What does it take to secure an $18bn fund from cyber attack? On the 1st of December, we hosted Dan Bennett, CTO of Castlelake for a webinar to find out. We were joined by Rois Ni Thauma, Head of Cyber Governance here at Red Sift. Beyond this individual challenge, we were interested in how the security of one firm in a tight-knit industry can give charge to a network effect that contributes to protecting all firms and investors from dangerous and costly email impersonation attacks.
Castlelake is a global private investment firm that specializes in asset-based opportunities. As CTO, Dan is responsible for both the firm’s overall cyber security as well as their use of software to optimize returns and increase the effectiveness of their assets’ operations.
I started my career in finance, so this is a bit of a return to the nest for me. Before joining Red Sift, I spent about seven years in investment banking and private equity working with firms that on the surface look just like Castlelake. None however leveraged software quite as elegantly and effectively as Dan and his team.
Teams that bring to bear software as a way of doing things faster and more reliably are more likely to win. I like to believe that it is this approach that led Dan to choose Red Sift’s OnDMARC as the firm’s outbound email authentication and DMARC solution.
On a recent call with Dan we got talking about the number of counterparties trading with weak outbound authentication. I volunteered to dig further and use our technology to scan the entire SEC-regulated universe for email authentication policies, or lack thereof.
What we have here is a failure to authenticate
We started by grabbing a list of all 18,281 firms registered with the Security and Exchange Commission. Then, for the 15,254 firms for which a web domain could be found, we analyzed their DNS to find their DMARC policy and SPF records. For an industry that depends so heavily on trust, the results are quite grim.
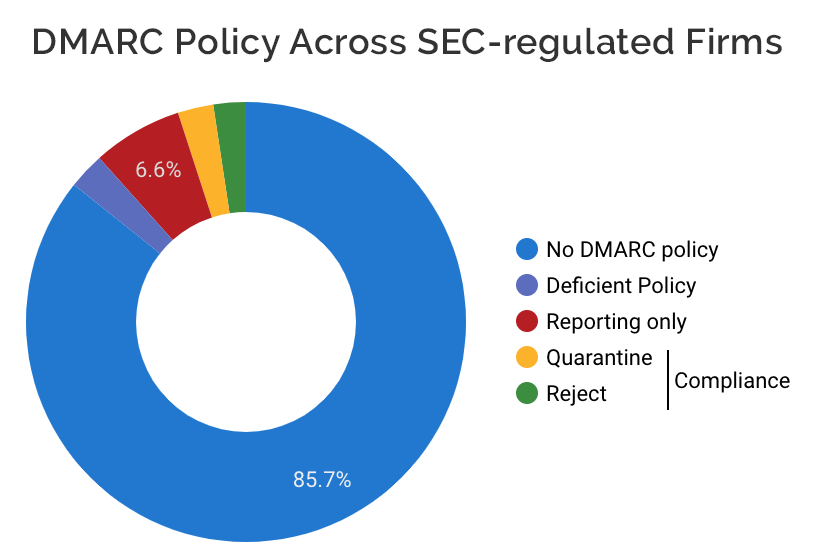
Only 5% of all firms have adopted DMARC in protection mode, a policy whereby unauthenticated emails sent on their behalf are rejected or quarantined by the receiver.
Barely 12% are gathering DMARC reports at all, creating a large blindspot for attackers to exploit.
It’s worth noting the huge diversity among the body of firms that are regulated by the SEC. They range from large bulge-bracket banks to ‘mom-and-pop’ brokerage firms with retail investor clients as well as fast-moving fintechs with a license to disrupt. This puts a huge array of counterparties at risk of becoming victims of impersonation, all with varying degrees of sophistication in cyber defense.
During our conversation, we hypothesized that it is perhaps this diversity that has led to slow adoption. Although large banks were some of the first adopters of DMARC, it has failed to ‘trickle-down’ to the vast majority of smaller firms, as our data shows. In other industries, such as construction, large contractors hold huge sway over entire value-chains, leading to rapid adoption of standards like onsite safety. Such effects are weaker in finance where supply chains are more diffuse or even circular in nature. If pressure does not come from the regulator then it is left to firms to secure themselves and influence their immediate network.
Dan noted that “email is by far the predominant way that finance is communicating with its ecosystem of counterparties, vendors, and suppliers. Probably at a volume and level of dependence that surpasses other industries because of the nature of relationships”.
The security network effect
When it comes to email, it really does take two to tango. It is as much the responsibility of a receiver to verify the provenance of a message as it is of the sender to make that provenance verifiable in the first place. That is precisely the role of DMARC and the two protocols, SPF and DKIM, on which the standard is built.
CISOs and CTOs like Dan at Castlelake are increasingly taking this principle a step further by insisting that counterparties get their outbound authentication in order. They are doing so by increasing their alertness on the inbound and placing harsher scrutiny on emails that do not meet basic authentication standards. “People in glass houses can’t be throwing stones. I can’t be turning up the controls on my gateway to restrict an email coming based on inherence to these protocols unless my house is in order”.
Getting your house in order
Outbound email authentication is often a harder sell: Because it is outbound, it seems by definition to be someone else’s problem. But in finance, what seems like someone else’s problem can quickly become a systemic risk. It is therefore a foundational part of today’s security stack and a necessary component of “getting your house in order”.
“We have an obligation to secure every email we send out as well as those we receive. You need to be careful who you let in through your front door, but equally as cautious if you’re sending nasty people out of your house.”
Dan Bennett, CTO at Castlelake
When business returns depend on frequent and seamless transactions with a growing set of trusted partners and counterparties, blocking malicious actors from impersonating Castlelake externally is just as important as defending against outside threats looking in.
Luckily, implementing outbound email authentication is a lot easier than it used to be. Thanks to DMARC reporting and software solutions like OnDMARC, the job can be mostly automated. The biggest fear of most businesses implementing DMARC protection for the first time is accidentally blocking legitimate email either during implementation or afterwards when adding new sending services. Our software is built with dynamic email environments in mind and makes configuration clear, observable and reliable so that team’s like Dan’s can focus on the next threat while making the financial services safer for everyone involved: “It’s now part of the architecture of our firm. It’s something that is running and we simply monitor.”







