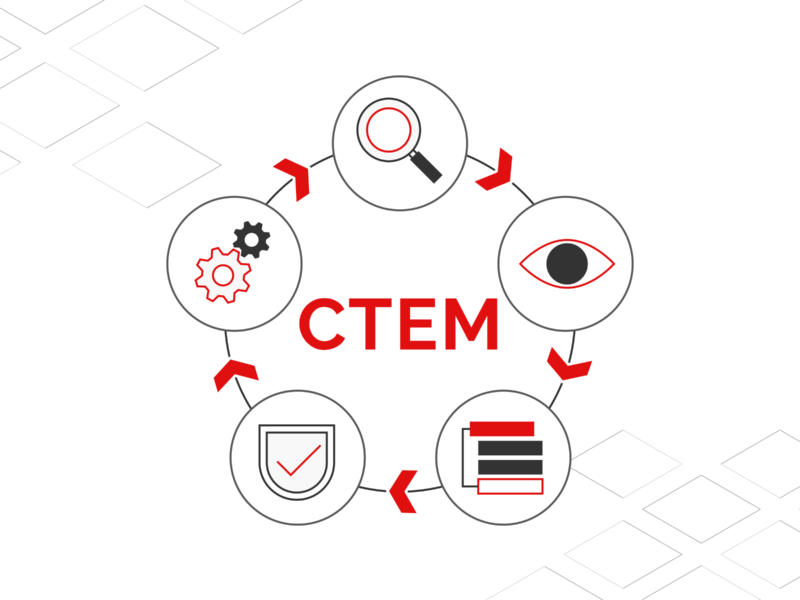
CTEM is a strategic approach to cybersecurity that incorporates constant, real-time monitoring and management of an organization’s vulnerability to threats. It is a kind of security technique that seeks potential flaws and threats before hackers can exploit them, rather than relying solely on reactive measures like firewalls and antivirus software…Continue Reading: What is Continuous Threat Exposure Management (CTEM) and why should you care?
Archives for June 2023
The transformative power of automation and generative AI
With the rise of complex cyberattacks and a staffing shortage, cybersecurity is set to reap the rewards of AI and automation. Today’s cybersecurity leaders are already implementing AI to build more scalable programs…Continue Reading: The transformative power of automation and generative AI
OnDMARC Named DMARC Leader in G2’s Summer 2023 Report
We’re excited to announce that Red Sift OnDMARC has shone in G2’s quarterly reports. This Summer 2023, our highly acclaimed DMARC application has been named in 5 reports and earned an impressive 9 badges. Our stellar customer satisfaction scores and robust market presence have driven this remarkable achievement. In the 2023 Summer G2 Report, Red…Continue Reading: OnDMARC Named DMARC Leader in G2’s Summer 2023 Report
How are attack vectors and attack surfaces related?
Security experts need reports of continuous asset discovery over a specific attack surface to mitigate cyber risks. Cybercriminals exploit vulnerable assets using attack vectors. This blog discusses the connection between these two terms that are mistakenly used interchangeably…Continue Reading: How are attack vectors and attack surfaces related?
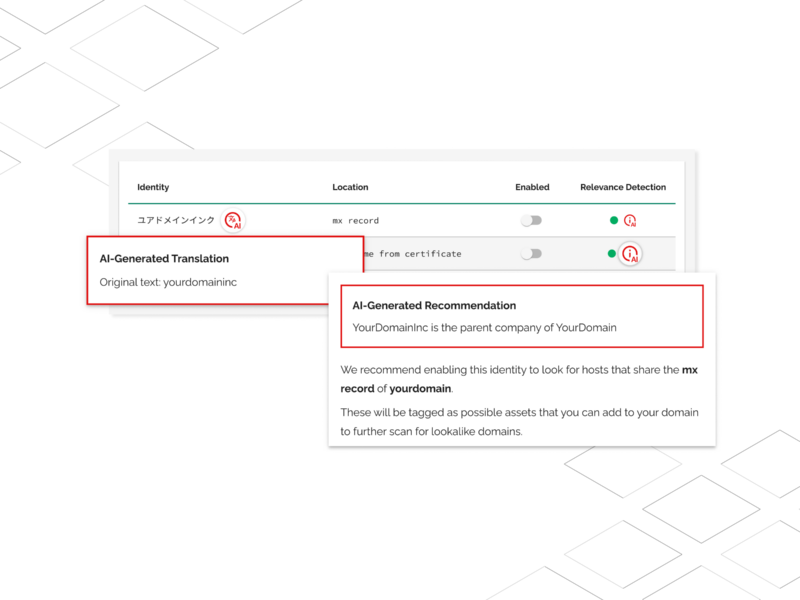
Red Sift Brand Trust launches first GPT-4 powered feature, Relevance Detection
Relevance Detection is an AI-powered feature that automatically classifies the significance of identities found across sources such as DNS, WHOIS info, SSL certificates, and many others…Continue Reading: Red Sift Brand Trust launches first GPT-4 powered feature, Relevance Detection
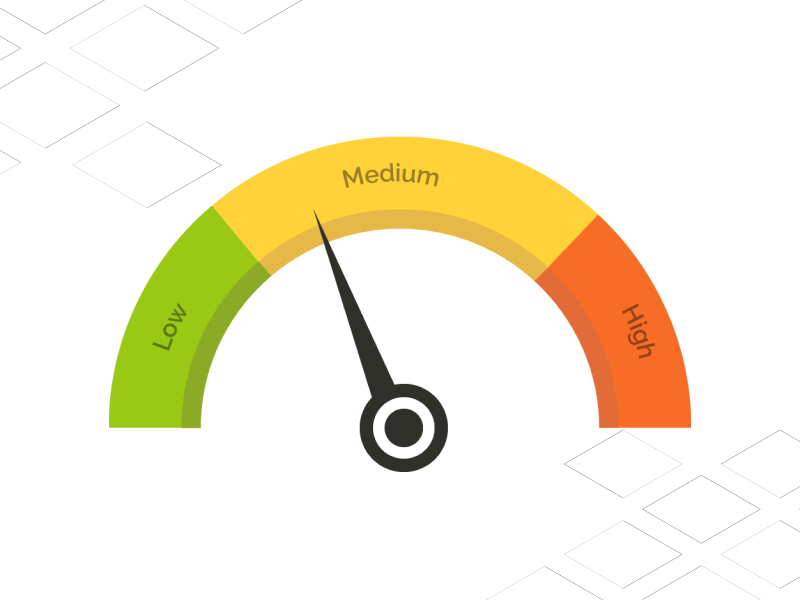
How does a customer improve their security rating company score?
Cyber Risk Security Ratings Companies gather publicly available information about an organization’s estate, assess the security posture, and then provide a score or grade based on what they observe…Continue Reading: How does a customer improve their security rating company score?