We are delighted to announce the beta for Red Sift Radar – our new LLM assistant for security teams.
With Red Sift Radar, teams will be able to use an LLM to automate manual checks, drive security consistency, and build bridges with less technical teams.
To bring this to life, we have taken base LLMs and combined them with our internet-scale data feeds and the hundreds of real-time APIs that power our existing applications to create something new.
With Radar, operators can investigate the real-time cybersecurity posture of internet-facing assets using our Hardenize capabilities or diagnose web and email security issues from points of presence around the globe. All of this is exposed to our end users via a familiar chat interface that requires virtually no specialist knowledge to operate.
This is our latest innovation in making AI a tool for defenders, who face a growing number of threats every day.
Red Sift (and Hardenize) customers on an Enterprise plan can now access these new capabilities by indicating their interest.
The Need for AI for Defenders
Cybercriminals were some of the earliest adopters of AI. Generative AI allows users with criminal intentions to write very convincing copy at scale for phishing emails, create more convincing social engineering ploys, and write malicious code to name just a few examples.
But GenAI does not provide the same out-of-the-box benefits to defenders.
Security teams need real-time information and the ability to automate. LLMs are great at capturing nuanced patterns, generating human-like text, and performing wide range of language-related tasks. But, with complex problems requiring multiple steps, particularly in the cybersecurity domain, responses from LLMs are still inconsistent, incomplete, and incorrect at times.
Enter Red Sift Radar
We set out to make LLMs more useful to security teams. To accomplish this, we had to introduce three innovations:
