In times when businesses are embracing digital transformation at a pace faster than one can fathom, exposure management becomes a crucial element to effectively address the pervasive challenge of mitigating cyber attacks, data breaches, and other security risks. While adopting new technologies and digital services might give businesses the boost they deserve, it also broadens the attack surface, subsequently increasing their exposure to potential threats.
Moreover, owing to the ever-evolving and sophisticated nature of cyber threats, exposure management must be an ongoing effort, necessitating that firms keep abreast of the most recent advancements in security best practices and technologies. To address this challenge and help security teams identify and ultimately dodge these threats, implementing a defined strategic approach like Continuous Threat Exposure Management (CTEM) can be conducive.
In this blog, we’ll look at the fundamentals of Continuous Threat Exposure Management (CTEM), a cybersecurity strategy coined by Gartner, and how it can help organizations minimize the risk of cyberattacks.
What is Continuous Threat Exposure Management or CTEM?
CTEM is a strategic approach to cybersecurity that incorporates constant, real-time monitoring and management of an organization’s vulnerability to threats. It is a kind of security technique that seeks potential flaws and threats before hackers can exploit them, rather than relying solely on reactive measures like firewalls and antivirus software. In a report published in July 2022, Gartner pointed out that;
“By 2026, organizations prioritizing their security investments based on a continuous exposure management program will be three times less likely to suffer from a breach.”
Gartner
That is to say, if companies don’t take actionable measures to detect and prevent potential threats and vulnerabilities, they might be at greater risk.
With an aim to assist end-users in determining the degree to which their digital assets are: accessible, exposed, and exploitable by cyber attackers, CTEM employs advanced analytics, Machine Learning, and Artificial Intelligence to identify and prioritize these threats.
By giving organizations a real-time view of the cybersecurity risk posture, CTEM helps them make more informed security decisions, such as how and where to allocate resources to curtail these attacks. When businesses have a thorough incident response plan and use automated threat detection and response systems, they can reduce the detrimental impact of security incidents and keep them from augmenting into significant breaches.
Furthermore, considering the ubiquity of cyberattacks in the digital domain, it becomes imperative for firms to comply with “government and regulatory body frameworks to achieve and demonstrate cyber resilience.”
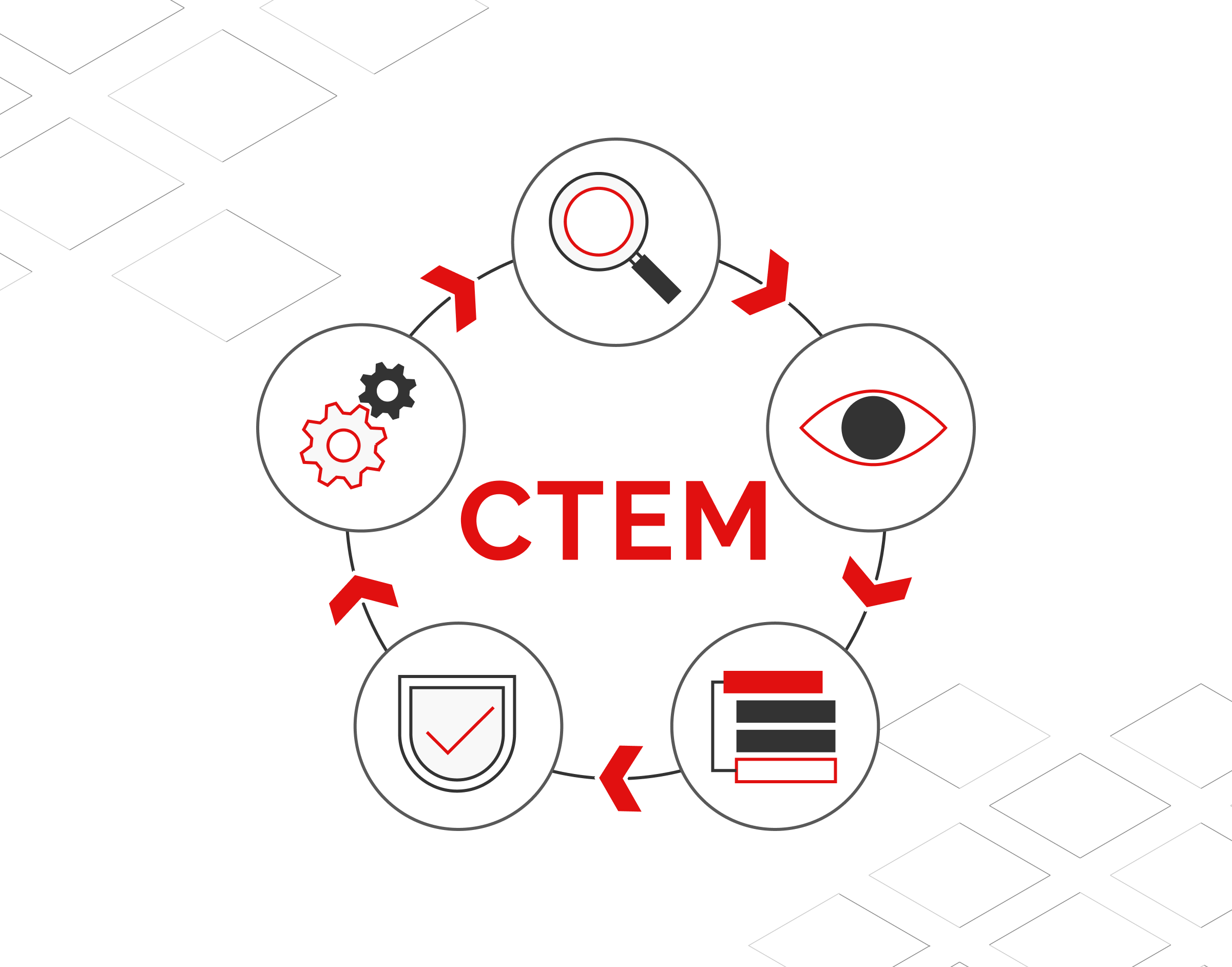
The Five Stages of CTEM Implementation
