Why is everyone making such a fuss about DMARC and its importance for email security? In short, because it’s easy for cybercriminals to send emails pretending to be you, and DMARC is the only protocol that can stop this.
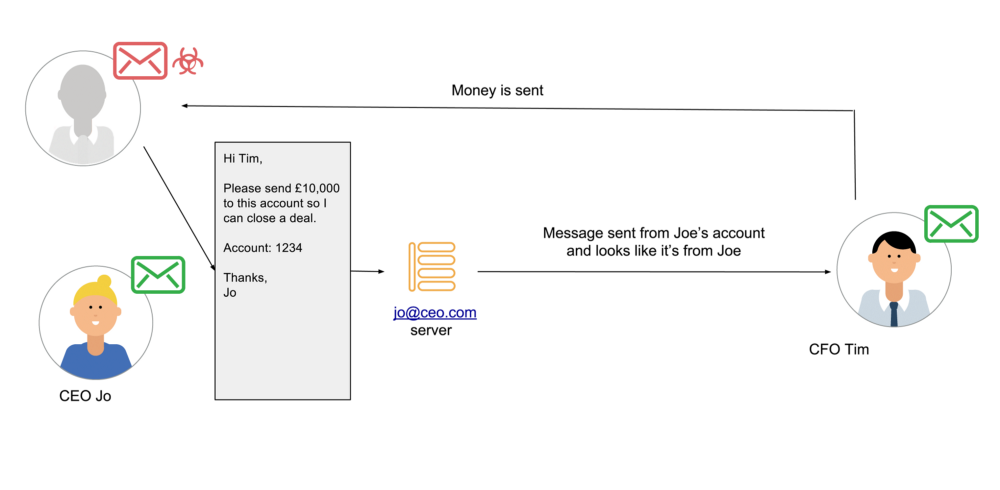
If your domain isn’t DMARC protected, then your business is highly vulnerable to Business Email Compromise (BEC). By easily spoofing your company’s domain, a cybercriminal can send phishing emails pretending to be your CEO, and gain access to money, data, and/or credentials by tricking employees into divulging these.
For example, this bad actor posing as the CEO might ask accounts, or even the CFO, to make a transfer of funds. Because the email comes from a legitimate email address, the recipient is unlikely to question it, and might even act on it without thinking. And just like that, your business is compromised.
This is just one example of the types of BEC attack companies that aren’t DMARC protected regularly face. Some more examples are here: Another homebuyer loses £67k as solicitors fail to warn of email fraud, NHS trust cyber attack, How Hillary’s emails may have lost her the election, and stealing from Tesla.
How important is email for businesses?
Email is a widely-used communication tool, both B2B and B2C, and it’s surprisingly vulnerable to impersonation attacks. This means it poses a significant threat to both organizations and individuals (that’s right, hackers can spoof your domain to phish your customers too).
So why don’t more businesses adopt DMARC? Well because they either feel that they would not be a worthwhile target, they believe it’s too difficult, or because they simply assume that their mailbox provider is protecting them. You can easily identify how well protected your domain is by using the free OnDMARC domain checker.
Red Sift conducted a study and analyzed 3,004 government domains and 71,000 charity domains. The results showed that only 6.4% of government domains and 1% of charity domains were DMARC enabled. The NCSC has now required that all government bodies implement DMARC on all government domains.
My domain mail is managed by G Suite or Office 365, why am I not protected?
DMARC configuration is the responsibility of the domain owner, not the email provider. A typical business will send emails from their domain name via several email providers, i.e.: human emails from G Suite, marketing campaigns via MailChimp, CRM emails via SendGrid, etc. In order to have your domain protected by DMARC, you need to make sure that all these different email sources are correctly configured. That’s the reason why email providers cannot offer automatic DMARC protection to their users.
My personal account is with Gmail or Yahoo, am I protected?
Yahoo was one of the first providers to protect their consumer email accounts with DMARC therefore personal accounts using their services are protected. At the time of writing this post, Gmail has its DMARC record in reporting-only mode therefore users are not yet protected however some media sources report that they are planning to enable enforcement soon. If you own your own domain, you can use and implement DMARC irrespective of who your mail provider is. DMARC was actually created by Google, AOL, Yahoo, and a few others who came together in 2011 to collaborate on a method of combating fraudulent email at internet scale.