- Steering the LLMs to improve the consistency of multi-step problem-solving while retaining the ability to diagnose newly encountered problems.
- Integrating standard and proprietary tooling to enable real-time sensing of internet-connected resources.
- Integrating internet-scale data sets when required to extract insight that is not available directly from these internet-connected resources.
Steering the LLMs
One way of thinking about today’s LLMs is to imagine them as lossy compression algorithms for the entity of human knowledge as expressed in their training data (the Internet). While this is incredible to witness, getting them to function consistently on tasks that are less creative writing and more functional requires some work. To this end, we have built a novel steering mechanism that operates behind the scenes of a familiar chat interface to improve the reliability of driving the LLM.
Integrating standard and proprietary tooling
While our steering gives the model context, it remains limited in its ability to measure the here and now. This is where our existing capabilities come in. Over the years we have built broad APIs and data sets that measure the signals relevant to cybersecurity on the internet. We maintain public resources such as bimiradar, free tools such as Hardenize and Red Sift Investigate along with hundreds of APIs to power our products. When we expose these granular capabilities to the model and combine them with the steering above, we see magic happen.
Internet-scale data
Next come our sensors and data partnerships. While these capabilities are not released in the beta we are announcing today, this is in testing and we can see some incredible insights appear when we expose this type of data, appropriately pre-processed to scale it down, to our model.
