Ever wondered about how whale phishing differs from spear phishing? Well wonder no more as Gino explains it all in this article for IT ProPortal.

Ever wondered about how whale phishing differs from spear phishing? Well wonder no more as Gino explains it all in this article for IT ProPortal.

Verified Mark Certificates (VMCs) and Common Mark Certificates (CMCs) continue to evolve, and staying up to date is crucial for organizations looking to authenticate their logos and enhance brand trust in email communication, this includes adhering to version 1.7 of the Minimum Security Requirements. In this blog, we break down the 5 key changes…
Read more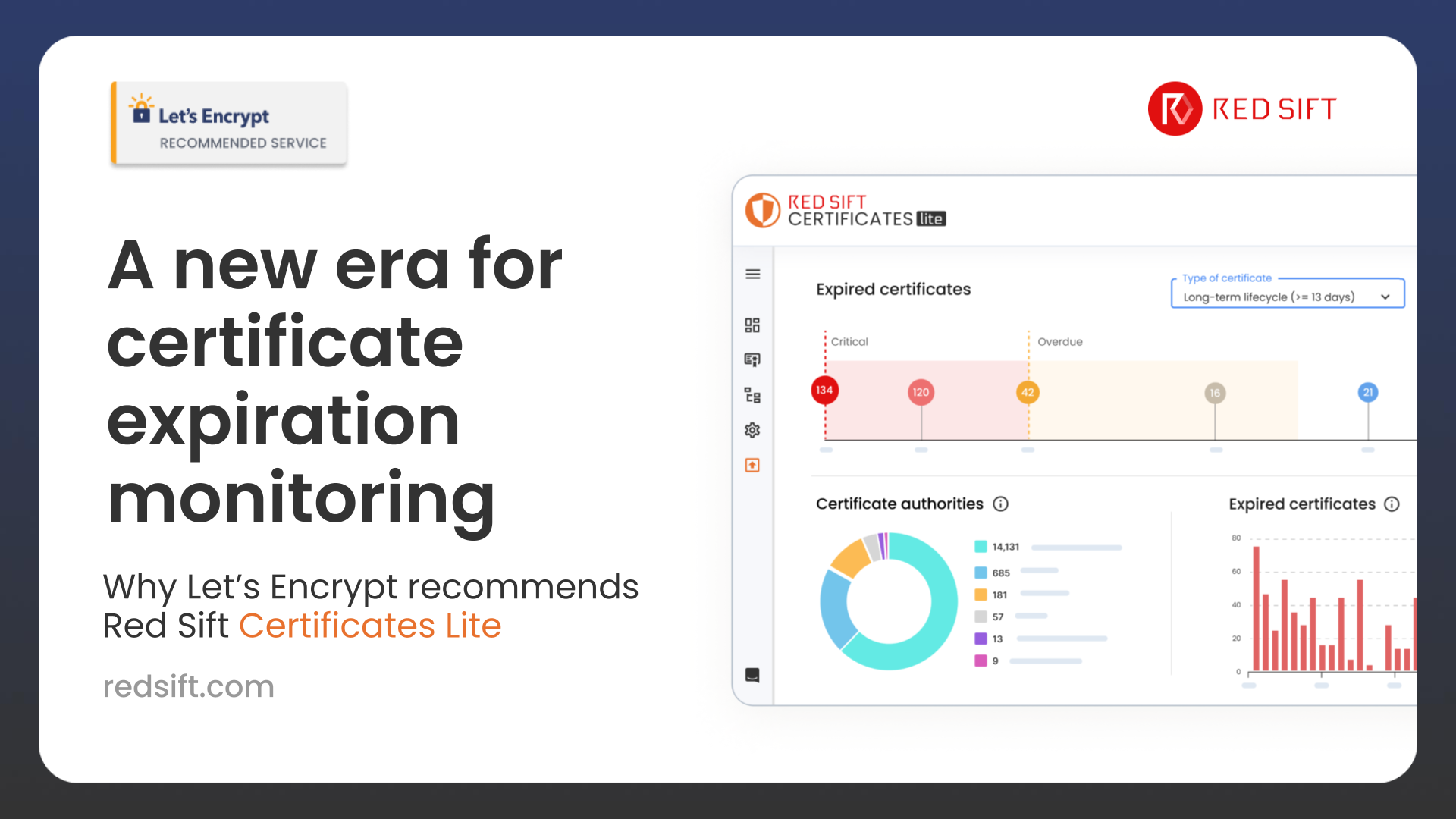
Every day, businesses rely on TLS certificates to keep their digital operations secure. But when those certificates expire unexpectedly, the consequences can be severe—websites go down, critical services break, and customer trust is lost. Even as automation has made certificate issuance and renewal easier, it hasn’t eliminated the problem. Organizations still find themselves blindsided…
Read more
The traditional approach to cybersecurity—often tacked on as an afterthought—needs a serious overhaul. This was the consensus in the recent MN-ISSA sponsored fireside chat titled “Moving Cybersecurity Upstream to Achieve Resilience,” where industry experts gathered to explore the integration of security measures right from the early stages of software development and strategic planning. Held…
Read more
In January 2025, Let’s Encrypt announced a major step forward in enhancing web security: the introduction of six-day certificates, also known as “short-lived” certificates. This initiative aligns with Let’s Encrypt’s commitment to strengthening the Public Key Infrastructure (PKI) ecosystem and is set to roll out for general availability by the end of 2025. Why…
Read more