The year started like 2020 did not end. Living in lockdown has proven to be fairly difficult for all of us and the cybercriminals are out there making it even worse. They are busy taking advantage of organizations trying to configure their journey to digital transformation, cloud adoption and remote working.
By combining the fast adoption of SaaS applications and the potential misconfiguration errors that inevitably arise, together with unknown vulnerabilities from third-party suppliers, we have a recipe for disaster for the good guys.
Recent cyberattacks
Let’s start by taking a look at the recently reported spoof attack against microsoft.com that reached over 200 million users. The Business Email Compromise (BEC) phish lured users to check for quarantined emails from a link within the email. Since the email came from a legitimate Microsoft domain, users assumed it was a legitimate message. The cybercriminals were then able to steal their O365 credentials when they accessed and inserted their credentials in a mirror page of the application.
Attacks like this are not unique. If we look back 12 months earlier, Check Point Software reported that the Florentine Banker Attack started from an impersonation, this time from a look-alike domain to Microsoft. The adversaries were able to compromise O365 credentials and launch a man in the middle attack against two Financial Services organizations in the United Kingdom, eventually financially defrauding them of £1 million.
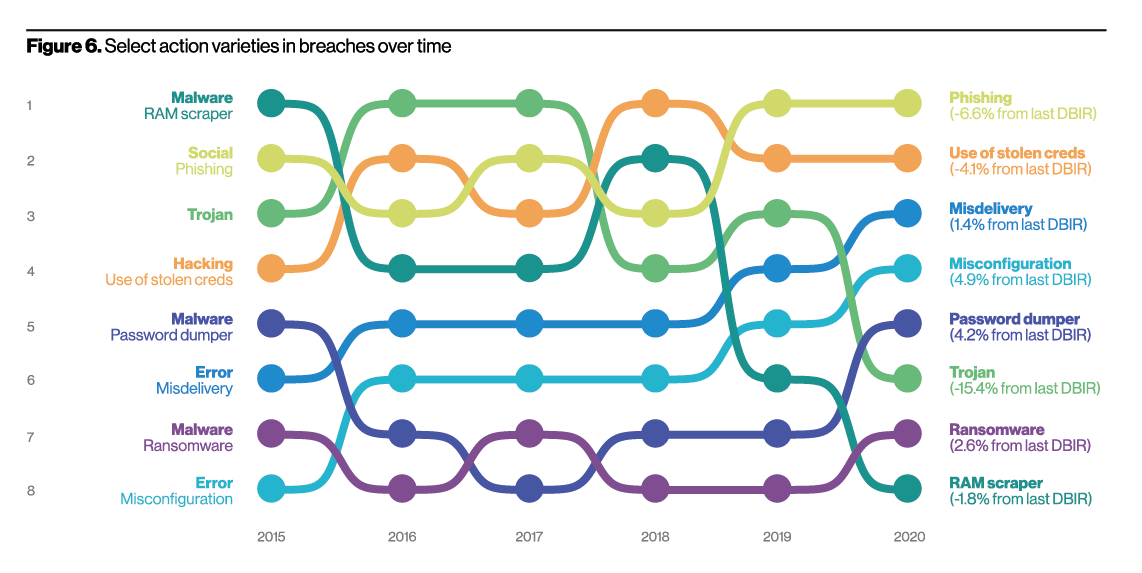
Those attacks are becoming more prevalent, and I believe we will be seeing a lot more coming along. Verizon disclosed in its 2020 Data Breach Investigations Report that the top 3 sources of breaches were Phishing, Use of Stolen Credentials, and Misconfiguration. This is showing us a pattern of leveraging social engineering through advanced Business Email Compromise to steal credentials to cloud applications where businesses store or exchange sensitive information and data.

In 2021, organizations must prioritize the protection of their domains against direct impersonation attacks and identifying then removing look-alike domains.
DMARC can combat spoofing
DMARC (Domain-based Message Authentication, Reporting & Conformance) uses two previously defined protocols, SPF and DKIM, to allow domain owners to explicitly tell the receiving email server what to do with an email that fails authentication. The enforcement of DMARC should be done both in the DNS and email gateway. When configuring a gateway with DMARC, you will be instructing your gateway to honour the policy of the sender’s domain, meaning it will ensure you are protecting your users against inbound impersonations of other domains. However, by enforcing DMARC on your DNS you will also be protecting your domains against direct spoofing attacks, thereby protecting your clients, business partners, internal users and wider supply chain.
Gartner recently identified DMARC as a “Top 10 Security Projects for 2020-2021”. They determined that “organizations use email as the single source of verification, and users struggle to determine real messages from fakes.” The advice on the report is that organizations should look to implement and enforce use of the DMARC protocol to add an additional layer of trust and verification with the sender’s domain.
The implementation and enforcement of the protocol are crucial to closing the gap currently exploited by cybercriminals, however, it is only as part of a layered solution. With better targeted, well planned attacks and emails looking more similar to legitimate ones than ever before, it is highly important to empower internal users to identify malicious emails. Leveraging machine learning and behavioural analytics to highlight the potential threats within an user’s inbox is clearly the direction the industry is heading in to offer better protection against these types of threats.
It is also important to ensure that organizations use tools that complement one another and allow for a holistic view of its email attack surface. By gaining 360° visibility, the security operations team can have a more dynamic operating model that allows for faster detection and response, and ultimately, faster recovery from security incidents.
Attacks through supply chains, like SolarWinds are not far from what can happen through the impersonation of legitimate domains, and advanced Business Email Compromise. If you wish to discuss how Red Sift can help your organization protect its brand and domains against impersonation as well as its internal users against advanced Business Email Compromise, get in touch below.