The result of all of this is an LLM-based security assistant that can provide insights into the security status of organizations by examining internet-facing assets like DNS, domains, subdomains, certificates and IP addresses, consistently and with with proper context.
Using Red Sift Radar
Ask the questions your team needs answered
Like ChatGPT, using Red Sift Radar requires the user to begin with a single question she wants to answer. Users can ask prompts like:
- What is the security posture of {mydomain}?
- Does {mydomain} have DMARC set up correctly?
- Can you check if port 80 is open on {mydomain}?
- Check to see if my website is loading correctly or has any problems.
Once your question is processed, Red Sift Radar determines the most appropriate action or response tailored to your inquiry.
Get specific answers
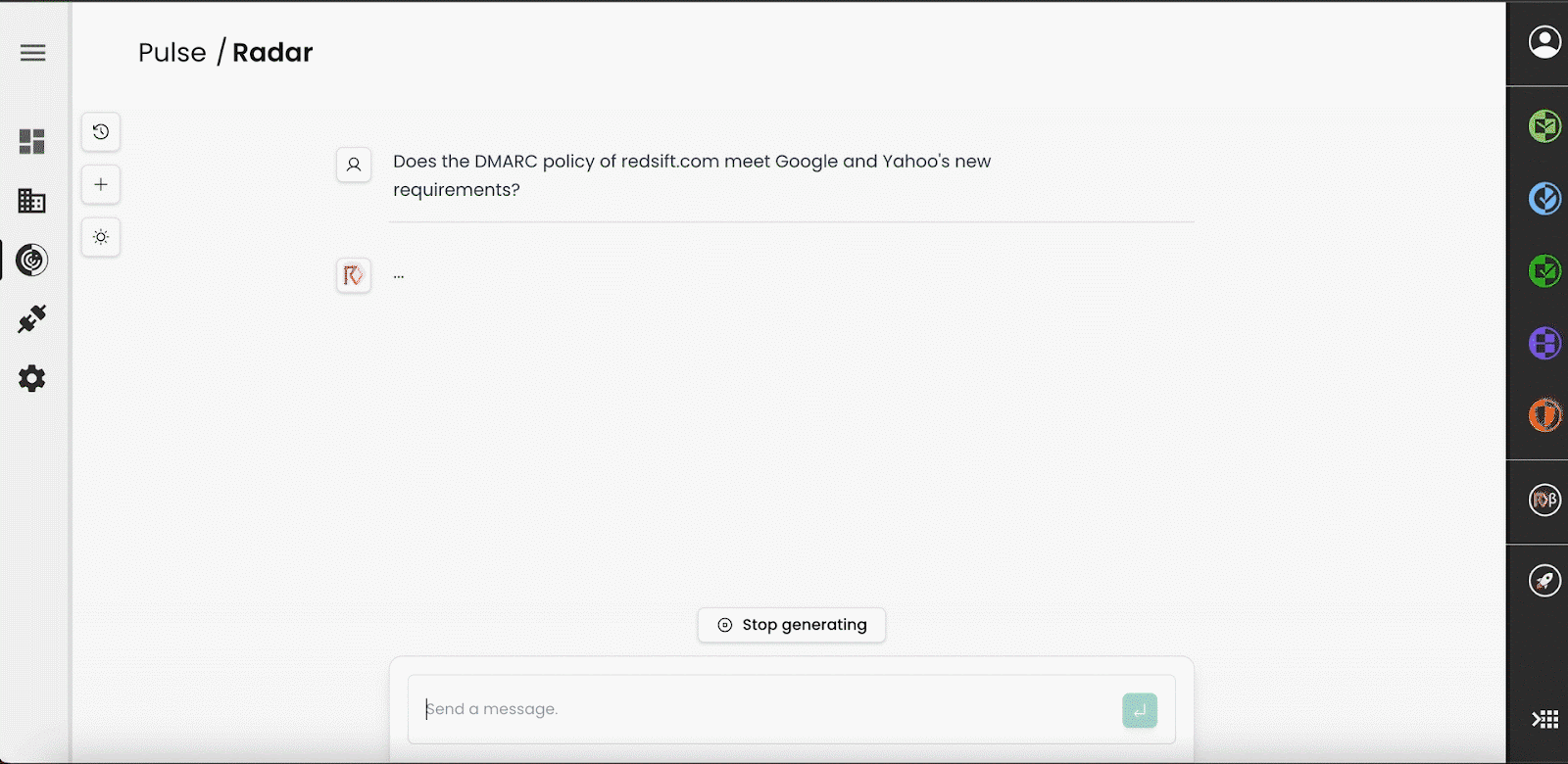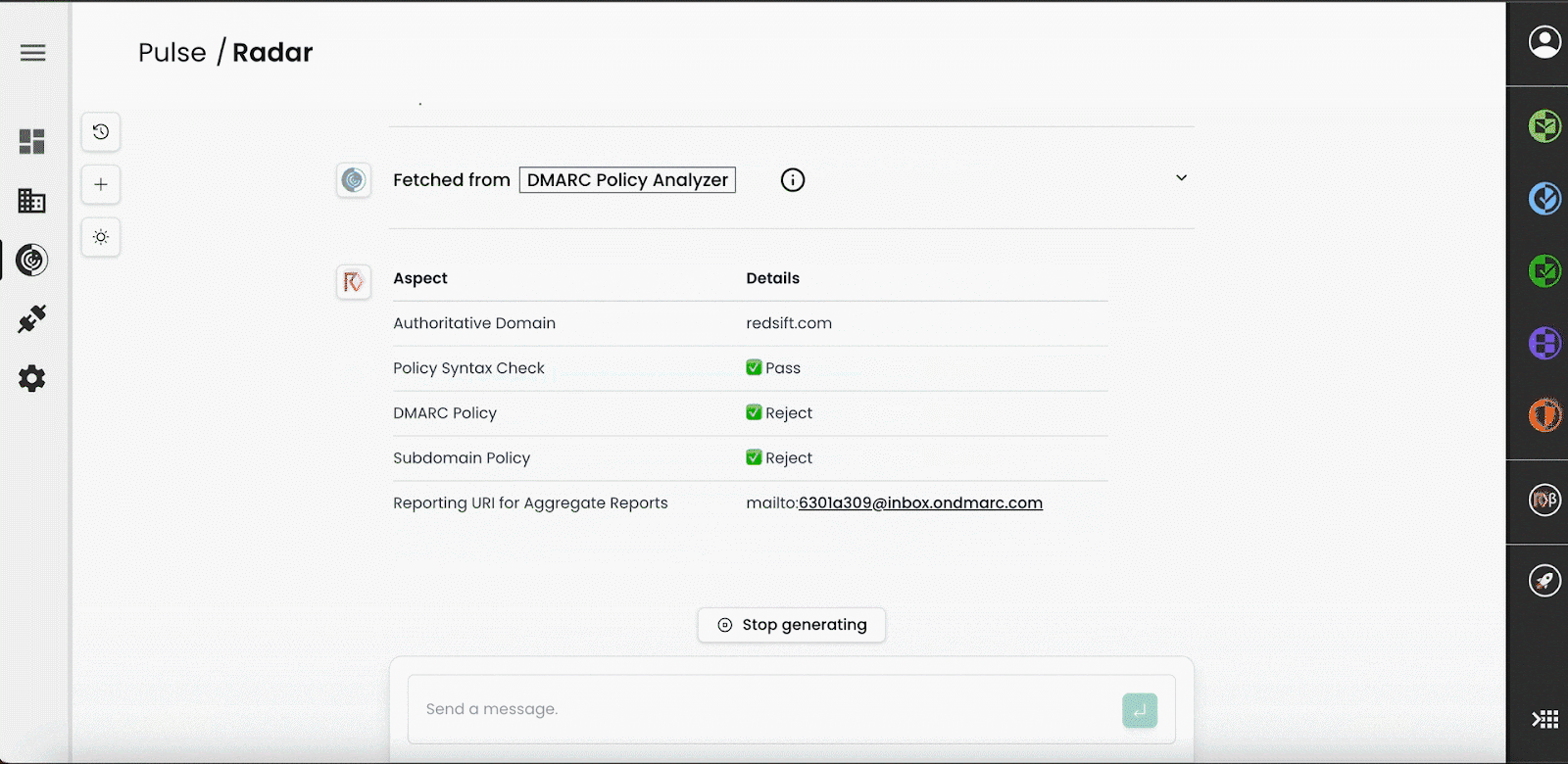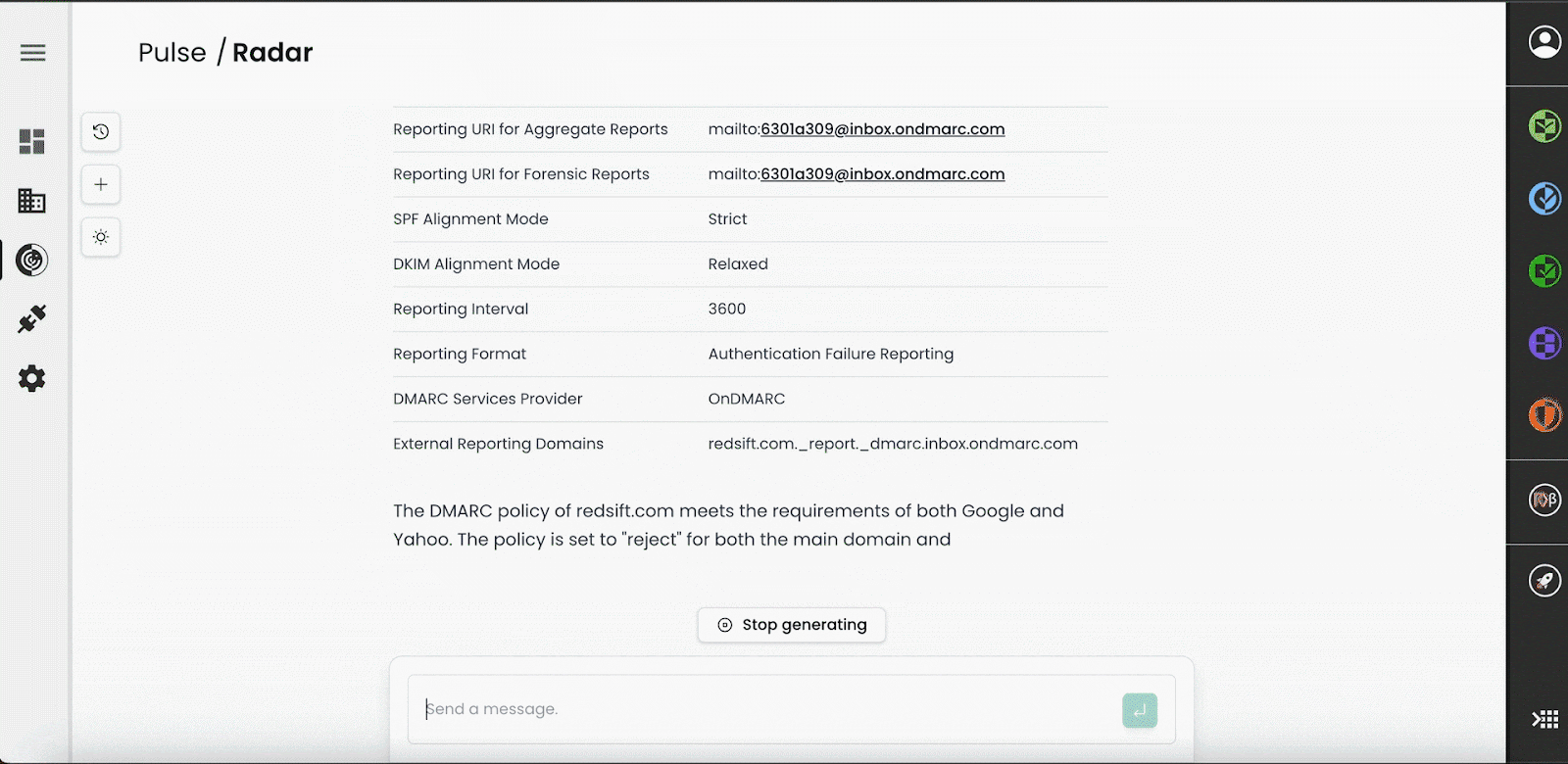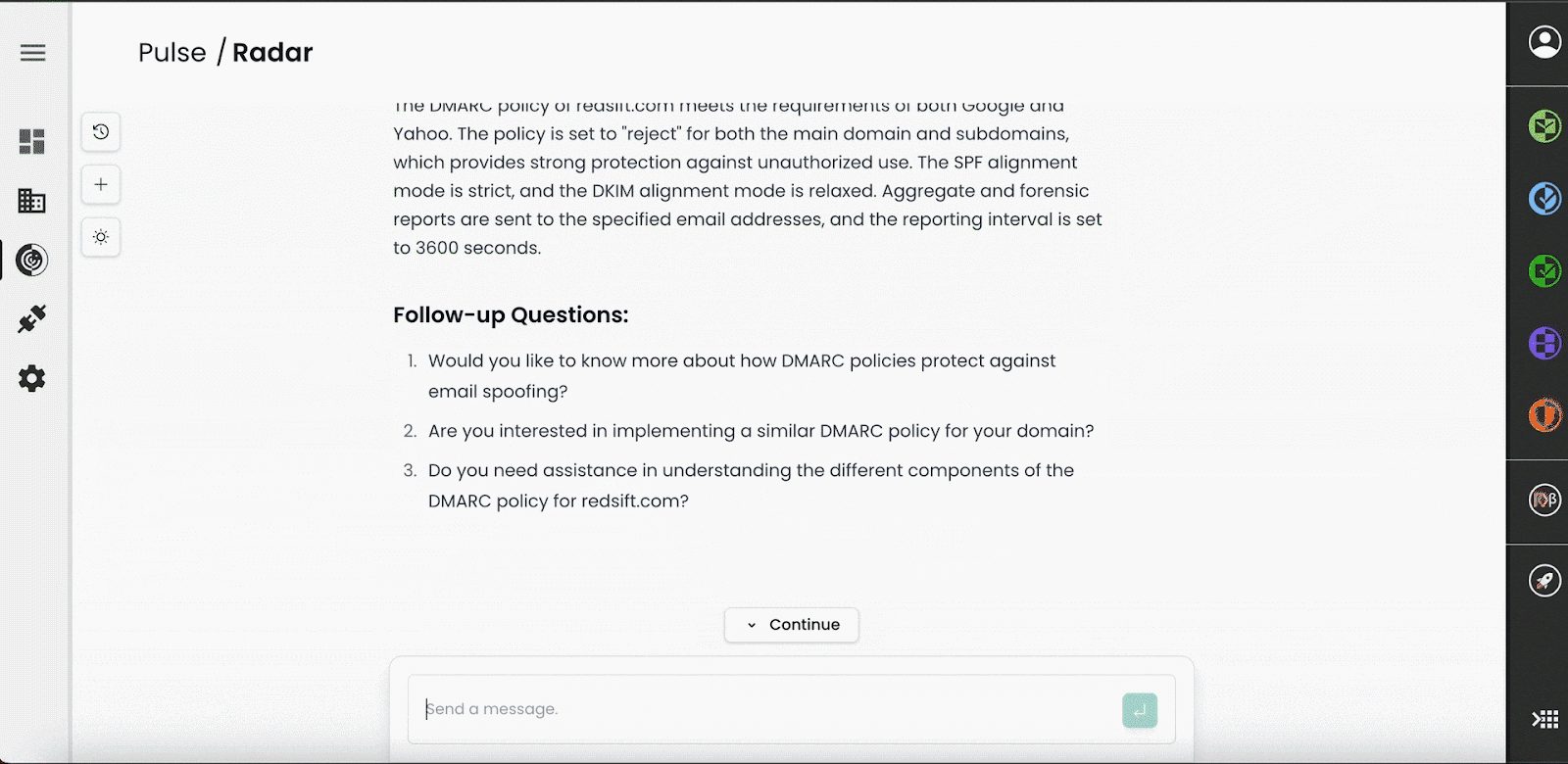
Take a scenario where you pose the question, “How secure is {mydomain}?” In such a case, Red Sift Radar performs a comprehensive analysis using a variety of lookups and checks, including:
- Domain Records: Evaluates DMARC, SPF, MX, NS, BIMI, DKIM, and MTA-STS configurations.
- Subdomains: Lists and analyses associated subdomains.
- Certificates: Checks SSL/TLS certificate status.
- Website Security: Assesses hosting server and website vulnerabilities.
- DNS Health: Reviews DNS security and configurations.
- IP Analysis: Examines exposed services and geolocates IP addresses.
Depending on your query, Red Sift Radar performs a variety of tasks, from evaluating the security posture of a domain to checking for potential misconfigurations. This versatility ensures that you get precise and relevant information every time.
Build bridges across your team and organization
The adaptability of Red Sift Radar to different security-related tasks and its ability to understand and generate human-like text make it an invaluable tool for security professionals.
