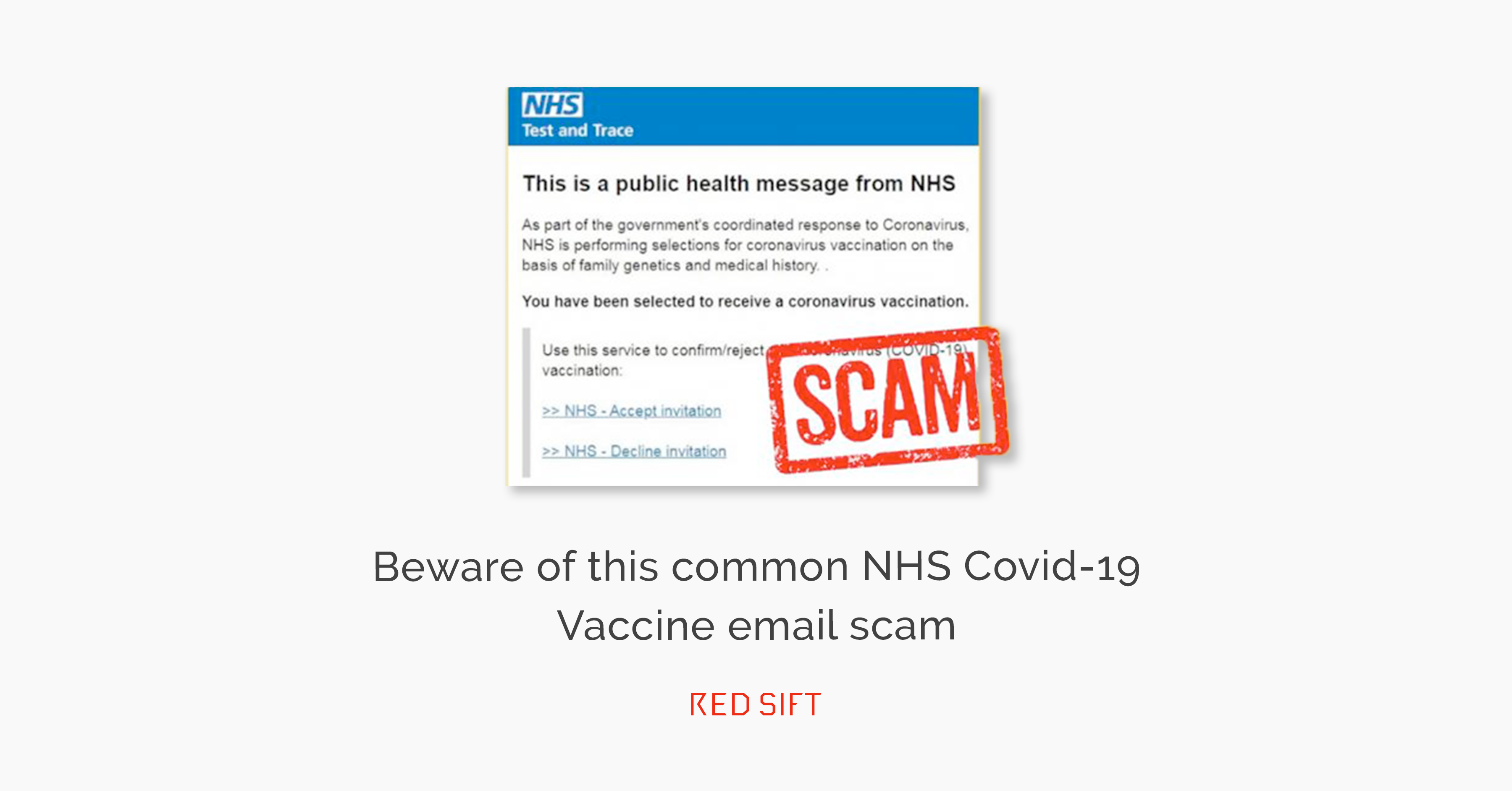
Last April I published a blog on the use of the “Friendly From” field to create convincing-looking emails that would fool most users. In this last week, there has been a very convincing email doing the rounds asking users to sign up for their Covid Vaccination.
In this Blog I warn that legitimate-looking email addresses are being put into the “Friendly From” but inside the wrong shape brackets. E.g. (John.smith@company.com) instead of inside <angle brackets> as these are the correct brackets for an email address.
Well, the recent NHS spoof was a simple but very clever twist on this theme.
Here is the actual header information from one of those spoof emails:
From: “noreply@nhs.gov.uk <noreply@nhs.gov.uk> on behalf of NHS digital <noreply@nhs.gov.uk>” <kanda@visceral.co.jp>
Date: 25 Jan 2021 15:58
Subject: Book an appointment using the NHS e-Referral Service – NHSVaccination
Again if you look at this string the only part that matters is the end email address inside the angle brackets. E.g. <kanda@visceral.co.jp> This is the “From address”. What appears before this is the “Friendly From”… you would normally expect this to be something like John Smith and it is just text.
What the attacker has done that is so very clever is they have put everything in the “Friendly From” field inside “quotes”. This has the effect of turning everything inside the quotes into text – The receiving mail system will ignore the angle brackets inside the “friendly from” but most people won’t spot the quotes or even understand the significance of them. To them it will look like the email has come from <noreply@nhs.gov.uk> especially since on a mobile device, the true “From” may not get displayed at all.
The second technique used is to pad out the length of the text string. On some devices, only a limited number of characters from the start of the email address will be displayed. By using a long text string the attackers are hoping that the real “From” address will not get shown. On many devices and clients, only the “Friendly From” is displayed in an attempt to make the interface more user friendly!
You have to recognize the simple but effective techniques used here will fool most people. Even with training, this was not easy to spot. You would think that there would be some way of stopping hackers from putting email addresses inside the “Friendly From” but this is perfectly within the scope of what is defined in the RFC.
I would point out that the Red Sift solution for Inbound Phish detection OnINBOX picked this attack up. We actively monitor the “Friendly From” in every email and if it contains something that looks like an email address we compare it to the real “From” address and if they don’t match we flag the email as a threat. (We also detected the link in the email as malicious as well….)
Check out our website to learn more about how our platform can help your organization combat phishing attacks.