DMARC is a vital component in the fight to secure your business’ email security posture. So it’s not surprising that a lot of people are talking about it. But there’s a lot of information out there, and it’s easy to become overwhelmed. We’ve written this article to help you unpack and understand this email authentication protocol reinforcing email security for good.
What is DMARC, and where did it come from?
In October 2008, the Network Working Group officially labeled Simple Mail Transfer Protocol (the internet standard for transmission of electronic messaging) as ‘inherently insecure’. They said that anyone could impersonate a domain and use it to send fraudulent emails pretending to be the domain owner. This highlighted real security issues.
So to solve this, some of the biggest names in email came together and, in January 2015, DMARC was born (well, ratified for standardized use).
DMARC stands for Domain-based Message Authentication, Reporting, and Conformance. It’s an outbound email security protocol that protects domains against exact impersonation i.e. when a bad actor pretends to be you to send phishing emails to your employees, customers, and supply chain.
How does DMARC work?
DMARC works using the existing security protocols SPF and DKIM. Your SPF record (Sender Policy Framework) is essentially a whitelist of IP addresses you’ve authorized to send emails using your domain. DKIM (DomainKeys Identified Mail) acts like a digital signature, letting the recipient know you are who you say you are. When you first configure DMARC, you’ll spend some time classifying which senders you’ve authorized to send emails using your domain, and which you haven’t.
Both SPF and DKIM are essential to your email security setup, but neither prevents exact impersonation (spoofing). Because while they tell the recipient who the email is from, the recipient has no instruction to act on this knowledge, i.e. it doesn’t know what to do with your email.
So, DMARC works by combining the results of SPF and DKIM to determine if your email is authentic and authorized. Then, the DMARC policy you have in place tells recipient servers what to do with it.
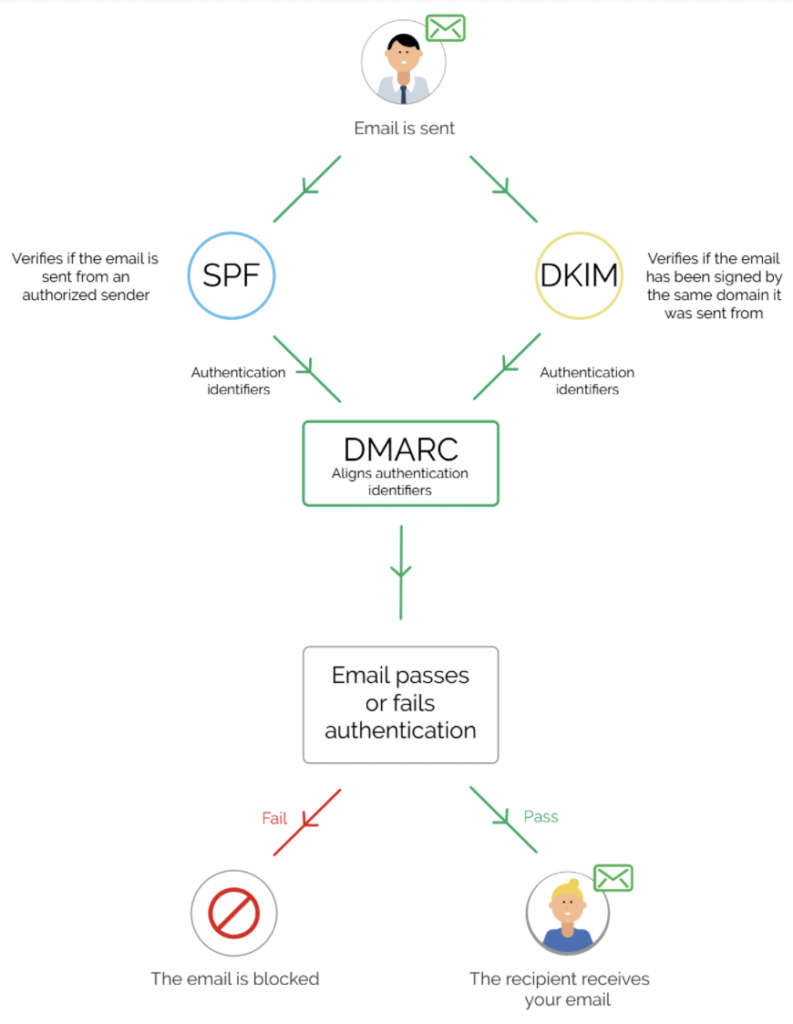
What is a DMARC policy?
