TLS certificates – once called SSL certificates and often referred to as just “certificates” – are one of the core ways we keep the internet safe and secure. Certificates encrypt data to make sure it is transmitted privately between your browser, the website you’re visiting, and the website server.
But as the number of services required by your organization increases, so does your dependency on encryption and certificates. Where there’s a dependency, there’s likely to be complexity and problems, and where there’s complexity and problems, a methodology will be created. Welcome to the world of Certificate Lifecycle Management (CLM).
What’s Certificate Lifecycle Management?
The certificate lifecycle starts at the certificate signing request (a CSR) and ends at the expiry date. CLMs were created to automate the issuance, renewal, and deployment of certificates. Given the number of steps in the process – and the mistakes that can happen – CLM emerged as a way for security and IT practitioners to get a handle on their certificate estates.
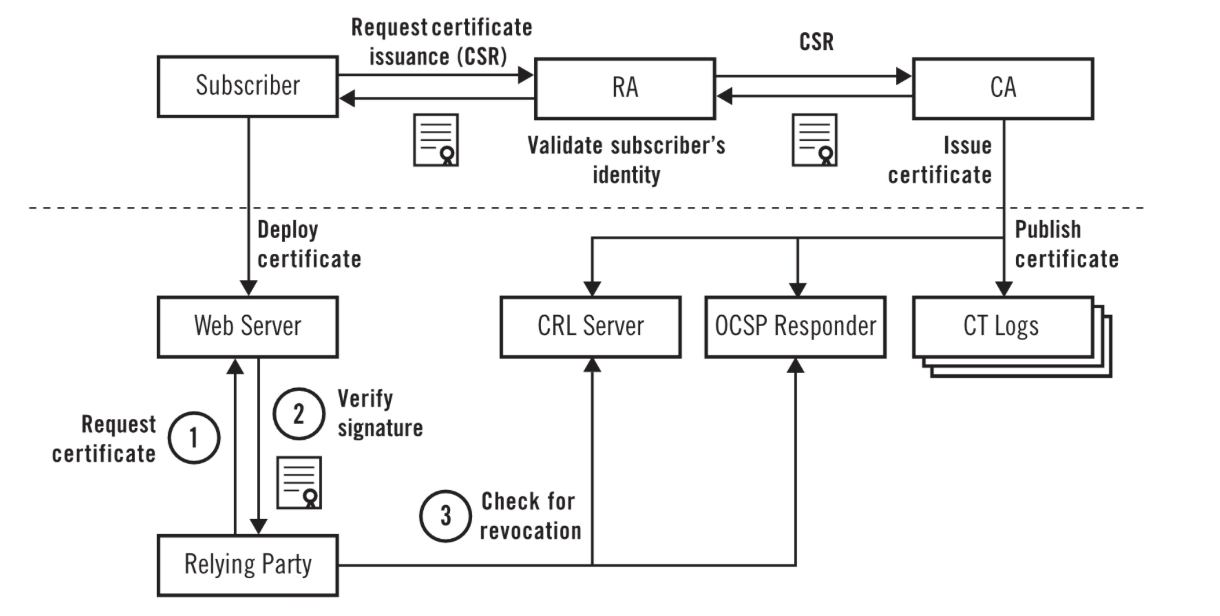
The Internet PKI Lifecycle, courtesy of “Bulletproof TLS and PKI” Second Edition by Ivan Ristic
What is Certificate Lifecycle Management software?
CLM software aims to:
- Automate the lifecycle processes involved in certificates.
- Minimize the risks associated with managing complex public key infrastructure (PKI).
- Provide detailed reporting on certificate usage across the organization.
When talking to other unfortunate souls like me who are tasked with understanding and working with PKI, three CLM vendors tend to come up.
- Venafi
- AppViewX
- Keyfactor
Most vendors tend to go a little deeper and start talking about Machine Identity Management initially, but good CLM is a primary component of a successful identity management strategy. I’ll talk about each of the vendors elsewhere in more detail
Are Certificate Lifecycle Management tools easy to deploy?
“Dealing with complexity is an inefficient and unnecessary waste of time, attention, and mental energy. There is never any justification for things being complex when they could be simple.” Edward de Bono
CLM vendors all share one trait—they need to be all things to all certificates. By design, they must be comprehensive in their scope so that they can sign, validate, issue, deploy, revoke, and report on a certificate. This level of automation requires:
- Deep integrations with certificate authorities, cloud providers, infrastructure providers, application providers, hardware providers, and the derivatives thereafter of those. Venafi has 189 integrations and counting.
