Must Flow (Part 2)
We take a serious look at new privacy regulations, data frameworks, and the return on investment for cybersecurity compliance…Continue Reading: The Data Must Flow (Part 2)
Award: Red Sift named a “Top 100 Cybersecurity Company”
Red Sift’s Digital Resilience Platform, which helps organizations see, solve, and secure vulnerabilities across their email, domain, and web attack surfaces, has again been named a Top 100 Cybersecurity Company for 2023 by Fin Tech Global…Continue Reading: Award: Red Sift named a “Top 100 Cybersecurity Company”
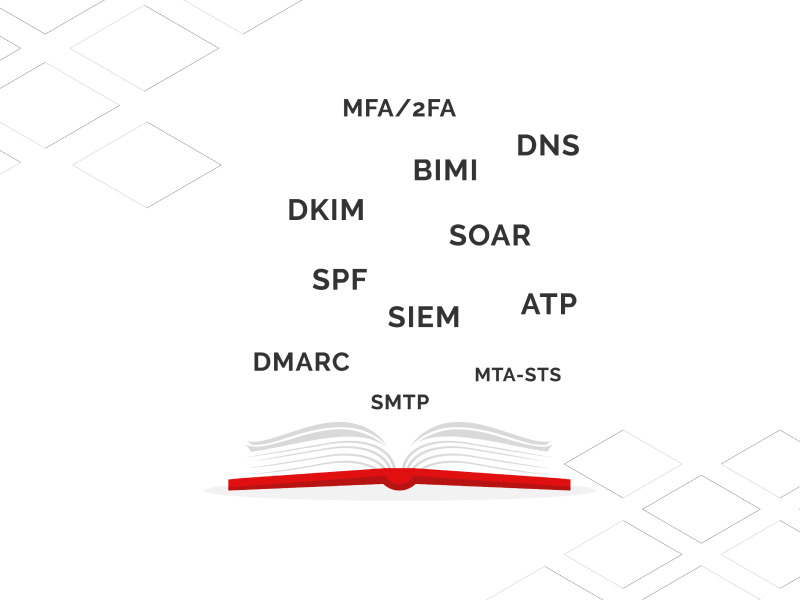
Your quick guide to email security acronyms: SMTP, MX Records, DNS, DMARC, and more
Email security is crucial to shield your business reputation, and you must deploy the necessary measures to stay abreast of cybercriminals. This extensive domain guide contains many terms that you may need an understanding of…Continue Reading: Your quick guide to email security acronyms: SMTP, MX Records, DNS, DMARC, and more
The data must flow (Part 1)
Today, cybersecurity concerns touch most every aspect of business operations as companies and governments have deployed substantial digital assets and vulnerabilities abound…Continue Reading: The data must flow (Part 1)