Domain security and brand protection are key priorities for businesses in 2022. Cyber threats like phishing, BEC, ransomware, zero-day attacks, and more are constantly evolving. So, the tools you use to protect your business should be too.
With this in mind, we’re delighted to announce the latest addition to our cloud email security and brand protection application: Red Sift Brand Trust.
What is Brand Trust?
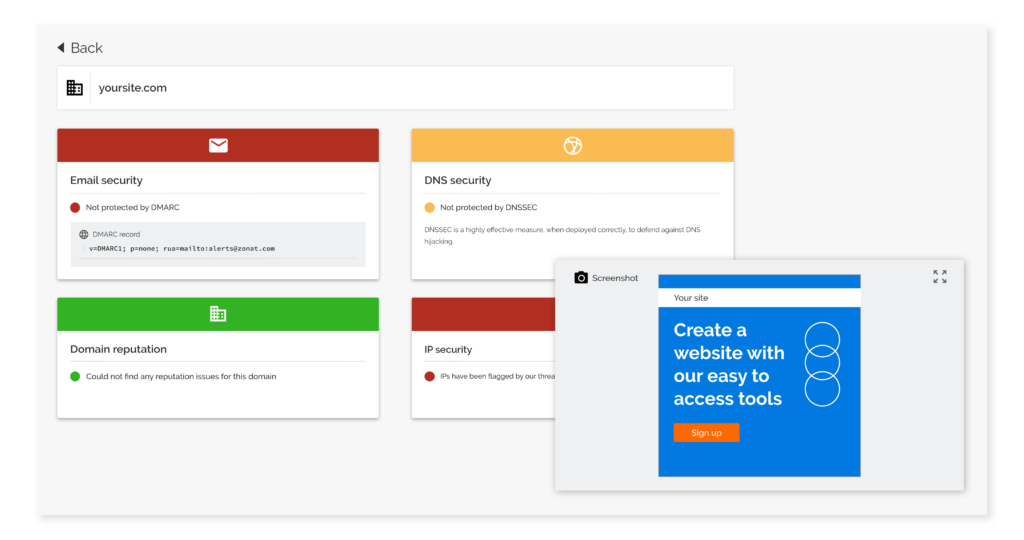
Brand Trust observes the internet in near real-time to stop bad actors from creating phishing campaigns before they even have a chance to launch them. It provides security personnel with the most comprehensive insight into their domain perimeter, plus an integrated phishing takedown service.
Unlike other domain monitoring products that only look at top-level domains (TLDs), Brand Trust monitors 150 million newly registered domains and subdomains every day, uncovering any parked and forgotten domains, as well as impersonation sites. It constantly absorbs and examines intelligence from a wide array of data sources, including rasterized web snapshots, certificate registration, DNS signals, live spam data and more, in order to paint the full picture of a domain’s health and validity.
It enables security personnel to sort threats by their imminence, save time with event-driven alerts, and issue takedown notices once an impersonation domain has been identified.
“For organizations to truly secure their domain perimeter, they need the ability to identify threats before they can be weaponized. Brand Trust makes it easy for security teams to define and visualize their complex domain estates in order to identify and disarm phishing attacks on day zero – before they launch. In doing so, we’re delivering a solution that helps organizations identify and continuously protect the entirety of their digital asset base.”
Rahul Powar, CEO Red Sift
How can I take down phishing websites with Brand Trust?
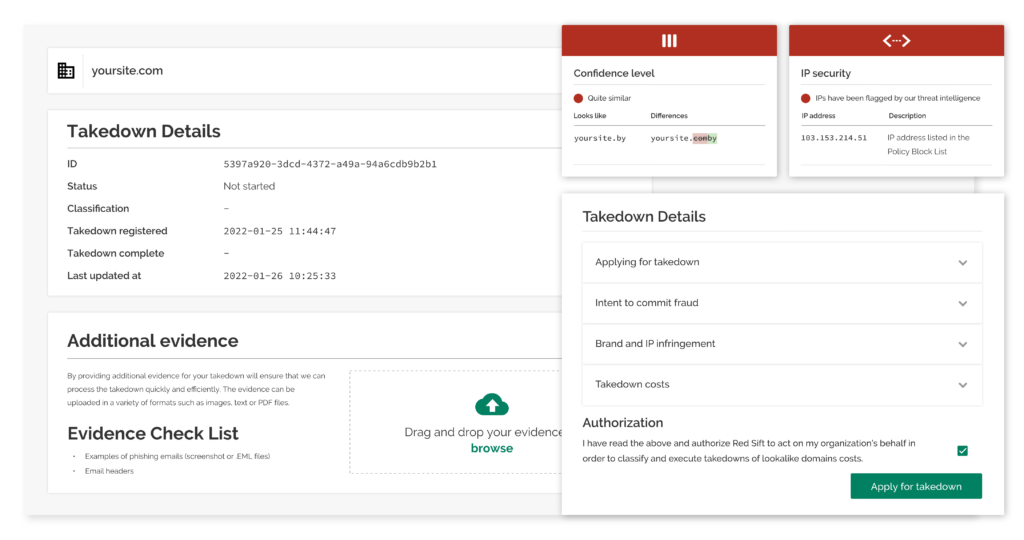
Brand Trust’s integrated takedown functionality leverages existing relations with registrars and hosting providers to quickly effect domain takedown.
Our solution collects evidence on the offending domain, classifies if lookalike domains intend to commit fraud or brand infringement, and displays this data to users through a single pane of glass for their review and sending for a takedown. Users can check on a takedown’s status at any time and will also be alerted if the takedown status is updated.
Brand Trust also helps tackle ‘shadow IT’ by proactively identifying unprotected yet legitimate domains that may have been created without your IT department’s knowledge.
In addition, machine vision-based logo detection discovers the use of counterfeit brand assets across impersonation domains. This additional infringement classification piece provides domain registrars with the evidence they need to effect takedowns even faster.

Complete brand protection with Red Sift
Brand Trust is the latest addition to the Red Sift portfolio and works interoperably with our existing email security product, Red Sift OnDMARC. It integrates with OnDMARC for a detailed view of an enterprise’s existing domains. This means that data and processes can be shared across different branches of an IT department, providing organizations with layered, enterprise-level threat protection.
To start protecting your brand, logo, digital assets, and domain perimeter, start your free Brand Trust trial today!







