Lack of protection from exact impersonation is a hole in the way the global email infrastructure works, exposing every business to cybercriminals. DMARC is the security protocol that secures your email, protects your clients, and improves the deliverability of every email you send.
When we started Red Sift, we wanted to unlock the data hidden in every business, and help decision-makers make better choices as they grow and adapt to ever-changing conditions. We began with deep email integration – simply because it’s a data store that every single person in every business has. We’ve all got thousands of emails with to-do lists, client contacts, meetings, and attachments we’re meant to look at. This is a tremendous consolidated view of our digital lives.
As we built a platform to transform this data into insight, we knew that security was going to be a prime concern. No business wants to give a third-party program, however respectable, a view of their email. We built and contributed code to the various email security libraries out there but quickly ran into a big problem.
Before DMARC, existing email security was completely ineffective against impersonation
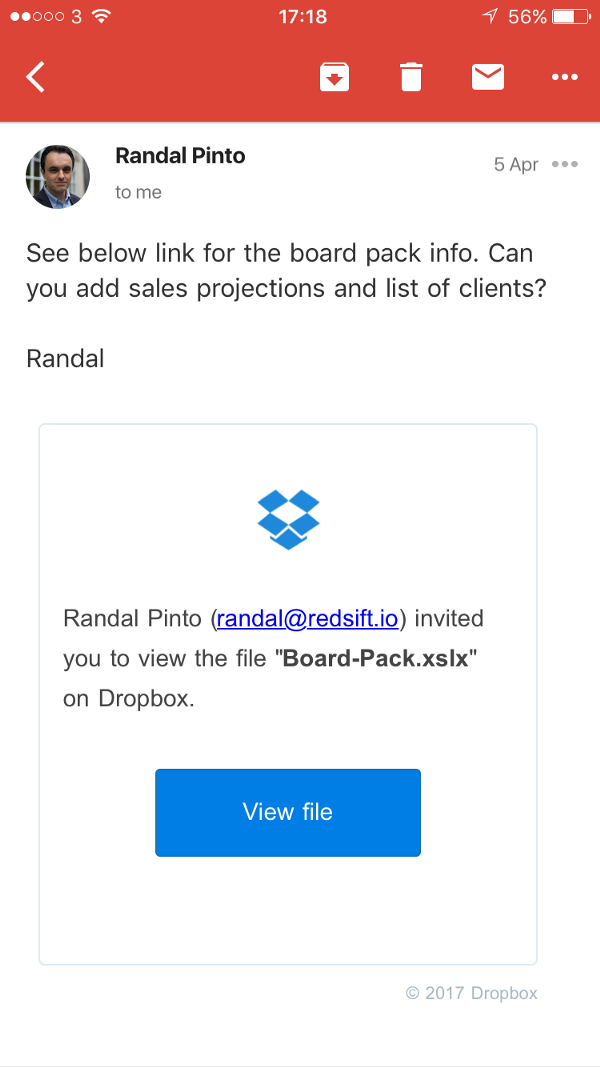
It’s entirely straightforward and very easy to effectively impersonate someone online. I don’t mean on a chatroom, or through the dark web. With just a few lines of code, it’s possible to ‘spoof’ an email address and send a malicious phishing email that looks genuine. Just take a look below.

Banco Popular did not send this email. I did, using a tool you probably have installed on your computer. On the left, I used telnet (a simple program that has been around since 1969 and comes pre-installed on every Mac, Linux, and most Windows machines), and emulated the email protocol, effectively impersonating someone else – in this case, one of Spain’s biggest financial institutions.
Unlike standard phishing attacks – those emails that look legitimate but with a clearly suspicious reply address (you know ‘theocb@sgsfg.id’, or the like) – the email address in this attack looks completely legitimate ( ‘customer-support@bancopopular.es’).
With just a single email to go on, your email server will think it’s ok and let it through your spam filter. And if you have a Banco Popular account, you’ll probably think it’s legitimate too!
Exact domain impersonation is perfect for Business Email Compromise (BEC)
This tactic works with almost all email addresses, and many cybercriminals use it to carry out BEC attacks. This is where they impersonate someone important within a business, and phish employees to gain access to money, credentials, and more.
What if you got an email like the above from the Chairman, Co-Founder, or your MD at your business asking you to review a document they’re working on? Would you be able to tell if it’s fake if it came from a legitimate email address?
