Ever wondered about how whale phishing differs from spear phishing? Well wonder no more as Gino explains it all in this article for IT ProPortal.

Ever wondered about how whale phishing differs from spear phishing? Well wonder no more as Gino explains it all in this article for IT ProPortal.
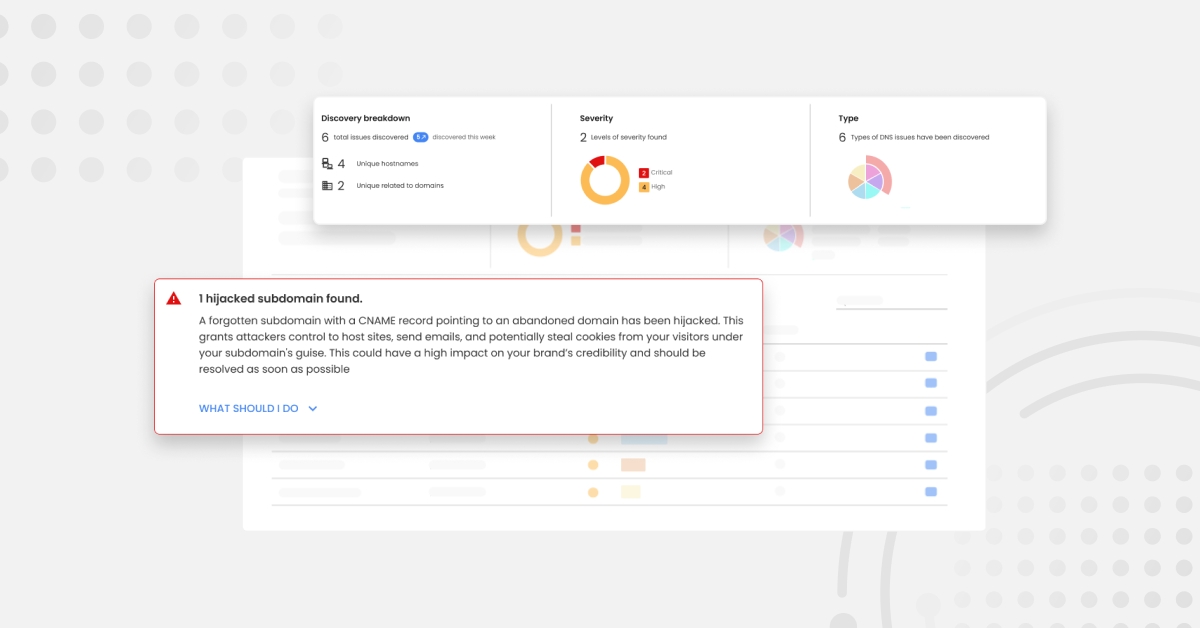
tl;dr: We’re thrilled to announce DNS Guardian — a new feature in Red Sift OnDMARC that can swiftly identify and stop domain takeovers that lead to malicious mail. Back in February, we shared updates with the community about SubdoMailing – an attack discovered by Guardio Labs. The attack was a form of subdomain takeover,…
Read moreThe recent webinar hosted by Inbox Monster, “What’s Next for DMARC: Data & Predictions for a New Era in Email Authentication,” featured insights from Red Sift and examined the significant changes brought by Yahoo and Google’s bulk sender requirements earlier this year. It also offered a forward-looking perspective on the future of email authentication.…
Read moreAs cyber threats evolve, so do the standards and frameworks designed to combat them. Two of the most recognized standards in information security are ISO 27001 and SOC 2. What sets them apart, and which one is right for your organization? Let’s delve into the key differences. Purpose and Scope: Global Framework vs. Client-Centric…
Read moreWe’re delighted to announce that Red Sift OnDMARC has again been named a Leader in G2’s DMARC category for Summer 2024. This recognition is based on our high Customer Satisfaction scores and strong market presence. Red Sift appeared in 11 reports – 5 new ones since Spring 2024! – earning 5 badges: A few…
Read more
Tl;dr: Google has announced that as of October 31, 2024, Chrome will no longer trust certificates signed by Entrust root certificates. While there is no immediate impact on existing certificates or those issued before 31st October 2024, organizations should start reviewing their estate now. On Thursday 27th June 2024, Google announced that it had…
Read more