The Digital Operational Resilience Act (DORA) is set to transform how the finance sector in the EU – and any business that wants access to it – protects against cyber threats such as cyberattacks, ransomware infections, data breaches, and more. The legislation, introduced by the European Commission, expects firms to mitigate any reasonably identifiable circumstances that could lead to an event that could compromise the digital operational security of the firm. Here are 7 things you need to know about the Digital Operational Resilience Act.
1. DORA will impact financial firms and other businesses all over the world
DORA’s impact won’t just be contained to financial institutions in the EU. The comprehensive legislation will have wide-reaching global significance primarily for two reasons. First is that it impacts any financial institution or third-party software organization that needs to access the EU market, in this case making it applicable to the USA, UK, Australia, and more.
The second is that it sets a benchmark for organizations of all sizes in all sectors globally to look to improve their digital operational resilience and business continuity planning. Ultimately, any organization concerned by cyber threats should use DORA as a guidebook to improve its digital resilience.
2. DORA could be enforced sooner than you think
DORA is expected to be fully enforced by 2024, but this doesn’t mean affected firms shouldn’t start getting ready. DORA legislation is due to be formally announced as early as Autumn this year (2022). So, it’s vital for all impacted businesses to start preparing now.
3. DORA will reduce business disruption and protect business continuity
The Digital Operational Resilience Act will reduce business disruption in a number of ways. It will mean businesses are properly equipped to mitigate any reasonably identifiable circumstances that could lead to an event that could compromise the digital operational security of the firm (for example – a cyberattack). Instances such as ransomware attacks and DDoS attacks are known to significantly disrupt business continuity, and DORA helps protect against these and safeguard sensitive data.
DORA will also reduce business disruption and improve business continuity by creating smoother exit strategies. Now, unscrupulous ICT vendors can no longer leave old ‘not fit for purpose’ kit with financial organizations once their contracts are up, as DORA requires exit strategies to be put in place.
4. Board members that don’t comply with DORA could face jail