Probably not, and you’d probably click on it. Why wouldn’t you? It even has your chairman’s name and picture – the Gmail iOS App even does you the courtesy of filling in the Google+ profile picture encouraging you to act.
Your email is the back door to your business, without DMARC it’s wide open
Crucially, and terrifyingly, no accounts need to be hacked or passwords stolen to impersonate a business. I didn’t have to go to the dark web and find exotic exploits or buy lists of compromised mail servers. To carry out the above example, all I needed was telnet and a little social engineering – looking up the business’ chairman or directors on LinkedIn to get their names and job titles is enough.
We all trust our email providers (Google, Microsoft, etc) to effectively handle the security of our email identities online. But this impersonation technique is part of a deeply rooted problem, emerging from the unfortunate way mail relay has worked since the dawn of the internet.
You may have invested in cyber security measures, have a modern strong password policy, file scanners and spam detectors, and enabled 2FA. But these don’t doesn’t make a difference when it comes to impersonation. All of this can be sidestepped by exploiting the pervasive weakness in email leading to further compromises across the rest of your security infrastructure. It’s like securing your house with the latest alarm systems and then leaving the front door wide open.
There is a solution for exact domain impersonation: DMARC
Just because it’s part of the way the internet works, it doesn’t mean exact impersonation is unsolvable. If you tried to spoof a Red Sift email address today, the Gmail server would actively reject your telnet session and log you off. Essentially, the front door would be slammed in your face and your attempt to impersonate the domain would be thwarted. This is because we’ve adopted DMARC and we have enabled it to reject unauthorized traffic. And more and more businesses are doing this too.

What is DMARC?
DMARC is an email security protocol that prevents anyone from impersonating your domain to send malicious phishing emails to your customers, employees, clients, and supply chain. When you have DMARC fully implemented at a policy of p=reject, it’s impossible for anyone to impersonate your email domain, and they can’t pretend to be anyone else in your business. So there’s no worry that hackers might use your email domain to send fake emails to your employees or clients.
The National Cyber Security Centre talks about it continuously, and a wide range of governments recommend you use it too. Yet many organizations globally still haven’t adopted a DMARC policy of p=reject. Why? Because enabling DMARC to actively reject unauthorized traffic requires a bit of know-how, and without the right AI-enabled tools, it can be a complicated task.
OnDMARC is a simple DMARC solution for every business
Using the Red Sift platform, we built OnDMARC, the software as a service (SaaS) that acts as a step-by-step guide for anyone wanting to make their email secure by enabling DMARC at p=reject. OnDMARC analyses email traffic on your domain automatically, and then tells you how to set up the protocol to stop hackers while letting legitimate emails through the net.
OnDMARC takes the complexity and guesswork out of implementing DMARC. You don’t want to delve into the black art of email security protocols, you want a simple solution to the problem so you can get back to your business. We built OnDMARC with this vision in mind : it’s straightforward enough that anyone can do it, even if they have no IT experience.
The average time it takes for OnDMARC customers to get to p=reject is 4 – 8 weeks, as opposed to months.
OnDMARC improves email deliverability
Security isn’t the only benefit of OnDMARC. Ever have your emails get sent straight to the spam box of a client? Have a newsletter with really low open rates? That’s because most email domains are badly configured, which means the emails they send out to the world look a bit suspicious to other domains. Legitimate emails can get stuck because they look suspicious — even though it really is you!
OnDMARC goes a long way to solving this problem. It reconfigures your settings, which puts the emails you send above suspicion and straight to the top of your clients’ inboxes too. This is a business enabler that stops you from throwing money down the drain.
DMARC is for every business
DMARC works best when we all have it. The more email domains and companies that have this protection, the harder it will be for hackers to exploit this hole in the internet.
So at Red Sift, we want to make sure there are no barriers to adoption. We price our product to scale with your email volume and we offer a free trial too. OnDMARC basic is free for all charities, with 50% off for larger packages. OnDMARC can also be integrated with your SSO or existing operational dashboards via our API, so we have you covered.
OnDMARC secures your email from exploitation, protects your customers, shuts the front door on hackers, and improves the deliverability of every email you send. It’s hard to get better than that. Why not try it out with a 14-day free trial, and begin securing your business email today?






