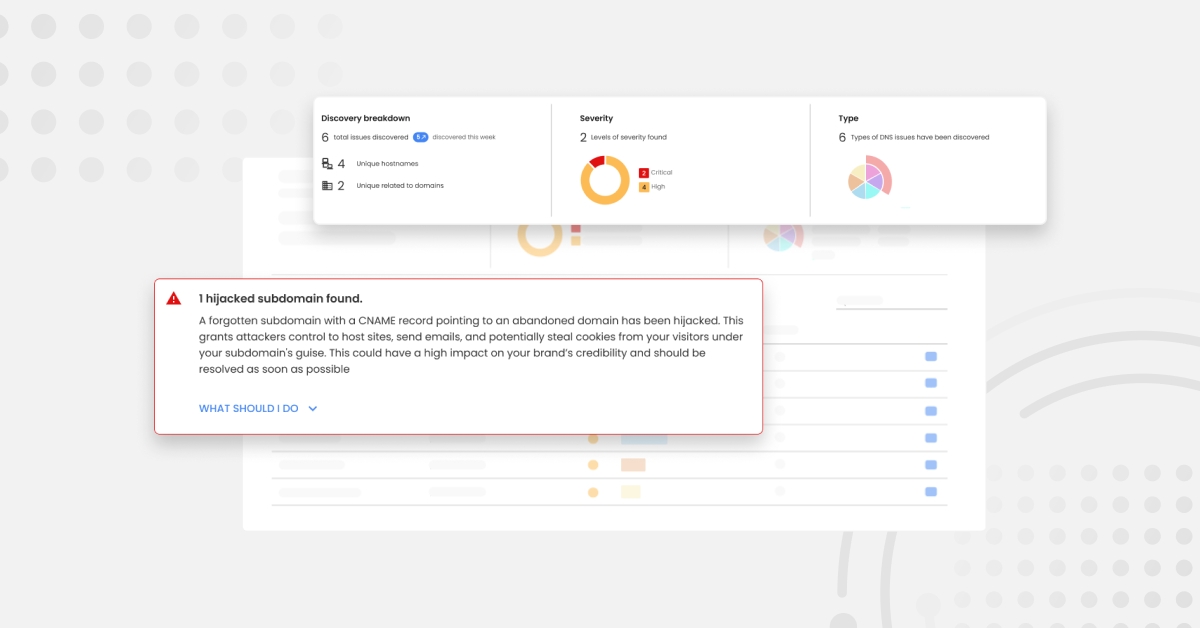
We’re thrilled to announce DNS Guardian — a new feature in Red Sift OnDMARC that can swiftly identify and stop domain takeovers that lead to malicious mail.
Back in February, we shared updates with the community about SubdoMailing – an attack discovered by Guardio Labs. The attack was a form of subdomain takeover, in which bad actors were able to send spam on behalf of legitimate brands through subdomain hijacking (for all the details on the attack, go here).
After our own research discovered that SubdoMailing is much more widespread than originally believed, we felt compelled to take action to ensure our customers are protected.
That’s why we are thrilled to introduce DNS Guardian – a new feature in Red Sift OnDMARC. DNS Guardian continuously monitors your domains for misconfigurations to stop domain takeovers – including SubdoMailing.
In this blog post, we will share why we are introducing these changes, what problems these changes solve for our customers, and how our customers can get access to DNS Guardian. You can also get all the details in our on-demand live session from June 27.
Addressing the gap between DNS and DMARC
Before getting into the details of DNS Guardian, it is important to understand the overlap between domains, subdomains, DNS and DMARC.
This is a very high-level overview. If you are looking to better understand these concepts, check out our blog.
What’s DNS?
DNS (Domain Name System) is like the phone book of the internet. It translates domain names (like www.example.com) into IP addresses that computers use to locate each other. If DNS records are not well-maintained, they can become an easy target for hackers to gain control of a domain they do not own.
What’s DMARC?
DMARC (Domain-based Message Authentication, Reporting & Conformance) is a protocol that helps prevent email spoofing. DMARC uses DNS records to verify emails. It checks DNS entries to see if a given domain is allowed to send emails on your behalf (through SPF) and if it’s been tampered with (through DKIM).
Confused about the nuances of DMARC? Check out our email security guide.
The overlap of DNS and DMARC
In the SubdoMailing attack, hackers exploited gaps in DNS setups to bypass DMARC protections. Here’s how it can happen:
- Identify Weaknesses: Bad actors look for DNS records that are not properly configured or maintained. This can include DNS that points to domains that are expired that the bad actor can re-register or DNS records that have outdated items included in the SPF.
- Exploit the Weakness: Using these weaknesses, bad actors can spoof emails from legitimate domains.
- Bypass DMARC: Poor DNS hygiene can make it easier for these fake emails to slip through DMARC checks, reaching unsuspecting victims.
SubdoMailing has proven that this threat is no longer hypothetical. Your DMARC is only as strong as your DNS hygiene. Keeping your DNS records accurate and covering all subdomains ensures that DMARC can do its job properly, protecting your brand from impersonation in the inbox.
Said another way, if you aren’t maintaining your DNS, there is no guarantee that your DMARC policy is working as expected.
If you want to learn more about the overlap between DNS and DMARC, check out our blog.
What’s DNS Guardian and how can it help my team?
DNS Guardian bridges the gap between DNS and DMARC to make sure brands are protected from takeover attacks and impersonation in the inbox. With DNS Guardian, email and security teams can stop ongoing attacks, protect revenue, mitigate fines, and empower overworked security teams.
Best of all, DNS Guardian takes the manual work out of DNS monitoring.
Sometimes seeing is believing. Watch our Red Sift OnDMARC Product Manager, Reid Cockrell, walk through DNS Guardian in less than three minutes.
What makes DNS Guardian different?
Through Red Sift ASM and our deep expertise in DNS, Red Sift is the only DMARC provider that is able to surface the level of domain detail required to prevent takeover attacks like SubdoMailing.
Here is how:
- Subdomain Discovery: Utilize advanced discovery techniques from Red Sift ASM to identify all subdomains associated with a given domain.
- Dangling DNS Detection: Identify subdomains with misconfigured or orphaned DNS records that are susceptible to being taken over by malicious actors.
- Bad Actor Identification: Detect subdomains already controlled by bad actors through CNAME takeover or legitimate CNAME delegation with poisoned SPF records.
- Risk Assessment: Analyze the severity and impact of identified vulnerabilities and security threats.
- Actionable Insights: Provide actionable recommendations and remediation steps to address identified risks and strengthen domain security.
How do I try DNS Guardian?
OnDMARC Premier with DNS Guardian will be available from Red Sift as well as through Cisco as Domain Protection Premier. For existing Red Sift ASM and Red Sift OnDMARC customers, DNS Guardian will be enabled automatically. Stay tuned for updates for Red Sift OnDMARC for MSPS.
If you are interested in trying DNS Guardian, get in touch. We can’t wait to help you get control of your domain health.
On the fence? Sign up to watch our on-demand live session to see how DNS Guardian can help your team identify and stop domain takeovers that lead to spam.