DORA puts the ‘final responsibility’ to ensure that measures, policies, tools, and protocols are enacted to mitigate cyber threats on a business’ management body (i.e. its boards and directors). If they fail to do this, they could face reputational damage, shareholder litigation, regulatory fines, and even criminal sanctions.
5. To comply with DORA, businesses need to protect against threats relating to email and domain security
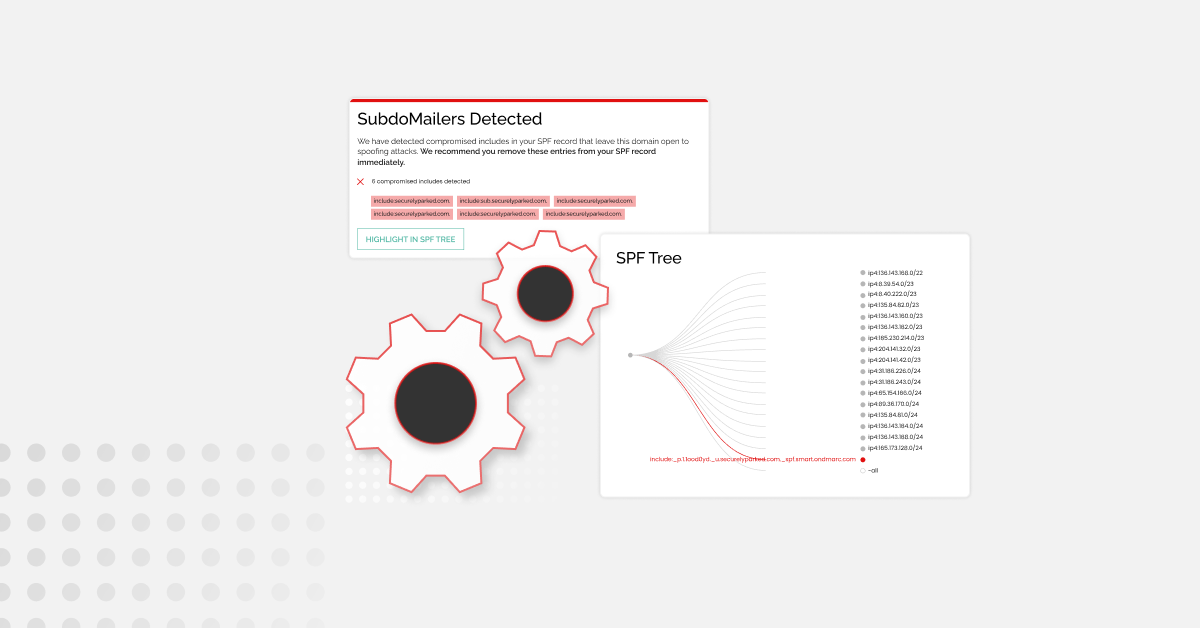
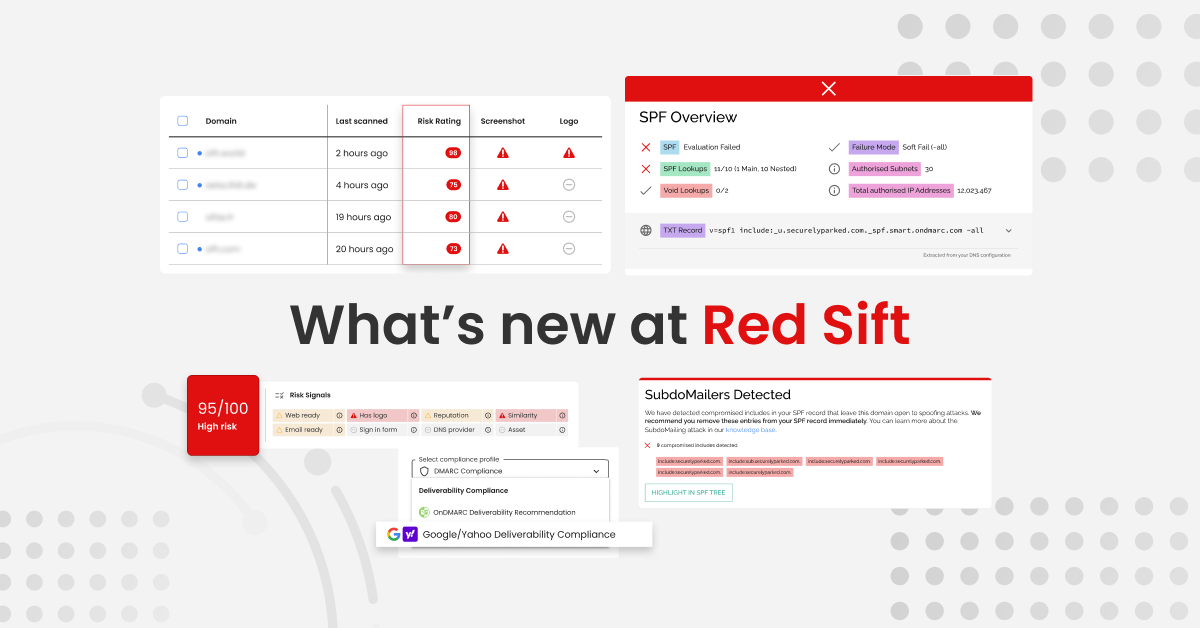
According to CISCO, 90% of cyberattacks happen because of weak email security. So, strengthening email and domain protection will be a key consideration for financial entities preparing for DORA. Targeted phishing attacks such as Business Email Compromised (BEC) are extremely common forms of attack, often made successful by ‘domain spoofing’. The FBI has been warning of Business Email Compromise in its IC3 Internet Crime Report since 2015. So, financial entities can consider BEC a reasonably identifiable circumstance and in turn, should implement DMARC (among other measures), to mitigate it.
DMARC configured at p=reject is a fundamental protection against this. DMARC protects an organization against phishing and BEC by making it impossible for a hacker to impersonate its domain (and brand) to send phishing emails and compromise sensitive data, money, systems, etc. DMARC is recognized by the National Institute of Standards and Technology (NIST), which in turn is recognized by DORA.
6. DORA will mean businesses and supply chains are better protected
DORA means that financial firms will now only be able to interact with third-party vendors that offer ‘high, appropriate, and the latest information security standards.’ This in turn means that supply chains will become more robust because everyone has to put the right measures in place.
7. DORA will help businesses make better decisions, faster
DORA contains everything needed to help financial institutions make better decisions about risk management, data security, risk mitigation, etc. Its comprehensive and straightforward nature also enables faster decision-making.
Download the whitepaper to find out more about DORA
DORA is a lengthy piece of legislation, and without a law degree, it’s hard to dissect. Luckily, we’ve written an all-in-one whitepaper covering everything from what this new legislation means, to who’s impacted, and how organizations can begin to prepare. Download your free copy below, and start getting ready for DORA today!