After an initial security query, users can ask follow-up questions to help make information consumable and actionable across an organization. Example follow-up queries include:
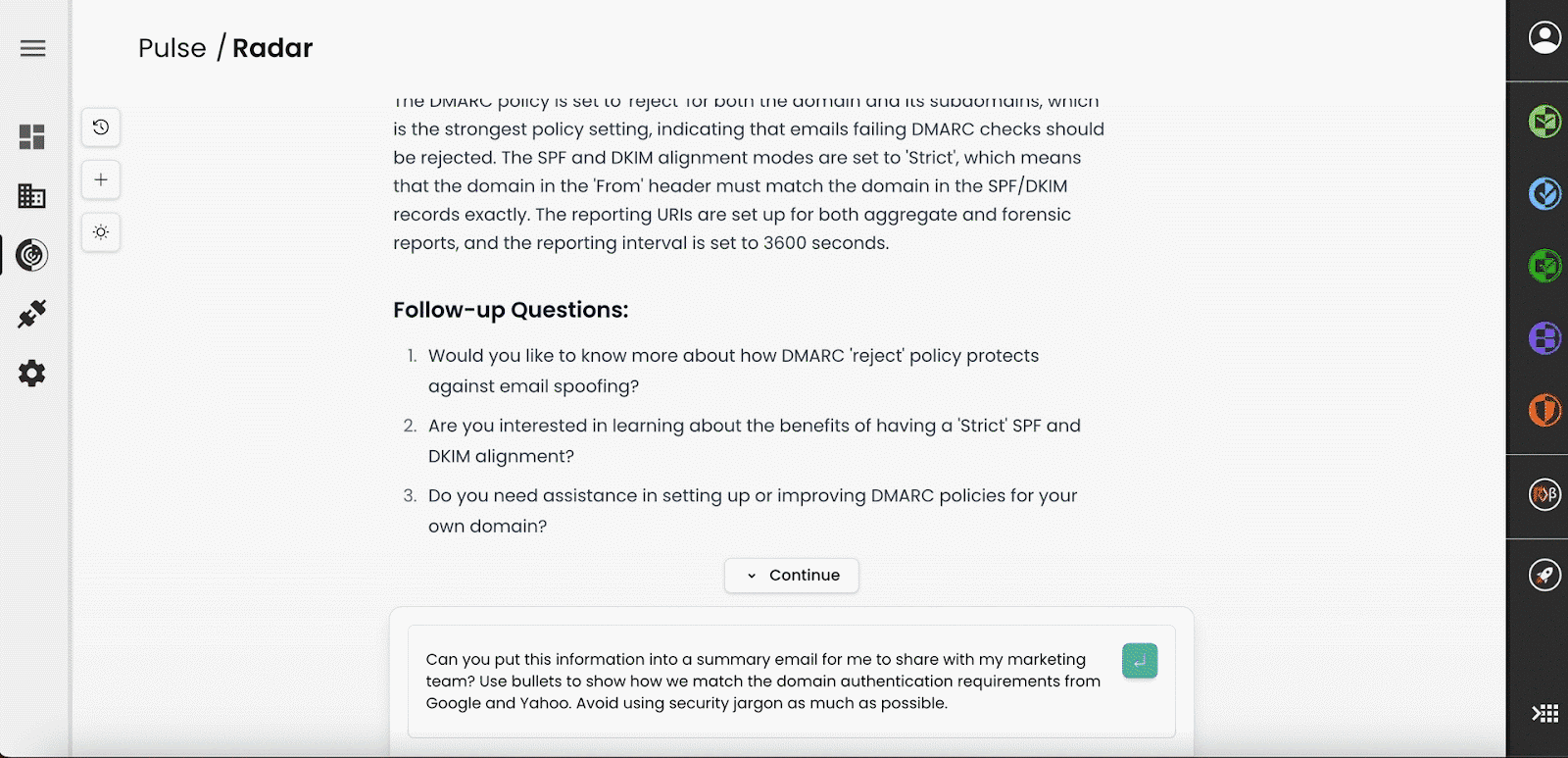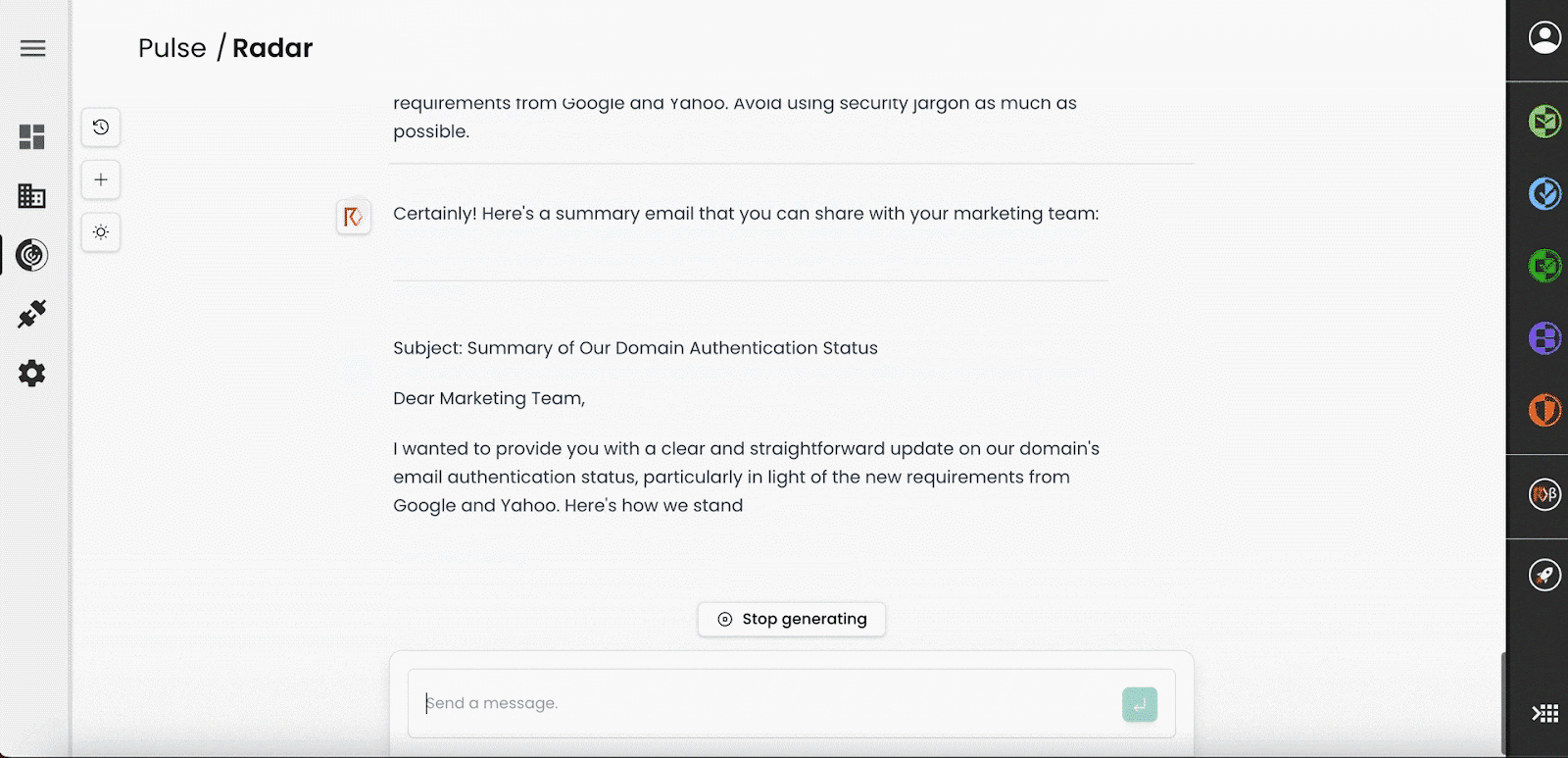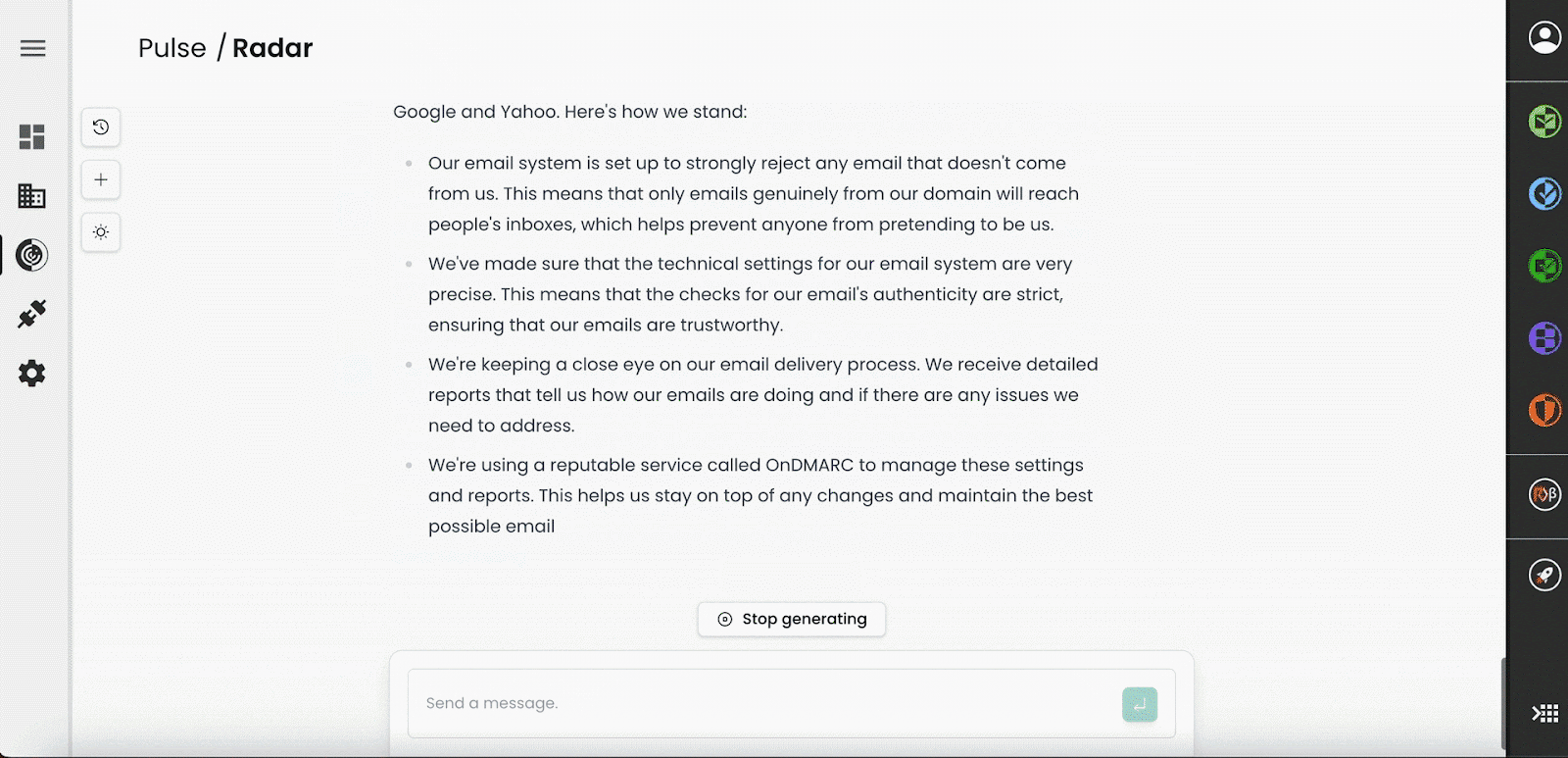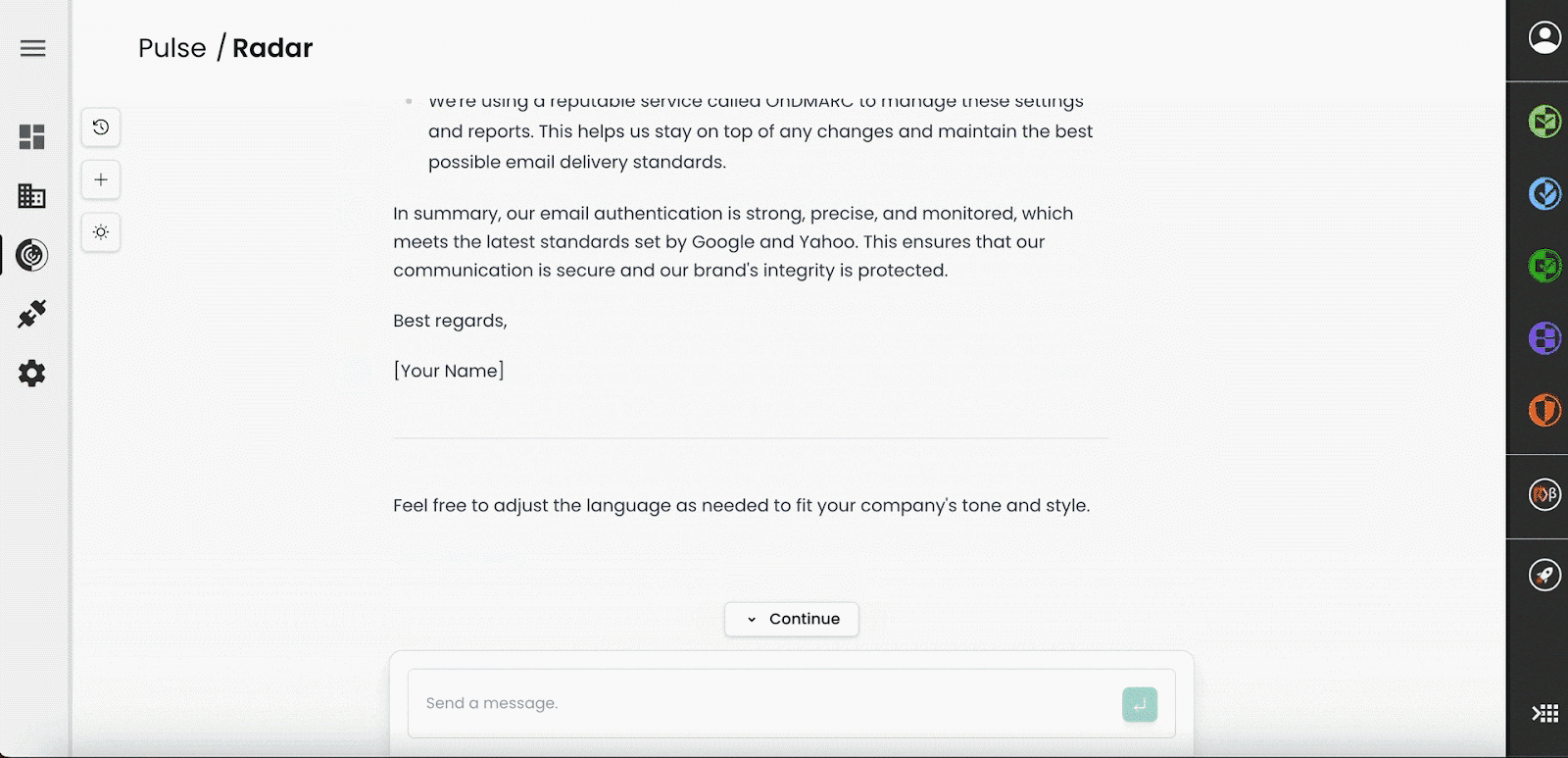
- Can you summarise this information for me?
- Our security division is in France; can you translate to French, please?
- Can you check if my website is working from different sites around the world?
Performing complex security analyses
So far we have demonstrated fairly straightforward requests but this gets very exciting when users go off-piste.
For example, a more comprehensive query could involve DNS change propagation around the world.
