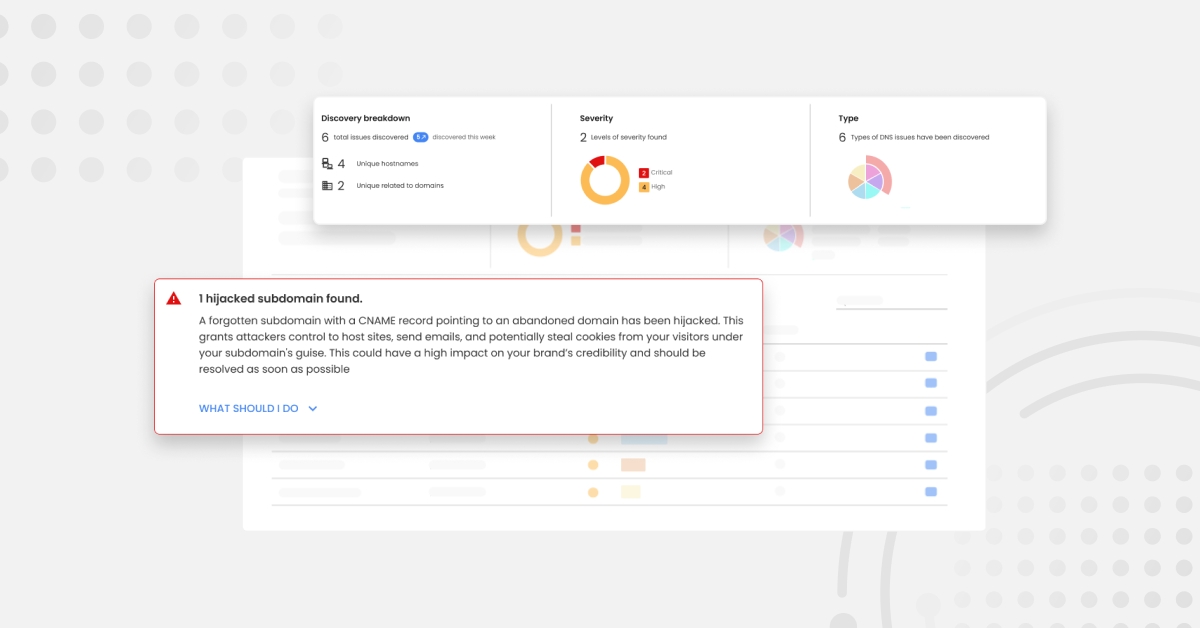
Covid-19 phishing attacks have risen by 400%*.
Whilst public authorities have taken decisive action to respond to the emerging health threat, the business community is having to reconsider the adequacy of measures in place to protect their workforce, systems, and services. A big part of this is organizations now working remotely in order to prevent the spread of this new virus and we’re seeing Covid-19 phishing attacks increase at the same time.
What are the security challenges?
Cybercriminals are taking advantage by impersonating health and government organizations such as The Center for Disease Control and The World Health Organization in malicious email campaigns. These are designed to invoke fear and trigger a reactive response from the person receiving the email. This knee-jerk response will involve an action that gives a cybercriminal access to sensitive information, money or even systems access for ransom. This is why securing business communications is essential to ensure your newly remote workforce remain safe.
5 steps to help secure a remote workforce
Here are our top 5 security tips to help IT teams securely and proactively address business continuity during the transition to remote working:
1 – Block fake emails sent from your domain
With DMARC (Domain-based Message Authentication, Reporting and Conformance) properly configured for your domain, you can block cybercriminals from impersonating your organization with Covid-19 updates. These may include Covid-19 instructions, or business advice sent to unsuspecting employees, suppliers and partners. With tools like OnDMARC you can simply follow step-by-step instructions to configure DMARC and block this type of domain fraud. Already started your search for a DMARC provider?

You can find our eBook guide on how to find your perfect DMARC provider in our site’s resource center.
2 – Increase awareness of Covid-19 scams or install software to do it for you
Work to increase awareness amongst your remote workforce around new inbound email fraud and exercise caution in handling any email with Covid-19 content. Alternatively, you can install software like OnINBOX’s intelligent email threat detection, which will automatically scan for these threats and point them out at the top of every email for your colleagues wherever they’re working from.
3 – Shine a light on Shadow IT as distributed employees use new services
As employees work from home, some for the first time, shadow IT will also creep in… OnDMARC will give IT teams up-to-date knowledge about new services being used, such as marketing signing up for a new automation service. OnDMARC automatically surfaces new sending services in your home dashboard so that you can sleep easy!
Learn more about Shadow IT in our blog here.
4 – Control access to your corporate systems
A Virtual Private Network (also known as a VPN) is a mechanism for securely connecting devices or networks together, even if geographically separated. Hence why at this time during the Covid-19 outbreak, they are popular for enabling remote working from end-user devices (EUDs). This NCSC guide to Virtual Private Networks provides risk owners and IT administrators considering this mechanism with more advice.
5 – Last but not least, set up multi-factor authentication for online services
By ensuring your remote workers have multi-factor authentication (MFA) in place, you’re mitigating the risk of password theft. MFA (multi-factor authentication) can also be called two-step verification or two-factor authentication (2FA) – take your pick! For advice on implementing multi-factor authentication to protect against password guessing and theft online check out this article by the NCSC here.
To learn more about how Red Sift can help you protect your remote workforce from Covid-19 phishing attacks, check out our home page.

Sources
* A March 2020 snapshot of Covid-19-themed phishing attacks as reported by a well-known cybercrime consortium.