- Complicated implementation and documentation. CLM implementations have been known to take months. AppViewX has a user manual that’s 2,261 pages long.
- Significant committed resource from an organization to deploy and fully utilize it.
This level of complexity means that deploying and managing a CLM tool is a difficult program of work in itself before you realize value. Anecdotally, I have spoken with a number of security and cryptography teams who have distanced themselves from working operationally with this category of tooling, as it drains resources significantly.
How does Certificate Monitoring compare?
Certificate Monitoring is interested in observing certificates in some but not all of the stages of the lifecycle of the certificate. Certificate Monitoring aims to ask and answer the following questions about a certificate:
- When has a certificate been issued?
- Has the certificate been correctly issued?
- Where has the certificate been deployed?
- Is the certificate still deployed?
- Has the certificate been revoked?
- Is the certificate due to expire soon?
- Is there any additional information about the certificate that can be found in the CA account?
- What’s the configuration of the certificate?
Crucially, Certificate Monitoring is concerned with checking when a certificate is issued and the steps needed to issue it. This removes the technical and resourcing overhead of the processes and integrations that are required in the early stages of the life cycle of the certificate. This is how certificate monitoring works.
- A certificate is issued or discovered. This can be through Certificate Transparency log monitoring, a host assessment, a network scan, or through a cloud integration with a Certificate Authority (CA) or a cloud computing provider.
- The certificate is checked.
- Does it belong to you?
- Has it been installed?
- Where is it installed?
- Does it match your Certificate Authority Authorization (CAA) policy?
- Has it been issued by a CA that you are expecting to see?
- Is it CT compliant?
- Is it valid for less than 398 days?
- After checking, if there’s a problem with the certificate, the user will receive an escalation. If not, the user will still be notified about the certificate to make sure he or she is aware.
- If the certificate is installed, the certificate’s configuration will be continuously monitored and the user will be notified about any issues.
- If the certificate is installed, it will be monitored through the expiration date. You will receive notifications so that you can replace before expiry. It will also be monitored for revocation events and send you notifications if that happens.
- If the certificate isn’t installed, it will start being monitored when it is installed.
- Once the certificate is no longer installed, it will automatically be removed from the user’s account.
This means that insight to support issue creation, triaging, and remediation is delivered within minutes of onboarding, not days or even months.
For Red Sift Certificates customers this has meant:
- Having a Christmas vacation without worrying about the downtime that expired and misconfigured certificates could be causing, despite onboarding to Red Sift Certificates just two weeks before the end of the year.
- Within seven days, having a Pub/Sub stream of all newly issued certificates that belong to their organization up and running.
- One hour after onboarding, catching a certificate deployed to a key service that was due to expire in just three days times.
- Being able to guarantee a service level that all certificates will be replaced no less than 14 days before their renewal date.
Do I need Certificate Monitoring or Certificate Lifecycle Management?
Whether you need Certificate Monitoring or Certificate Lifecycle Management depends on the problem you have.
If your organization is experiencing painful downtime, embarrassing failed audits, uncomfortable board-level conversations about poor security ratings, and risks from external threat actors because of misissuance and misconfiguration then Certificate Monitoring is for you. This is becoming the norm as most organizations already have CLM processes in place to handle the steps up until issuance, but lack visibility of what happens after that due to poor-performing tools or a lack of investment.
If you have not yet put in automation for the early steps in the life cycle of the certificate, then a CLM tool may be something you should consider. But a Certificate Monitoring product like Red Sift Certificates should be considered as part of that motion. Not only will you find that the product gives better visibility of your certificate estate once your CLM tooling is deployed, it will give you visibility of your existing certificate estate whilst you implement a CLM tool. Our proprietary discovery methods mean that time to value takes minutes and not months.
Certificate Monitoring by Red Sift Certificates
Red Sift Certificates is a Certificate Monitoring application without the overhead created by the early steps of the life cycle. It focuses instead on best-in-class automation tools deployed in minutes that provide immediate and continuous visibility of an organizations certificate estate, expired certificates, upcoming expirations, misconfigurations and misissuances.
See our guides for how Red Sift Certificates compares to Venafi and AppViewX or watch our Red Sift Certificates demo to learn more.