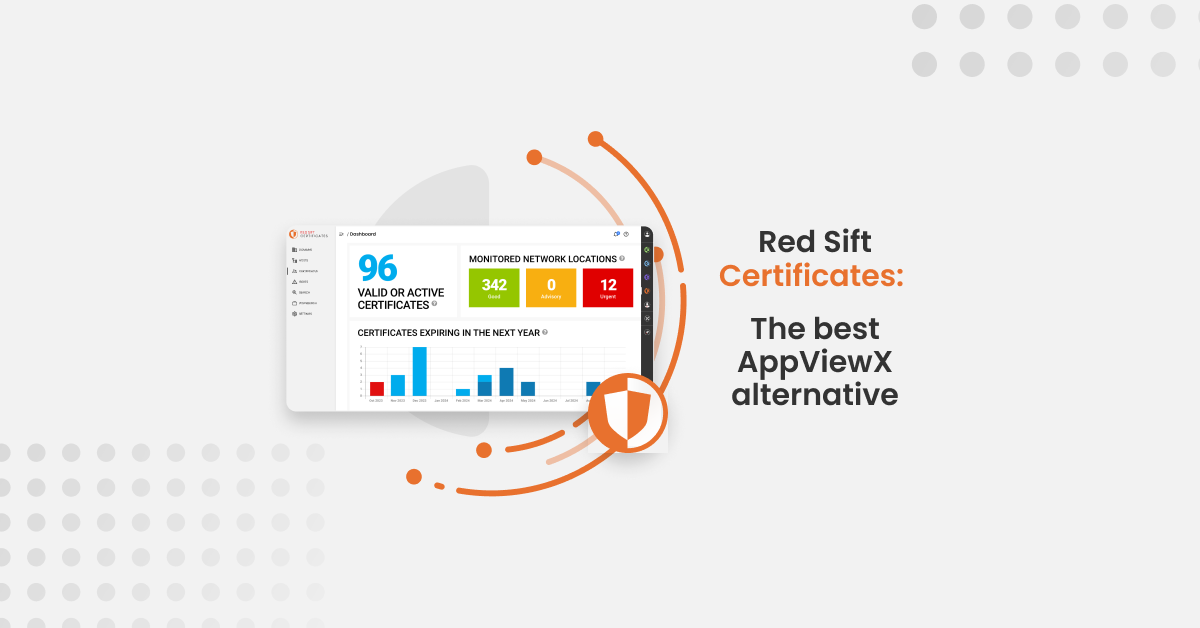
Hunting for an alternative to AppViewX that helps you monitor your certificates to stop downtime and security risk? You’ve come to the right place.
Let’s dive into a no-frills, straight-up comparison between AppViewX and Red Sift Certificates.
AppViewX Overview
AppViewX CERT+ is AppViewX’s certificate monitoring tool. According to their docs, “AppViewX’s CERT+ provides an end–to–end lifecycle management of x.509 digital certificates across complex networks to secure your business.”
AppViewX has a number of other products including PKI+, KUBE+, SIGN+, and ADC+. They are frequently used together. For this blog, we will be referencing CERT+ only.
Red Sift Certificates Overview
Red Sift Certificates stands out as a top-tier solution in the realm of certificate monitoring. It offers up-to-the-minute detection of newly issued certificates and ensures vigilant tracking for both expirations and revocations. While it’s not in the business of issuing, renewing, or revoking certificates itself, Red Sift Certificates is the go-to tool for companies like Coop, Rakuten, William Fry, and Denic to prevent certificate-related disruptions and security concerns.
An interesting note about Red Sift Certificates is its history with Hardenize. In 2022, Red Sift acquired Hardenize, and with this move, the Hardenize team, including its renowned founder Ivan Ristic — the brain behind SSL Labs and the author of “Bulletproof TLS and PKI” — became a part of Red Sift.