How does DMARC work with SPF and DKIM?
DMARC stands for, Domain-based Message Authentication, Reporting & Conformance. DMARC ensures that emails are authenticated properly and allows senders to define how email recipients deal with unauthenticated emails. This blocks malicious emails and increases the deliverability of authorized emails. The way that DMARC does this is by using SPF and DKIM, two foundational technologies that help secure different aspects of email. The problem with only using only SPF and DKIM is that they do not work together or enforce a policy.
DMARC uses the validation results from both SPF and DKIM to provide a more comprehensive validation. SPF verifies if an email was sent from an authorized IP address whereas DKIM verifies if an email has been signed by the same domain it was sent from or from a domain authorized to send on behalf of that domain. They both produce what is known as authentication identifiers that DMARC uses to authenticate emails and set rules about how receiving servers should treat emails that fail authentication checks.
Why is Red Sift’s OnDMARC the best choice for DMARC protection?
OnDMARC guides you through a step-by-step process of implementing and maintaining DMARC. Let’s take a more in-depth look at DMARC and where OnDMARC comes in.

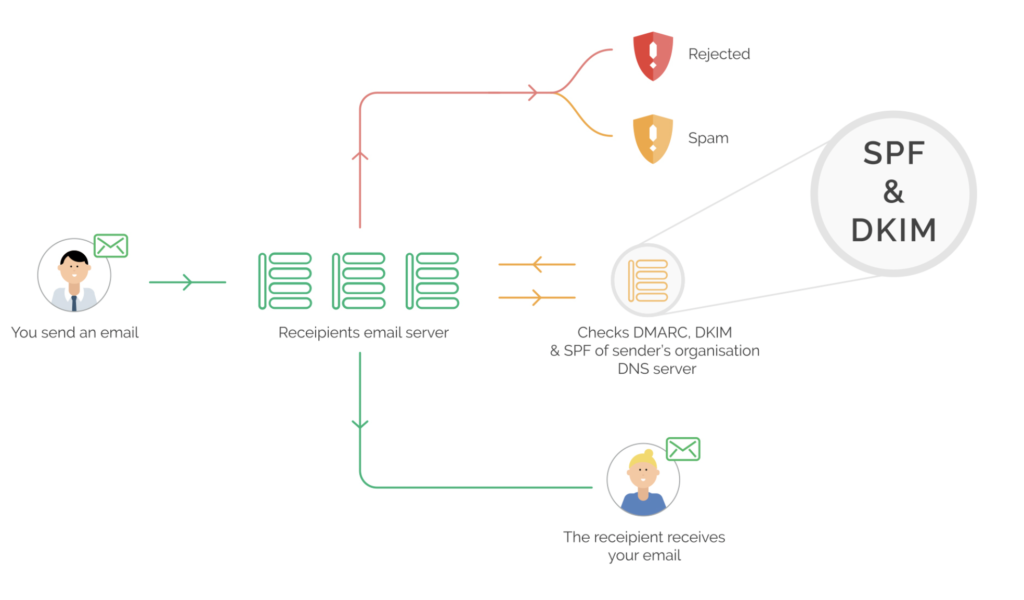
1a and 1b — An authorized message is sent or an unauthorized message attempt is initiated to the receiver’s email server.
2 — The receiver’s server then checks the sender’s DNS for DMARC, SPF and DKIM records.
3 — The receiving server then verifies the incoming message against SPF and DKIM and if either SPF or DKIM validation passes it sends the message onto the recipient.
4 — If the validation fails, based on the DMARC policy configured it will either send the message to a spam folder or completely reject it and the end-user will never see the failed message.
5 — At least once a day, all email servers that received messages from your domain will submit a report to OnDMARC containing information about the origin and number of messages that passed and failed validation.
OnDMARC uses these reports to analyze a domain’s traffic in order to suggest the appropriate actions for implementing and maintaining a secure DMARC policy for the domain. OnDMARC will allow you to see exactly what is happening on your domain so you can easily identify authorized and unauthorized traffic.

Why choose OnDMARC?
And that’s it! The basics of how DMARC, SPF, and DKIM work to protect domains! We hope that you’ve been able to follow all that but the truth is that you only need to know the very basics as OnDMARC takes care of all the complicated stuff for you.