The five phases of the CTEM program—Scoping, Discovery, Prioritizing, Validation, and Mobilization—complete the cycle and are necessary for its success. So let’s have a look at these stages.

Scoping
Scoping, the first stage of Continuous Threat Exposure Management (CTEM), entails establishing the program’s scope, identifying the most crucial assets to protect, and determining the risk associated with those assets. This stage of the CTEM course is essential to its overall success since it establishes the framework for all that follows.
Discovery
The Discovery phase of Continuous Threat Exposure Management (CTEM) involves identifying and cataloging all vulnerable resources, such as hardware, software, databases, and network infrastructure. During this phase, businesses use a wide variety of IT discovery tools and methods to audit all their IT resources and find potential flaws and dangers, which often include conducting vulnerability assessments, penetration testing, and other security audits.
Prioritizing
After scoping and discovery of prevailing vulnerabilities in the digital infrastructure of the organization, the natural course of progression leads us to Prioritizing. The prioritization phase of the Continuous Threat Exposure Management (CTEM) evaluates the risk associated with each asset discovered in the discovery phase and ranks them based on their criticality to the business operations. Businesses often use a risk assessment methodology to analyze the severity and likelihood of each threat to their assets during this stage.
Validation
In this stage of CTEM, security teams put their plans for addressing the vulnerabilities and threats deemed to be the greatest priority into action and testing them. This could involve adding additional safeguards, updating software, or changing security settings. It’s also worth noting that, akin to the discovery stage, it’s crucial to involve a wide range of stakeholders, including IT people, security personnel, and other employees who may have different viewpoints on potential vulnerabilities.
The Validation phase is crucial for ensuring that the organization’s vulnerability to threats has been effectively controlled and decreased. It enables security teams to assess the effectiveness of remediation operations and make necessary improvements to improve the organization’s security posture.
Mobilization
The Mobilization stage, the final stage of the CTEM strategy, involves defining the scope of the initiative, setting goals and objectives, identifying key stakeholders and resources needed to support the effort, and, most importantly, conducting a readiness assessment to determine the organization’s current level of cybersecurity and exposure management maturity. Since Gartner warns against over-relying on automation, this assessment might help detect vulnerabilities before deploying CTEM.
