According to the FBI’s 2019 Internet Crime Report, Business Email Compromise (BEC) attacks cost businesses $1.8B, with 94% of all data breaches originating from phishing attacks. Modern BEC attacks are becoming not only more common, but also more successful. The improved effectiveness of these attacks stems from hackers creating elaborate campaigns that cover tracks and evade signs of detection. To improve the success rate of their campaigns, cybercriminals are meticulously researching their target, its supply chains and users, leveraging company news and events, and tracking social media channels.
Although these attacks are a global threat across all industries, the financial sector is typically a primary target. According to the American International Group (AIG), BEC attacks are the top cause of cyber claims with the financial services industry accounting for 15% of all claims made in 2018. Whether they are the main target of the attack or a means to a target, banks are often pursued due to the large volume of phishing attempts they receive and numerous high-value transactions.
Criminals in general are typically interested in where the money is. Cyber criminals are no different. Instead of having to physically break into a bank like an old Hollywood style robbery movie, we are seeing an increase in cyber heists where the criminal does not have to physically break into a property to take any money away. This makes these heists much “safer” for the criminals and can be far more lucrative, as they are not only taking what is available at present.
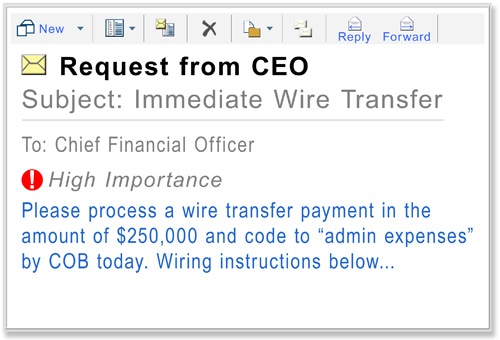
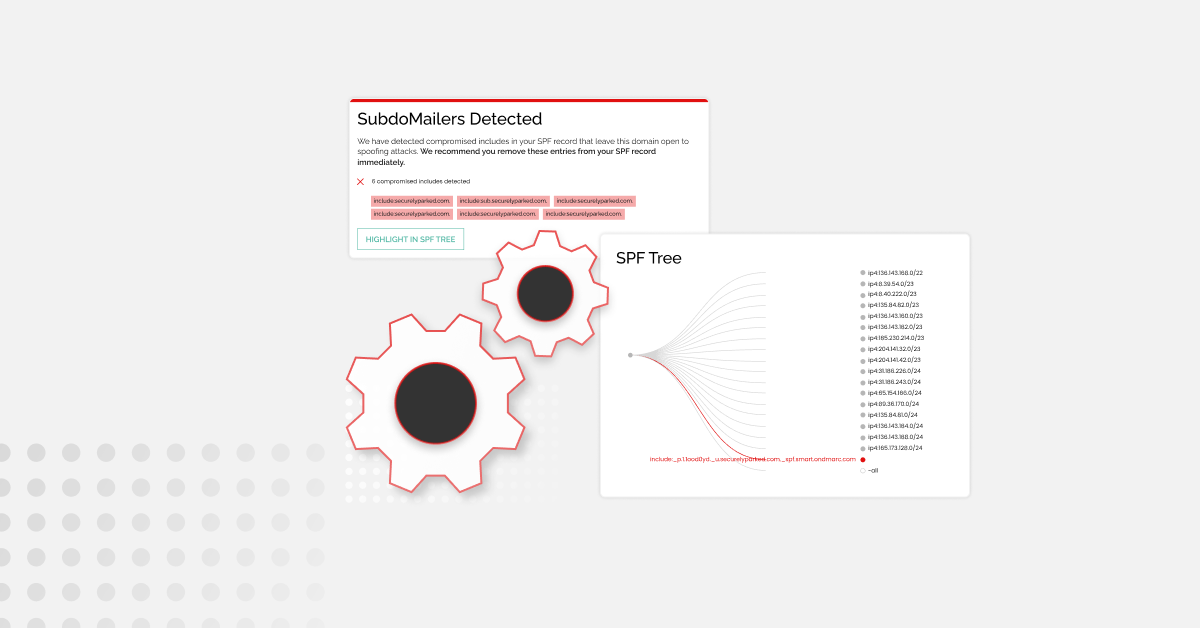
Cybercriminals are often heavily armed with rich information about their targeted organisation and its supply chain. Taking a note that the vast majority of data breaches have originated from a BEC attack, it is not surprising that adversaries are crafting highly credible, targeted emails that are virtually indistinguishable from those sent by colleagues, clients, and suppliers we are communicating with on a daily basis.
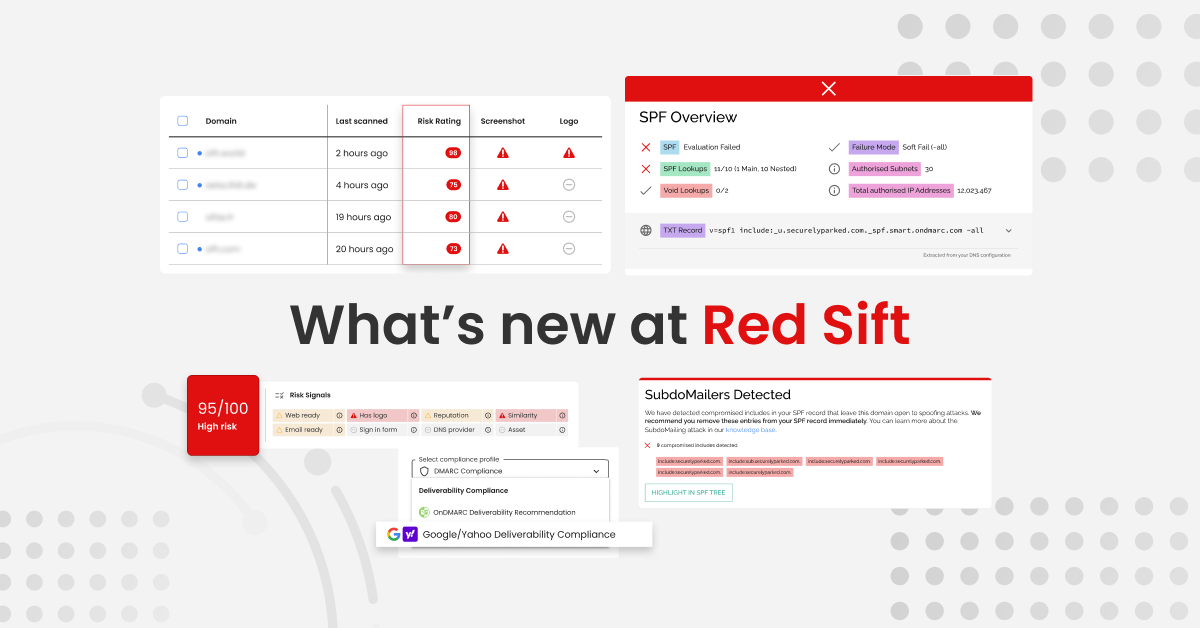
As phishing attacks become more complex and sophisticated, it becomes harder for users to identify one when it lands in their inbox. Financial institutions, as well as businesses from all other industries, should be ensuring their brand, clients, supply chain, and internal users are protected against BEC attacks by reinforcing their email security posture.
At Red Sift, we help our clients protect assets outside of their network by supporting them to implement the DMARC protocol. By closing the gap between what is provided by traditional email gateways and user awareness training, we empower users to quickly identify malicious emails and help to protect a company’s email domain.
Click below to check your current email security hygiene.