Nobody wants a Christmas general election to interfere with the general merriment and festivities of the one winter event that we enjoy and some of us well, endure. And what’s more, the run up to this year’s has been particularly hostile and mired with controversy and, let’s face it, a little deceit.
With the Tory press office Twitter profile being rebranded ‘@factcheckuk’, the public can hardly be blamed for being suspicious about the party’s motives. For many unwitting Twitter users, this profile was a genuine, verified account, discharging a steady stream of objective political facts.
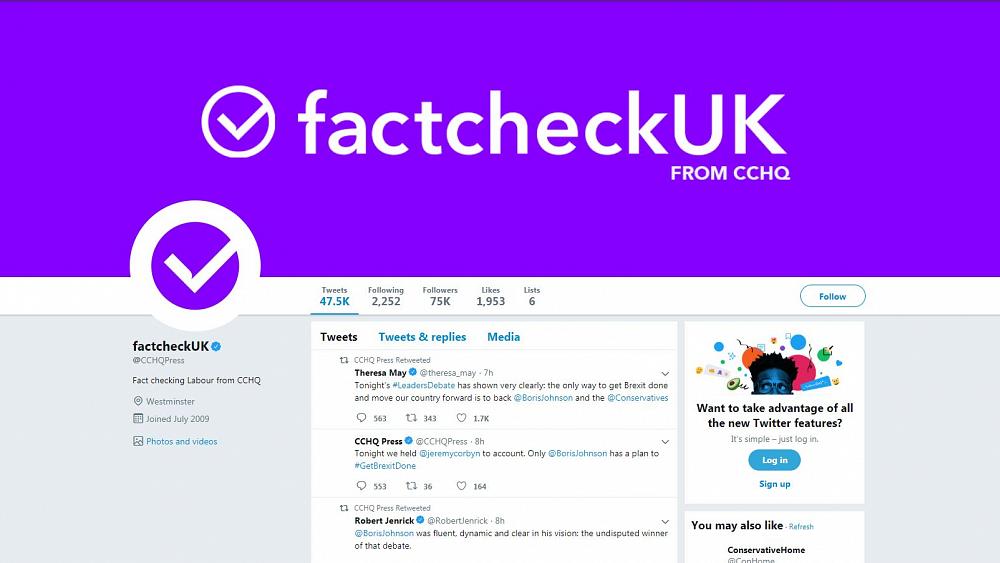
Misleading. Impersonation. Duping. We often use those words when we talk about phishing emails. Scammers impersonating a trusted organisation to mislead you into handing over personal details or money… The similarities are somewhat worrying!
So in that vein, we thought we’d take a look at how well the 13 political parties from GB and NI were protecting their constituents from the potential of phishing attacks by analysing their primary email domains.
Annnnd you’ve guessed it, none of the parties had their DMARC policies configured to quarantine, let alone reject. Only three of the parties – Liberal Democrats, Labour and SNP had a valid DMARC policy, but would still need to tighten configurations to direct impersonated emails using the @libdems.org.uk email domain for example, into the spam/junk folder.
So, with under a week to go, we implore you to take anything you read from a political email with a pinch of salt – seek out the official websites, try and find an impartial news site, and mostly, get out there and vote! Should you need any help with setting up your DMARC policy and ensuring the emails you both send and receive are legitimate, contact a member of the team!
Research methodology: Red Sift conducted the study in November 2019, using the domains of the main political parties in the UK with candidates from GB & NI running for the general election on 12 December 2019.