The comparison tl;dr
While Red Sift Certificates and CERT+ can both help teams stop PKI-related security risks and downtime, the two take very different approaches. Red Sift Certificates is a Certificate Monitoring tool, while CERT+ has full Certificate Lifecycle Management (CLM) capabilities.
Which tool is right for you depends on your requirements and the problems your team is looking to solve.
Red Sift Certificates gives teams unmatched insight into their certificates to automate inventory, stop misuse, and avoid certificate-related downtime. Because Red Sift Certificates ingests tens of thousands of certificate transparency (CT) log entries, users get continuous visibility into their certificate estate. Red Sift Certificates is simple to deploy and can easily be integrated with the SOAR tool of your choice.
For teams looking to automate all steps across the certificate lifecycle including issuing, renewing and revoking certificates, CERT+ is a better alternative. However it is a more complicated product to deploy—their user manual is 2,261 pages long—with significant configuration steps necessary. That difficulty can also impact on coverage. It’s a challenge to discover all certificates that should be monitored.
Certificate Discovery
Red Sift and CERT+ both discover certificates that belong to an organization. Red Sift Certificates uses fully automated discovery capabilities that layer network monitoring, host assessments, and certificate transparency (CT) log scanning in real time. CERT+ has similar discovery capabilities, but substantial configuration steps for each method are required. CERT+ doesn’t appear to collect important certificates deployed to your estate by third-parties.
Red Sift Certificates: Automated Certificate Discovery for Complete Visibility
Getting started with Red Sift Certificates is straightforward. Just enter a single seed domain, and Red Sift Certificates can create a complete inventory of certificates across your network by looking at hosts, network ranges, domains, and IP addresses. Red Sift Certificates collects and inventories all certificates encountered during the assessment including SMTP and HTTP, or any other TLS-enabled service. In as little as an hour, a user will see substantial results.
You can integrate Red Sift Certificates with major cloud providers like Google Cloud Platform, Microsoft Azure, and your preferred Certificate Authorities for an even broader view.
Additionally, Red Sift Certificates actively monitors certificate transparency (CT) logs, uncovering all publicly-trusted certificates from any CA. This feature is great for keeping an eye on CA operations and tracking certificates issued for your domains and those issued by third parties.
This is the foundation of a comprehensive inventory of all certificates belonging to the user’s organization.
To date, Red Sift Certificates has processed an impressive tally of over 7 billion certificates. Its monitoring is conducted from 10 global locations, making it a great fit for those with networks spread far and wide.
A heads-up: currently, Red Sift Certificates doesn’t support internal certificate monitoring, but this feature is on the horizon and expected to roll out in 2024.
AppViewX CERT+
CERT+ supports multiple certificate discovery methods. For internet-facing assets, AppViewX will conduct network scans, CT log scans, CA scans, and cloud scans. These are scheduled or on-demand.
To identify certificates on a private network CERT+ supports device scanning, with a separate product available for certificate monitoring of Kubernetes environments.
Each discovery method supported needs to be configured separately.
Freshness
In Scotland, we drink a lot of Irn-Bru. There’s nothing better than a freshly opened can straight from the refrigerator. But if someone hands me an old can that was opened days or even months ago, I’m not interested! That’s just like if someone gives me information about certificates that’s days old—I don’t care because it doesn’t benefit me.
There is only value in understanding where your certificates are deployed if that data is fresh. Red Sift Certificates scans in real-time for all customers where CERT+ allows users to schedule scans either daily or on-demand. This means that certificate discovery and configuration checks aren’t real-time.
Red Sift
Red Sift Certificates is continuously scanning the internet in real-time and your network daily to make sure that information about new and expiring certificates is up to date. This allows teams to take action, validating issues and risks as they happen and putting remediation in place much more quickly.
CERT+
Scheduled and on-demand scans are great, but it means that real-time discovery isn’t available. This delay means that a threat that could be prevented by identifying a misissued certificate wouldn’t be identified until after the fact. Freshly issued certificates are a useful source of intelligence for other compromises too such as DNS takeovers.
