Emails are an inevitable part of today’s corporate and personal life. But do you know what mechanisms a standard mail exchange process follows? Well, multiple elements are included, like email protocols, email service providers, mail user agents (MUAs), message submission agents (MSAs), mail delivery agents (MDAs), etc.
This blog focuses on understanding the difference between SMTP, IMAP, and POP3 email protocols.
What is an Email Protocol, and how does it work?
An email protocol is a standard set of interoperability rules for exchanging information between different email providers as well as email clients. An email protocol ensures the email is universal and functions similarly across users.
Some email protocols receive emails, while others transfer them to receivers. Simple Mail Transfer Protocol (SMTP), Post Office Protocol 3 (POP3), and Internet Message Access Protocol (IMAP) are three email protocols used by various email service providers for the transmission and retrieval of messages across servers.
The following sections of the blog discuss what is SMTP, what is POP3, and what is IMAP in detail.
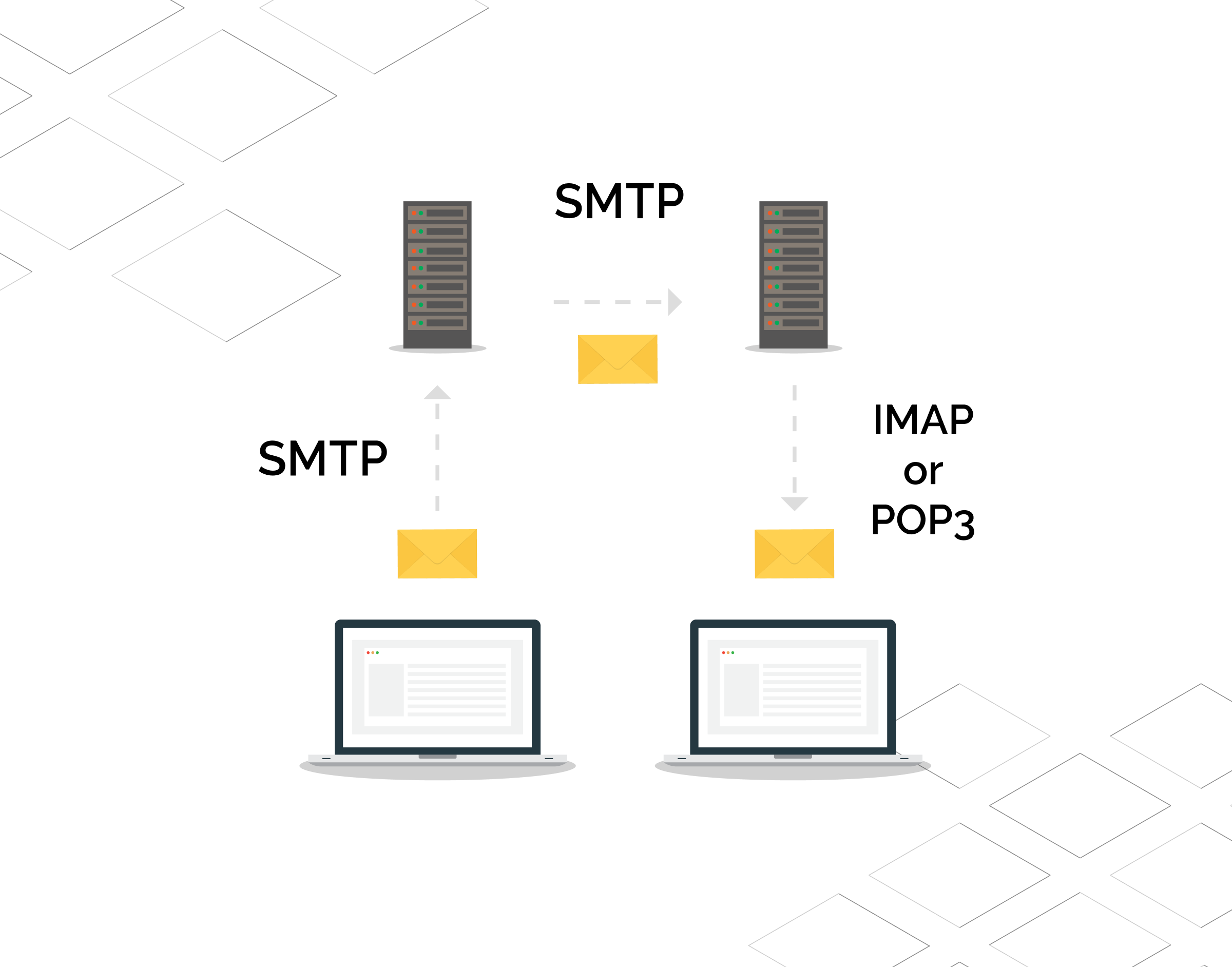
Email protocols work quite similarly to physical mail that we receive in our post box. Consider the following example for comprehending an email message’s transfer flow.