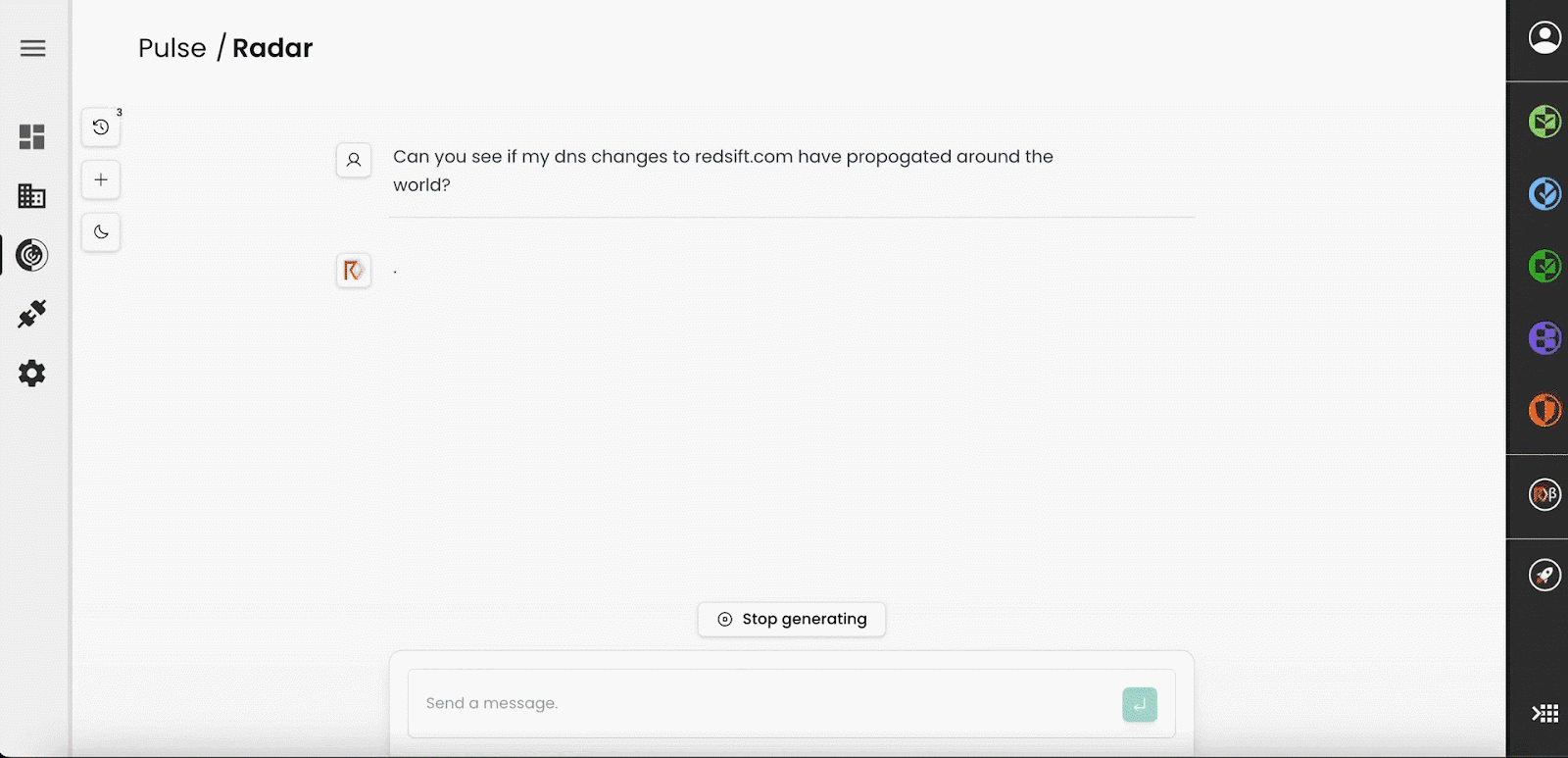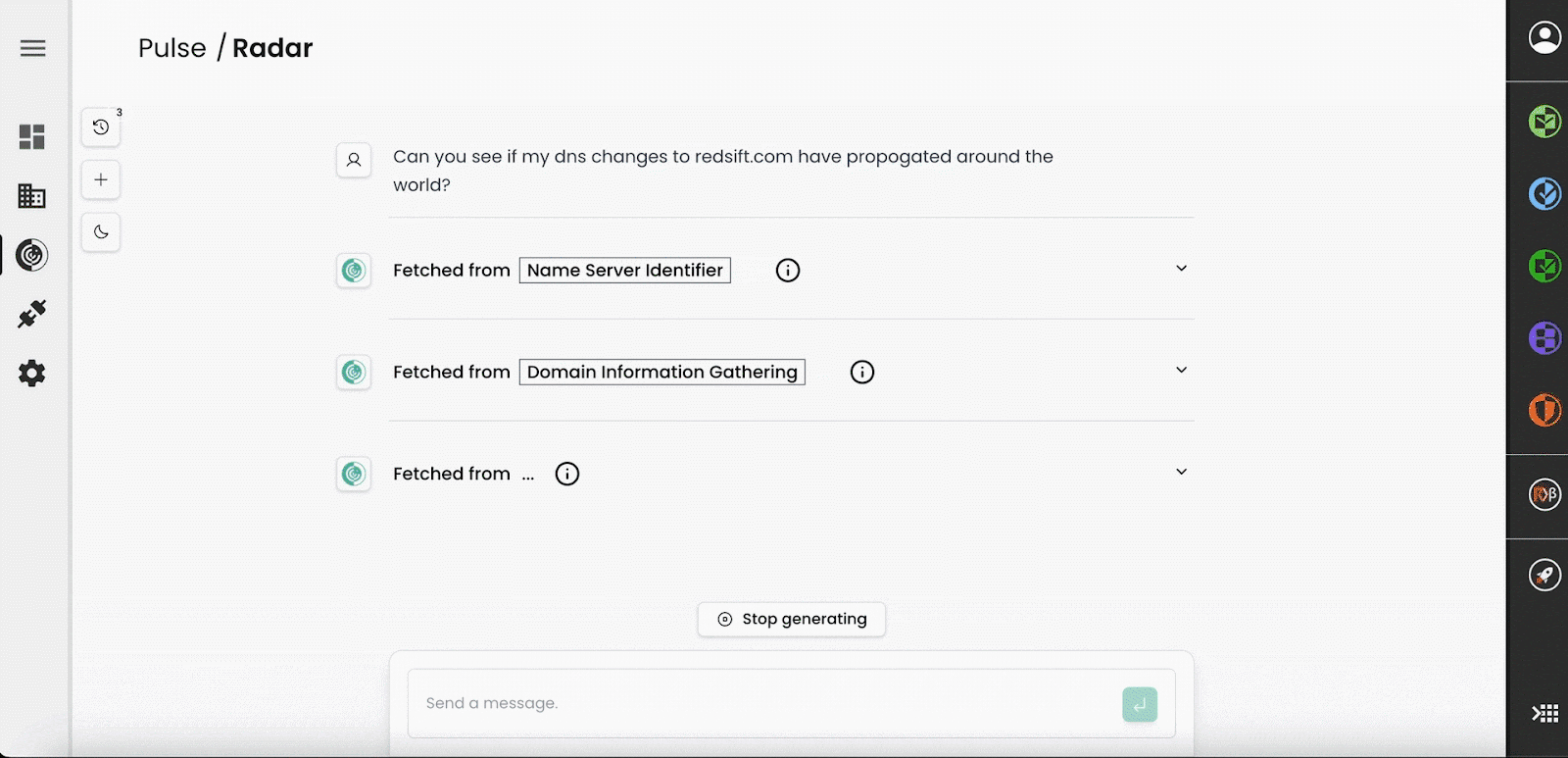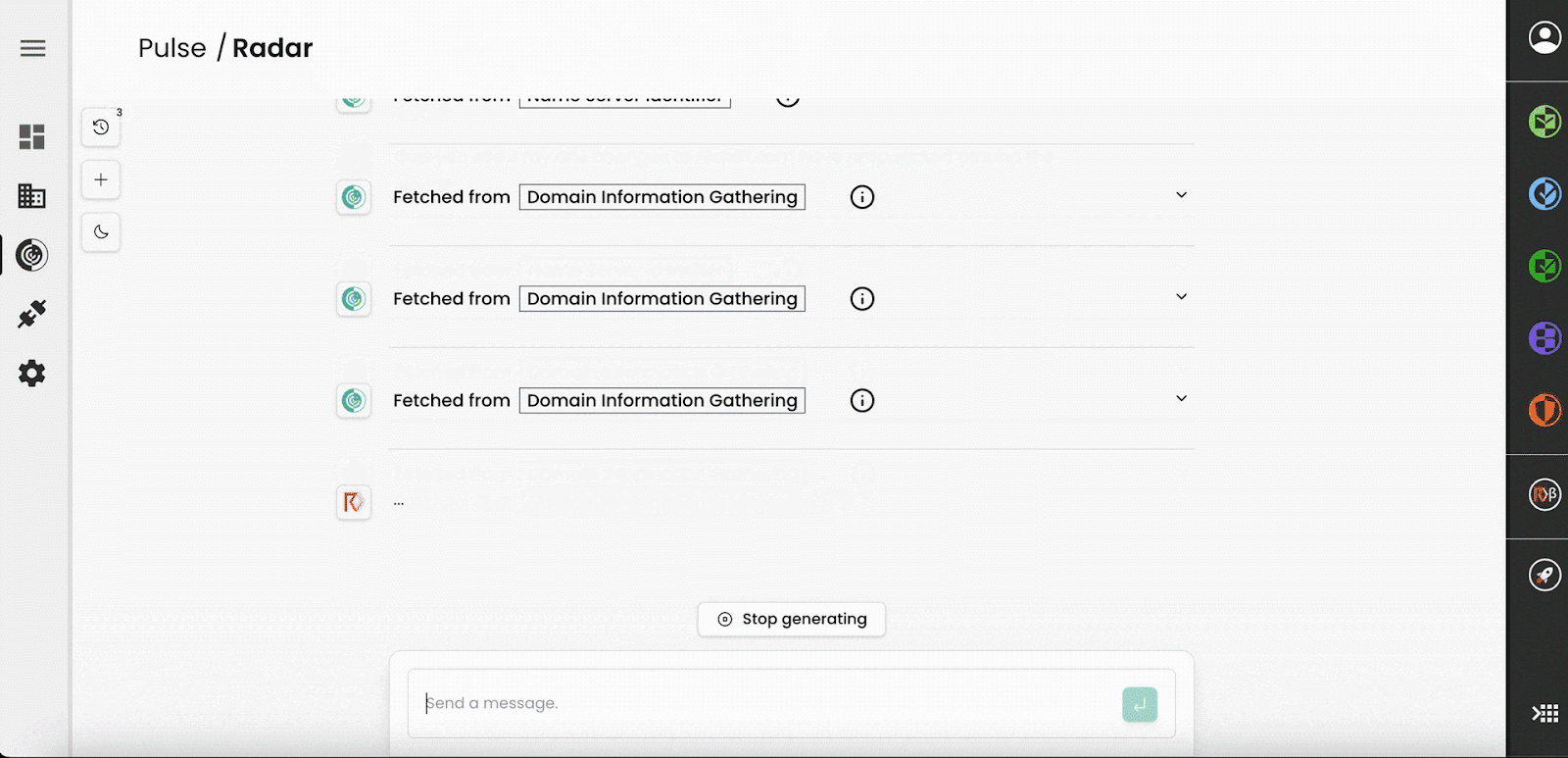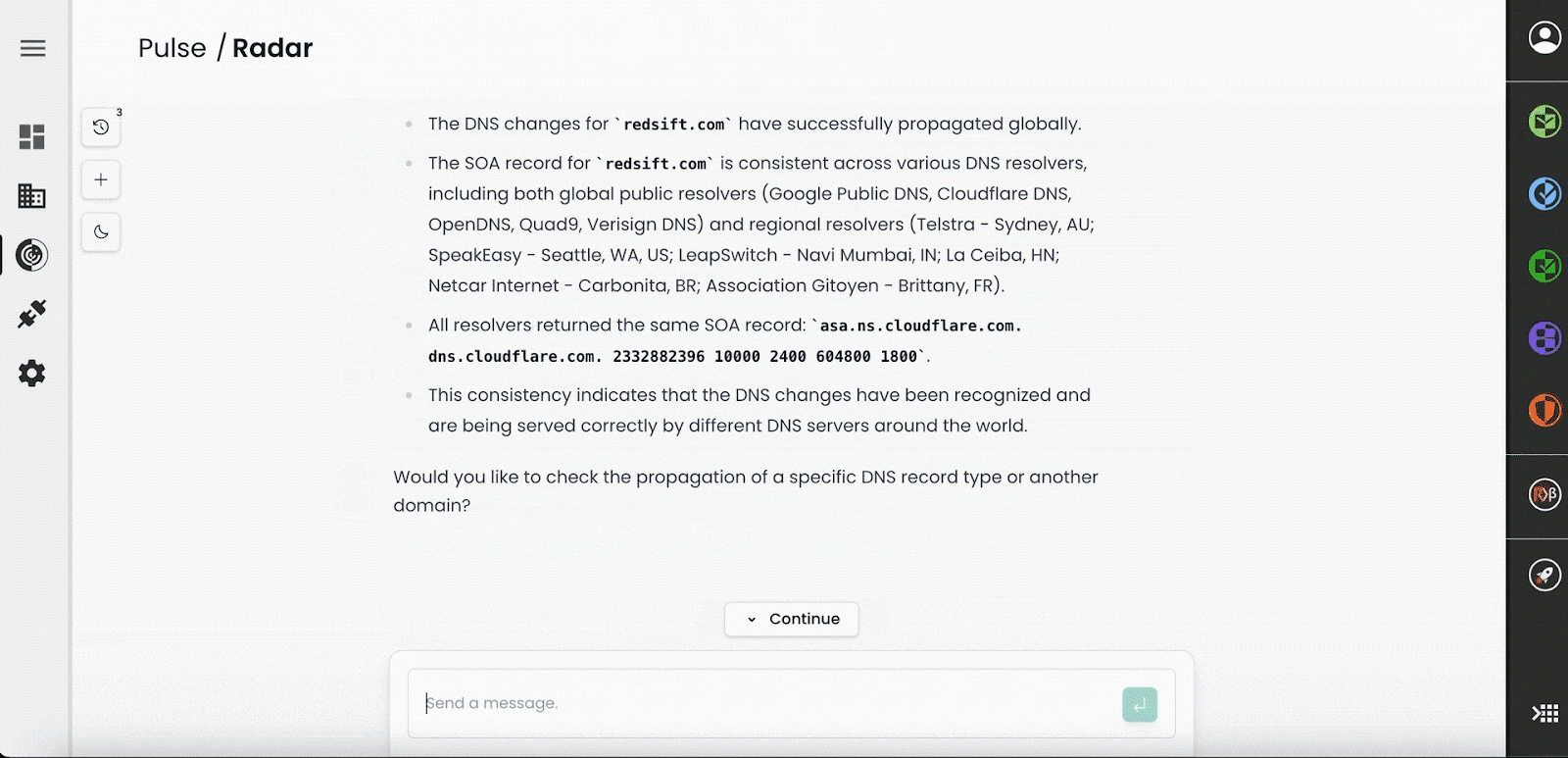
Here the models knows how to use Red Sift’s different points of presence across the globe to interrogate both global and local consumer DNS servers, synthesising a view on these technical details with one easy query. The alternative would require a mass of VPNs, terminal commands and operator time and expertise.
We can also see some incredible insights appear when we ask Radar to compare the security posture of multiple assets on the internet and highlight the material differences.
The Outcomes: Consistent, proactive security at scale
The biggest benefit for users we have seen to date is the ability to automate manual tasks that are time-consuming but business-critical.