Taking Action
Red Sift and CERT+ go about taking action in two different ways. Red Sift focuses on getting users the best information they need to take the required steps, while CERT+ focuses on automation and manual rule-building for notifications. Both have pros and cons, and deciding which is best for you comes down to your organization and business problems.
Red Sift Certificates
Out of the box with no configuration required, as soon as a certificate is discovered, Red Sift Certificates begins to take action. No scheduling of scans is required.
Red Sift Certificates effectively monitors CT logs, providing essential expiration monitoring and detailed deployment data with alerts by email out-of-the-box and through the API. This enables prompt identification and resolution of potential issues, preventing certificate-related system outages.
For monitoring certificate expiration, Red Sift Certificates identifies network endpoints with certificates that are nearing expiration, are in a critical state, or have already expired. Email alerts regarding upcoming expirations start within minutes of adding one domain, and reports are available immediately—customers have remediated upcoming issues within minutes of onboarding to Red Sift Certificates. This information can be exported in CSV or JSON formats for further analysis and record-keeping.
When remedial action is required for a certificate, Red Sift Certificates presents all relevant details including the host, hostname, location, last seen date, expiration date, and certificate number. This information aids in quick decision-making and problem-resolution.
Additionally, each certificate’s details, such as the hostname, network location, associated services, ports, and ASN are provided. This facilitates efficient prioritization in addressing certificate issues.
All discovered certificates, including those issued by other teams within the organization, are included in this monitoring and reporting.
CERT+
CERT+ has what appears to be a powerful workflow builder. This allows you to build out custom rules relating to lifecycle management, including monitoring for expiration dates. This means that significant setup and configuration time is required before actionable insight is received.
Scheduled scanning means that essential discovery and configuration data may be unavailable immediately.
Integrating with Your Stack
Red Sift Certificates
Integrations
Asset Monitoring Through Third-Party Integrations: Red Sift Certificates offers comprehensive monitoring of all public-facing assets and resources via integration with several third-party services to expand the scope of certificate discovery. Upon configuring an integration, Red Sift Certificates performs daily checks on assets.
The integrations include:
- Cloud Computing Platforms: Integration is available with major platforms like Amazon Web Services (AWS), Google Cloud Platform (GCP), and Microsoft Azure.
- Certificate Authorities: Compatible with authorities such as DigiCert and Entrust.
- Registrars: Works with registrars including CSC, MarkMonitor, and Safenames.
- Content Delivery Networks (CDNs): Integration support for CDNs like Cloudflare.
REST API
For users looking to leverage the Red Sift Certificates REST API for integration and automation purposes, comprehensive documentation is available. The API facilitates various functions:
- Certificate Information Retrieval: Users can retrieve detailed information about all their certificates.
- Endpoint Analysis: The API aids in quickly identifying endpoints with issues.
- Subscription to Certificate Events: Users can subscribe to notifications for new certificate events.
- Manual Certificate Uploads: The API allows for manual uploads of new certificates as they become available.
- On-demand reports: reports regarding all certificates or those with problems available on-demand through the API.
CERT+
CERT+ has a very capable API but appears to be missing on-demand reports. This means that developer time is needed to build, or users need to rely on the reporting capabilities of the user interface.
CERT+ has connectors available to a large number of certificate sources including cloud computing providers, certificate authorities, orchestration tools, zero-trust platforms, and CMDBs. They don’t appear to have any connections to registrars which is an important source of truth for what an organization should be monitoring.
So, which one to choose?
Deciding between Red Sift Certificates and AppViewX ultimately comes down to the business problems you are looking to solve. To get a better understanding of your PKI estate through continuous intelligence, automation, and integration, Red Sift Certificates is the way to go. To solve issuance and renewal challenges with automation, AppView X can offer a solid path forward.
To see how to build your PKI security, visit the Red Sift Certificates webpage.