A user with the email address xyz@gmail.com sends an email to abc@yahoo.com, which is sent from the Gmail email client. SMTP will transfer or push the email message to Gmail’s server, which is a distribution center. This is followed by the message being further pushed to the recipient’s email server, which is Yahoo in this example. Once it reaches the recipient’s server, it lands in the desired recipient’s mailbox via a mail delivery agent and then fetched by the recipient by using POP3 or IMAP.
What is the Difference Between an Email Client and an Email Provider?
Before we move ahead, it’s important that you know the primary difference between an email client and an email provider.
Email Client
This is the email application used for accessing messages. It can be the same as your email provider, but not always. It includes specific rules for deleting, archiving, drafting, or grouping emails. Common email client examples are Apple Mail, Outlook, Thunderbird and Yahoo Mail.
Email Provider
An email provider is a service that supports and performs technical steps in transmitting and retrieving your emails. Its common examples are Gmail, Hotmail, and Outlook.
What is SMTP?
SMTP (Simple Mail Transport Protocol) is the industry standard protocol for sending emails. It is defined in RFC 5321 and it helps relay emails from an email client to the desired recipient’s server. An email client and SMTP server exchange instructions through an established connection, generally over ports 465, 587 or 25.
However, if the recipient server does not support STARTTLS, a command to encrypt the transmission, SMTP isn’t secured as it lacks encryption; leaving emails prone to MITM and eavesdropping attacks. You can add a preventive layer by deploying MTA-STS to force encryption and prevent the suppression of the STARTTLS upgrade on servers that support it. Learn more about how to increase SMTP security and stop man-in-the-middle attacks with MTA-STS.
How does SMTP work?
First, the email client connects to the SMTP server and authenticates the connection. Once the connection is established and authenticated, the message is transferred from the client to the server and the server will then initialize delivery of the email message to the destination server via its MX record. In case the email is not delivered, it’s returned to the sender with an explanation.
What is IMAP?
IMAP retrieves emails from the mail server. Unlike POP3, which is a one-way sync from the server to the client, IMAP allows the sync of messages and message state between the clients and server so that you can access them from any device. All the changes are dynamically updated; you will see the update when you access emails from other devices.
How does IMAP work?
IMAP (Internet Message Access Protocol) is defined in RFC 3501 and allows the mail user agent to fetch the messages from a mail server. It requires a TCP/IP transport layer to complete the process. Since IMAP stores emails locally, you can access them anytime and anywhere without having to download them on multiple devices.
General steps of an IMAP operation:
- The email client gets in touch with the server using IMAP when you sign into it.
- A secured connection is established on a specific port.
- The email client shows the headers of all emails.
- IMAP downloads the email content when the recipient clicks on it. However, the attachments aren’t auto-downloaded.
- Email copies stay on the server unless you choose to delete them.
What is POP3?
POP3 is also a retrieval protocol that works over a TCP/IP connection and is used by recipients’ servers to download emails. Its downside is that it’s a one-way protocol, meaning emails don’t automatically synchronize across devices and locations, and it also does not sync any other folders besides the Inbox.
How does POP3 work?
POP3 (Post Office Protocol, version 3) is a protocol defined in RFC 1939. Unlike the IMAP protocol, POP3 only downloads what’s in the inbox, not other folders like sent, spam, deleted items, etc. It also can keep an unread copy on the server, or it can purge the messages from the server upon fetching them.
General steps of a POP3 procedure:
- Authorization stage: The email client connects to the server.
- Transaction stage: The email client retrieves the email message.
- Update Stage: The message copy is deleted from the server (if selected).
- Disconnection: The email client and the server disconnect from each other.
What is the difference between SMTP, IMAP, and POP3?
SMTP transmits emails between servers, while POP3 and IMAP retrieve them from the mailbox on the server.
IMAP vs. POP3
While POP3 doesn’t give you the advantage of syncing emails between any device, IMAP allows simultaneous access by multiple clients and supports syncing of folders and message state. POP3 downloads your emails to your device, optionally deleting them from the server. With POP3, you can’t organize emails in the mailbox of the mail server into folders, something IMAP allows.
POP3 is a considered a legacy protocol and most providers no longer recommend it, however, they keep it for legacy purposes. Nearly all email providers support and recommend IMAP due to its flexibility and syncronization options which allow you to manage, and organize your mailbox on the go.
For more information about security protocols and email configuration, feel free to get in touch!