Has a senior executive at your company ever been spoofed? Or even worse, has anyone in your company fallen for a spoof email resulting in a loss of money or data? BEC (Business Email Compromise) is the act of compromising a business email user in some way by convincing them to do something they shouldn’t.
Spoofing and phishing are very common forms of BEC that every business in 2022 has to contend with. Since 90% of cyberattacks start with a phishing email it’s not simply a matter of if, but when.
What’s the solution?
A layered email security strategy that protects against advanced threats is crucial. The DMARC protocol is part of this.
But “what is DMARC?” you might ask.
DMARC (Domain-based Message Authentication, Reporting and Conformance) is an open standard email security protocol. Once fully implemented, it will protect your domain against impersonation of the “From” Domain. This means people (fraudsters) won’t be able to send emails that look exactly like they come from you.
DMARC was developed in 2012 by Google, Comcast, AOL, Microsoft and Yahoo as a way to fully block and prevent impersonation attacks on domains. By coming together, they created an open standard solution to the rapidly growing phishing problem and DMARC was born.
So how does it work?
The DMARC protocol is based on two pre-existing protocols:

SPF (Sender Policy Framework) – This is an authorization protocol, developed to help fight sender address forgery by comparing the sending server’s IP address to a list of authorized senders. Think of SPF like a guest list at an email “party” – the IP address of the email sender has to be on the guestlist issued by the domain owner to pass.
Here’s what happens…
SPF uses the Return-Path header of the email, extracts the domain and originating IP address, and checks if that domain has authorized the IP to send emails. DMARC also checks if the extracted domain is an exact match to the From domain or subdomain. If they are both the same or subdomains of each other, alignment passes and DMARC passes from an SPF perspective. Without alignment, DMARC fails.

DKIM (Domain Keys Identified Mail) – This authentication protocol is essentially a signature that is applied to each email to verify where the email has come from and that the contents of the email have not been changed along the way.
Here’s what happens…
DMARC checks if the DKIM signing domain matches the From domain of the email or its subdomain. If they’re both the same or subdomains of each other, alignment passes and DMARC passes from a DKIM perspective. Without alignment, DMARC fails.
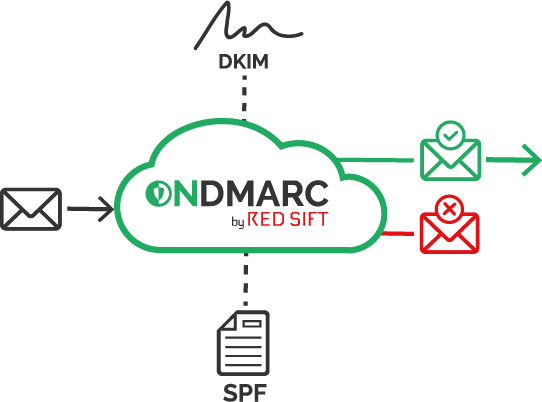
By checking SPF and DKIM results, the receiving server will determine whether or not DMARC has passed. If the email passes SPF and/or DKIM, then DMARC passes. If it fails both SPF and DKIM, then the email fails DMARC validation. You must set up SPF and DKIM correctly for all your sending services that are legitimately sending emails on your domain’s behalf.
What happens to an email that fails DMARC depends on what policy you have set in the DMARC record for your domain.
What are the DMARC policies and what do they mean?
There are 3 DMARC policies:

This is reporting only mode where you gather information about the email traffic on your domain. During this phase you will be configuring SPF and DKIM for all your valid email sending sources. Email flow will not be affected at this stage.

In this policy you should have properly configured SPF/DKIM for all your legitimate sending sources. During p=quarantine, emails that fail DMARC validation (ie are likely fraudulent) will go to the recipient’s spam folder. Legitimate emails that pass DMARC will arrive in the inbox. This can be seen as a testing phase to ensure proper configuration before going to reject mode.

This policy is the end goal. Once at p=reject, your domain is protected against impersonation. This means that any email that fails DMARC validation (ie fraudulent email) will be blocked from reaching the recipient’s inbox. All legitimate emails will pass DMARC and be delivered to the intended inbox. Email deliverability will also be significantly boosted as a direct result of your DMARC journey.
So what’s next?
We have seen in this blog that having DMARC in place is a crucial part of the layered security solution that organisations must implement in order to be protected against BEC attacks. As a technical protocol it significantly reduces the risk of email impersonation and phishing for your colleagues, end recipients, and supply chain by using SPF and DKIM results to ensure valid emails are delivered and fraudulent emails are blocked. It is the only way businesses can take back control over what’s happening outside their network and service perimeter.
So far this all seems straightforward, however real world email infrastructure is fundamentally complex and organisations are usually reluctant to configure DMARC. Often, this is due to a number of reasons such as fear that they might block their emails in the process, not have the skills or knowledge to interpret complex XML reports, or they have the all too common misconception that they’re already protected by their email gateway. As a result of this, $1.77 Billion was lost to Business Email Compromise attacks in 2019.
Organizations must concern themselves with the growing global issue of BEC, as it remains to be a common threat vector that exists as the “easy way in” to their business. Take the necessary steps to secure your domain and protect your brand against BEC by quickly and easily configuring DMARC for your email sources with a self-serve tool like OnDMARC which provides full visibility and guidance within 24 hours of your free 14-day trial.
With the trend toward using cloud services on multi-tenant infrastructure, email security and DMARC in particular become much more nuanced.






