When the threat of SubdoMailing was newly discovered, we wrote a comprehensive guide and worked to get our impacted customers remediated within 72 hours of the discovery being published by Guardio Labs.
We are proud of what we accomplished, but through the process, we also discovered that many people don’t fully understand the overlap of DMARC and DNS. Because of the widespread nature of SubdoMailing, it is critical that security teams understand how these two protocols are related to make sure their domain is protected.
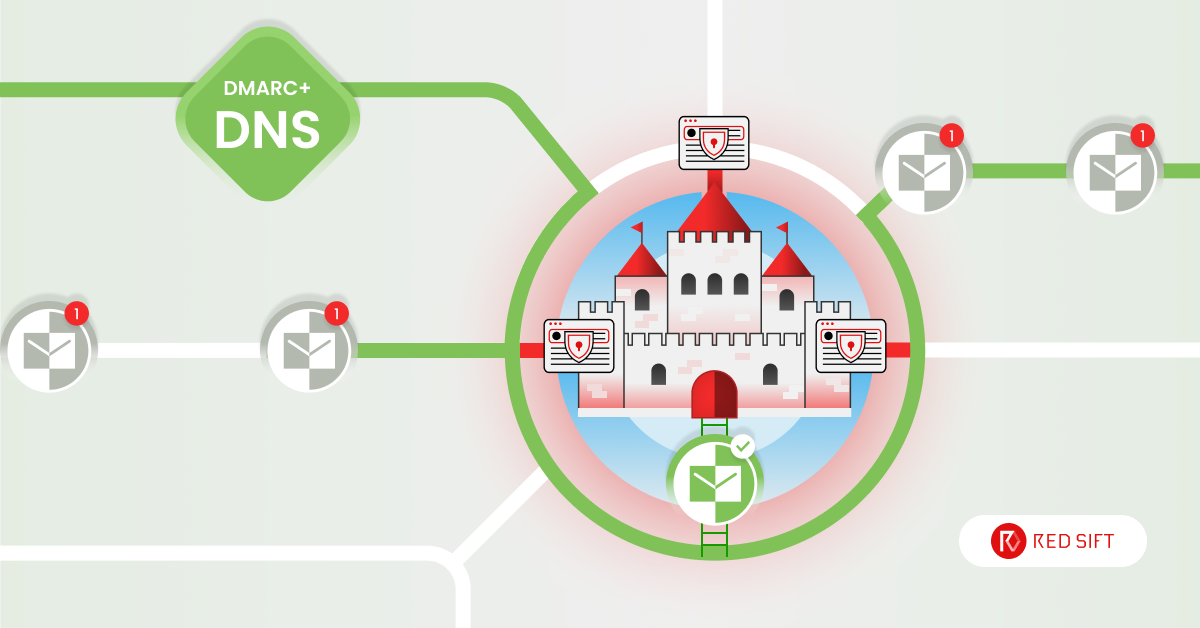
Here, we aim to give a non-technical overview of DNS and DMARC to better illustrate the interdependencies of these core pillars of email security using a castle metaphor.
DNS is the foundation for DMARC
Domains, subdomains, DNS and DMARC are all deeply interconnected. Let’s first discuss each one of these topics independently, and then cover the overlap.
Domains and Subdomains
Imagine your company website is a castle, and your domain name is the main gate. The smaller buildings and courtyards outside the main gate are your subdomains. These subdomains are like side entrances, tunnels, and even hidden entrances to your castle.

What’s DNS?
Now imagine the DNS (Domain Name System) as the castle’s map system. It helps visitors find the main entrance (domain) and other entrances (subdomains).
When someone asks, “Where is example.com?” the DNS translates this request into a specific location (IP address). This would be equivalent to guiding the visitor to the right place inside the castle.
Similarly, if someone asks for blog.example.com, the DNS provides the exact directions to the side entrance – in this case, the blog section.
When DNS works correctly, users effortlessly reach the desired website, just like finding the right entrance on a well-maintained castle map.
What’s DMARC?
At Red Sift, we are big fans of DMARC (Domain-based Message Authentication, Reporting, and Conformance). Building on our metaphor of a castle and map, think of DMARC as the diligent guards who protect the castle from the wrong people entering and exiting.
How DMARC works
- Verification: Just as the guards verify the identity of messengers claiming to represent the castle, DMARC verifies emails claiming to come from the domain. It ensures that the emails are genuinely from authorized senders and not from malicious imposters.
- Policies for Action: The guards have specific policies for dealing with messengers based on the verification requirements the organization has set:
- None: They let the messenger pass without any special action but note down their details for review.
- Quarantine: They detain the messenger in a secure area for further inspection, ensuring no immediate harm is done.
- Reject: They outright refuse entry to the messenger, ensuring no fake or malicious messages reach the castle.
- Security: The guards protect the castle from receiving harmful or unwanted packages. In the digital world, DMARC adds a layer of security by preventing phishing attacks and email spoofing, ensuring that only verified emails reach their intended recipients.
The Overlap of DNS and DMARC
DMARC policies live in the DNS. DMARC checks DNS to verify the policy, sees if a given domain is allowed to send emails on your behalf (through SPF) and if it’s been tampered with (through DKIM).
Said another way – the castle map (DNS) guides the emails to the correct domain, while the diligent guards (DMARC) ensure that only legitimate emails gain access to the inbox.
Confused about DMARC? Check out our email security guide.
Exploiting Poor DNS Hygiene to Bypass DMARC
In the case of SubdoMailing, bad actors proved that even organizations with the highest levels of DMARC enforcement (p=reject) can still be victims to bad actors sending fraudulent mail from their domain if their DNS hygiene is poor.
Revisiting our metaphor one last time – what happens if the map is up to date but the guards have forgotten about one of the secret entrances and left it unlocked and unprotected? This is akin to poor DNS hygiene, where DNS records are not properly maintained, allowing cybercriminals to take control of these secret entrances and get past the guards undetected.
Poor DNS hygiene enables bad actors to bypass security measures and deliver malicious emails to unsuspecting recipients because it looks legitimate.
Introducing DNS Guardian – Now in Red Sift OnDMARC
We know with the SubdoMailing attack being widespread, bad actors are capitalizing on poor DNS hygiene. We are compelled to give our customers the tools they need to protect their domains from takeover, abuse, and supply chain attacks.
That’s why today, we are pleased to announce DNS Guardian – a new feature available in OnDMARC that helps users continuously monitor and manage DNS hygiene.
Get all the details on DNS Guardian here.