Your DMARC policy is basically the instruction you give to receiving servers, telling them what to do with emails that come from your domain. There are three DMARC policies to choose from, but only one (p=reject) fully protects your domain from exact impersonation.
p=none: this policy tells the recipient server to accept all emails from your domain, regardless of whether they pass authentication or not.
p=quarantine: this policy tells the recipient server to send any emails from your domain that fail authentication to spam.
p=reject: this policy tells the recipient server to reject any emails coming from your domain that fail authentication.

When your policy is at p=reject (otherwise known as a ‘strong’ DMARC policy), any emails sent by unauthorized senders using your domain will be blocked from reaching the recipient. This is how the DMARC protocol stops spoofing when fully enforced, because it actively tells receiving servers not to accept emails from your domain if they’re coming from an unauthorized sender.
What is a DMARC record?
A DMARC record is a text record that explains the DMARC policy you have in place. If you’re using OnDMARC, then your DMARC record is automatically generated in your account, you just need to add it to your DNS.
To get into the more nitty-gritty detail of what DMARC records and tags look like, and how you add a DMARC record to your DNS, check out our in-depth blog from our customer success team.
What is a DMARC report?
DMARC provides two types of reports: aggregate and forensic. When you first start using DMARC (and when your policy is p=none) you’ll receive aggregate reports telling you:
- Which emails sent from your domain are currently passing or failing DMARC
- Who the senders and receivers of emails from your domain are
- Where in the world emails are being sent from using your domain
How easy these reports are to understand will depend on the DMARC tool you choose to use.
Forensic DMARC reports provide more detailed insight into the emails sent using your domain, including:
- From address
- Subject line
- IP address
- Return path
- Date
- Country
Reporting is an important first step, but there’s a common misconception that if you’re receiving DMARC reports then your domain is protected, and that’s incorrect. Your domain is only fully protected when you have enforced a DMARC policy of p=reject.
What type of threats does DMARC protect against?
DMARC is an outbound security protocol, meaning it simultaneously protects recipients and your brand reputation from being exploited. It’s important to remember that bad actors who use your domain to trick people into opening emails aren’t doing so by chance, they’re piggybacking off the weight of your brand reputation and relying on it to encourage email opens.
DMARC stops this exact domain impersonation, by telling recipient servers not to accept any emails which aren’t authenticated to have come from you. So, bad actors cannot use your domain to send phishing emails and carry out Business Email Compromise (BEC), resulting in fewer attacks like:
- Vendor Fraud
- Ransomware
- CEO Fraud
- Whaling
- Invoice Fraud
- Spoofing Emails
- Supply Chain Attacks

Why is DMARC important, and what are the benefits?
The more companies and institutions enforce a DMARC policy of p=reject for their outbound email, the safer the email ecosystem becomes overall. This is because attackers and bad actors will have fewer domains to ride on the back of to carry out attacks. So as a result, more sensitive information is protected, more money is saved and fewer attacks are successful.
But aside from this, DMARC can offer some real business benefits too, including:
- Brand and domain reputation protection
- Improved deliverability rates and inbox placement
- Eligibility for BIMI (the new standard which attaches registered logos to DMARC authenticated emails)
Does DMARC offer inbound email protection too?
Yes, to an extent. It does stop bad actors from using your domain to carry out phishing attacks on your own employees, so you’re protected from Business Email Compromise. However, it doesn’t actively stop all threats which are coming into your inbox, for example, phishing emails using other domains which don’t have a strong DMARC policy. For this, you should use spam detection and file scanning technology, as well as SEGs and advanced threat protection such as OnINBOX.
Is there a free DMARC tool where I can do a DMARC check?
Yes! You can quickly and easily check your current DMARC setup using our free Investigate tool.
What’s the fastest and easiest way to become DMARC compliant?
If you choose to do DMARC alone, the process can be tricky, and if done incorrectly it can lead to more problems than you already had. Our mission is to make the technology essential for cybersecurity accessible, and it’s why we created OnDMARC, the tool which gets you to p=reject in just 5-8 weeks, instead of months.
It’s easy to use, with clear reporting dashboards and step-by-step instructions for everything from adding your DMARC record to your DNS to configuring your trusted sending sources. We even offer end-to-end BIMI set up too, so you can get your logo in the inbox and start increasing email opens and engagement.
Why not give it a try with a free 14-day trial below?