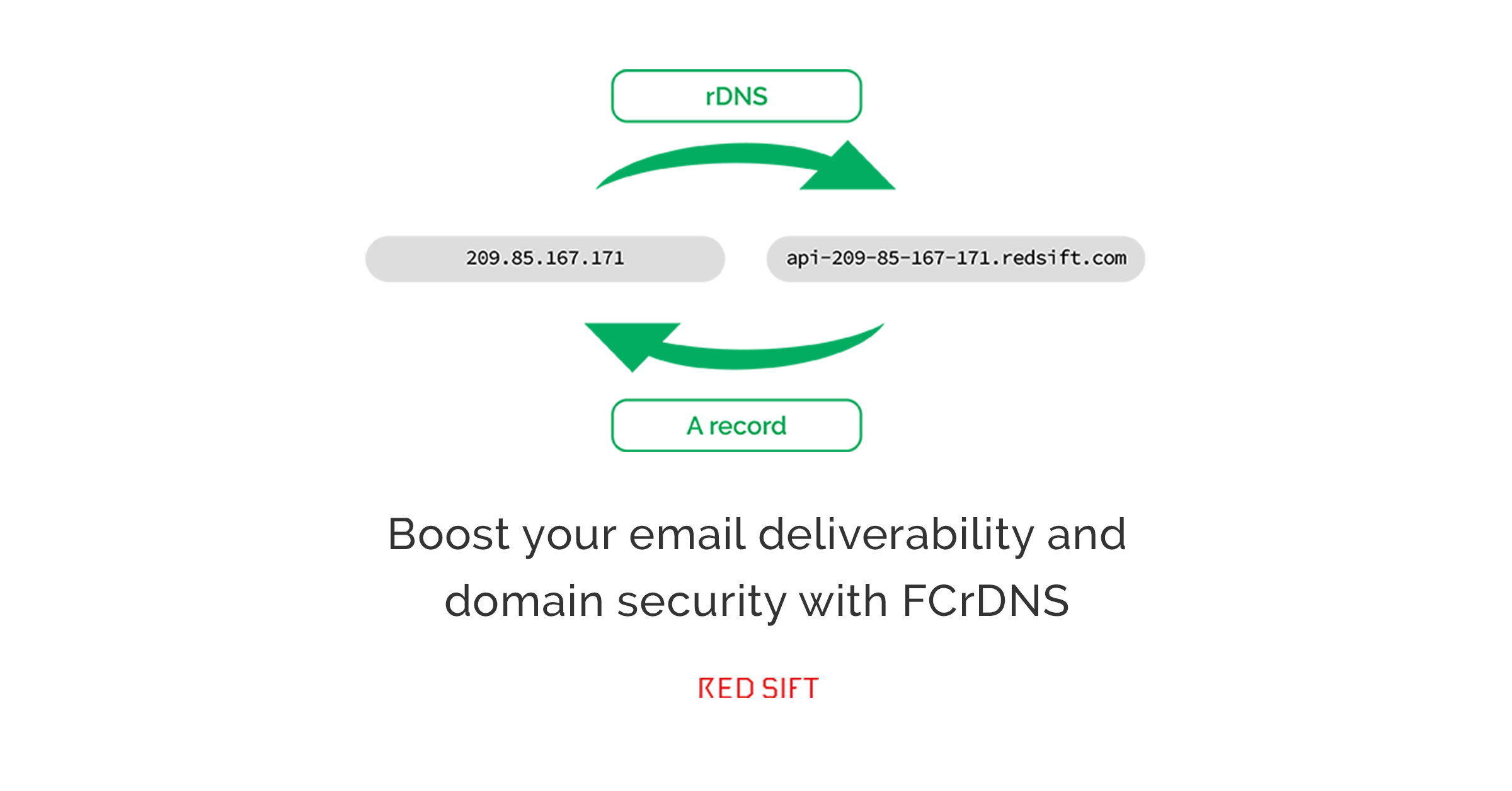
Forward Confirmed Reverse DNS (FCrDNS) is a technical DNS configuration that shows the relationship between an IP address and a hostname.
FCrDNS allows you to prove that your IP address is using a sending domain that you own; this allows a form of authentication that some mailbox providers use in their spam filter methodology and if set up correctly will help the deliverability and security of your email.
Improving security
The objective of FCrDNS is to reduce the amount of incoming spam that is processed by a mail server. This check happens as soon as a connection is made to your SMTP server before any other header information is received. As a result, the SMTP server can reject mail early on and not waste processing time or resources.
Misconceptions regarding where should FCrDNS be setup
When setting up FCrDNS on an IP address that is sending out mail, it is best practice to set up the hostname with an A record in your DNS. When an IP address is set up this way, the IP has a reverse DNS resolution of a single hostname. The hostname reversed points back to the IP address. That IP now uses the same hostname to introduce itself during SMTP transactions.
Not every hostname needs to be set up with A/AAAA records; a single hostname can point to multiple IP addresses. Vice versa, a single IP can also point to a different hostname or to nothing at all.
The above example shows an IP being pointed to multiple PTR records, a setup we do not recommend because anyone verifying such an IP will need to do multiple DNS lookups for verification, requiring more computing power and time. Our recommendation is that only one IP sending mail should have FCrDNS. However, please note that this is not a definitive setup as not all outgoing mail servers have it configured.
Do all Cloud Providers support FCrDNS?
Some cloud email sending services don’t support FCrDNS. For example, Office 365 is a shared environment that provides email services and sends from a variety of different IPs. When emails are sent via Office 365 SMTP, FCrDNS can’t be implemented. However, if you have a static IP that you own to send email, FCrDNS can be configured.
FCrDNS, SPF and DKIM and DMARC
It is important to strengthen your email authentication infrastructure by implementing SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance). These three protocols work together and have been identified as best practice to secure your email domain.
But, what does each one of these protocols do and how do they enhance FCrDNS?
- SPF allows you to publish a list of IP addresses that are authorized to send email on your behalf
- DKIM is a digital signature that travels with your emails, which is then validated by the receiving server as your legitimate signature
- DMARC uses the results of SPF and DKIM to tell the receiving server if they should either put the email in the end user’s inbox, put it in the spam folder or reject the email
DMARC, DKIM and SPF combine to give you extra security and deliverability by:
- Allowing the receiving server to verify ownership, letting them reverse look up your sending IP to your domain
- Allowing the receiving server to validate that the sending IP is authorized
- Providing extra authentication via DKIM and ensuring your email keeps their authentication information even if that email is forwarded by an intermediate service like a distribution list
- Telling the receiving server if they should accept or reject an email based on your DMARC pass/fail results and your DMARC policy
Demystify your DMARC, DKIM, SPF, FCrDNS and TLS setup by using our free Investigate tool today!