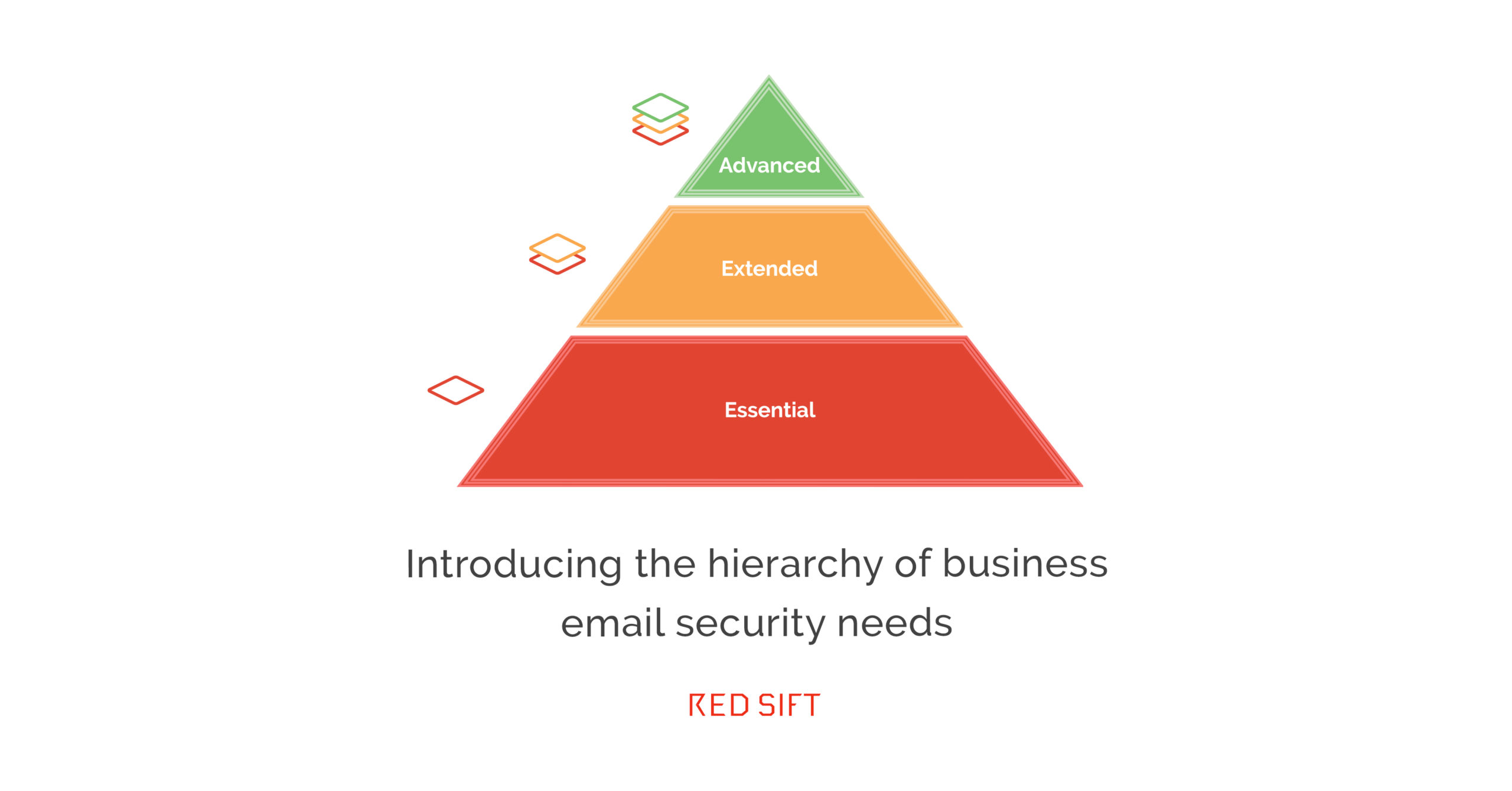
There’s a whole range of email security practices, products, and protocols out there, and it can be difficult to know exactly what’s needed for your business’ email security posture. So, we’ve put together this hierarchy highlighting what measures are essential, what’s extended, and what’s advanced. …Continue Reading: Introducing the Hierarchy of Business Email Security Needs