Take the example of “what is the security posture of {mydomain?}”
To answer this question without Red Sift Radar, a security analyst would have to manually check web, email, and infrastructure security information across tools, have a good knowledge of basic CLI prompts, and understand how to translate their findings into a summary for the business.
Our early adopters are using Red Sift Radar to eliminate the manual nature of these tasks and are on average saving 10 hours per week. This time savings is paired with the value of consistency – the same things are checked in the same way each time, no matter who from the team is responsible.
Is this a GPT?
We have been early adopters of the GPT stack starting with the release of GPT-3 back in 2020 and initially prototyped Red Sift Radar as a plugin running on top of the public version of GPT-4. However, it was apparent that we were exposing a lot of power to the model and we remained cautious about the risks associated with free for all access to this capability. We also started to hit technical limitations with the size of the context that was available in the consumer version of the Chat GPT LLM and decided instead to bring the LLM to our platform so we can build a safer and more capable experience.
What’s to come?
We cannot wait for Red Sift Radar to be in the hands of our customers. We look forward to using the beta program to get user feedback and continue improving our capabilities. We will start inviting customers we think could be a good fit for the beta this week. If you haven’t yet received an invite and would like to participate, make sure to share your interest if you would like to join. Our wonderful Product and CS teams will follow up with all requests within a week.
At the same time, we will continue to progress towards a generally available version accessible to all Red Sift customers. Plans include the ability to query across your Red Sift applications and go deeper than publicly available security information. And, rest assured that we will be using this time to perfect Radar’s Dark Mode.
It is critical to note that we are taking every step to ensure Red Sift Radar is not used for malicious purposes, such as gathering information to exploit vulnerabilities or for reconnaissance. To mitigate this risk, Red Sift implements best practices in security and privacy, including access controls, monitoring, and responsible disclosure policies, and will continue to do so at every stage.