External Attack Surface Management (EASM) and Continuous Threat Exposure Management (CTEM)
With the rise of cyber-attacks and data breaches, firms should take a proactive approach towards cybersecurity and risk management. That being said, staying a step ahead of cybercriminals, who are constantly on the lookout for gaps in a company’s infrastructure through which they can steal sensitive information or cause other damage, requires a combination of the concepts of external attack surface management (EASM) and continuous threat exposure management (CTEM).
We’ve already established that threat exposure is the risk a firm faces from cybersecurity hazards such as external attacks, insider threats, and other security issues. Further to this, organizations can implement CTEM strategies to stay vigilant of any malicious activities by constantly monitoring their system applications and responding swiftly to those threats.
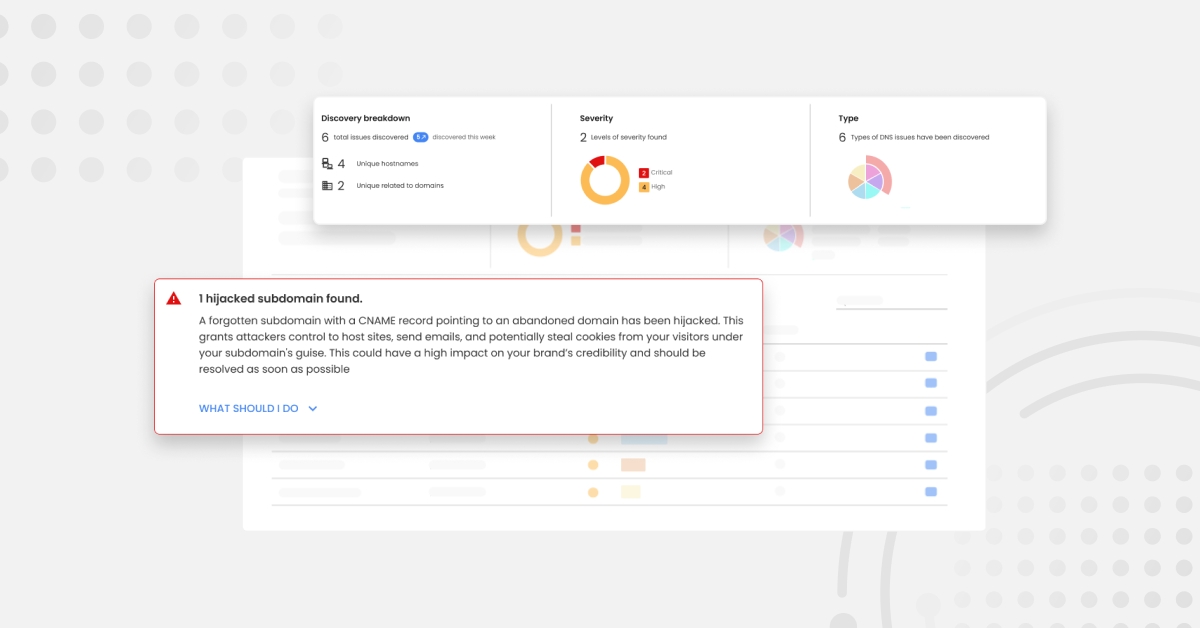
Another way security professionals can streamline their efforts is by employing External Attack Surface Management (EASM). EASM identifies, evaluates, and maintains an organization’s external attack surface by finding and documenting external-facing objects that can pose as network breach sites. These sites include discovering outdated software or misconfigured servers before attackers exploit them.
Get Started With Red Sift
While it might seem that launching an effective and seamless CTEM program is primarily contingent on the technology, the virtue of its success is the platform which consolidates your security posture assessment and optimization functions, streamlines the process, and helps execute the program.
As one of the first highly scalable cloud platforms designed for enterprises of all sizes, Red Sift brings together external attack surface management (EASM) and vulnerability prioritization to help organizations see, solve, and secure the greatest vulnerabilities across their digital infrastructure.