By now, even people who’ve not heard of computer worms or ransomware have heard about #WannaCry. In this blog, we’ll explore what just happened and how we can use these learnings to help us better prepare our organizations for the next generation of attacks.
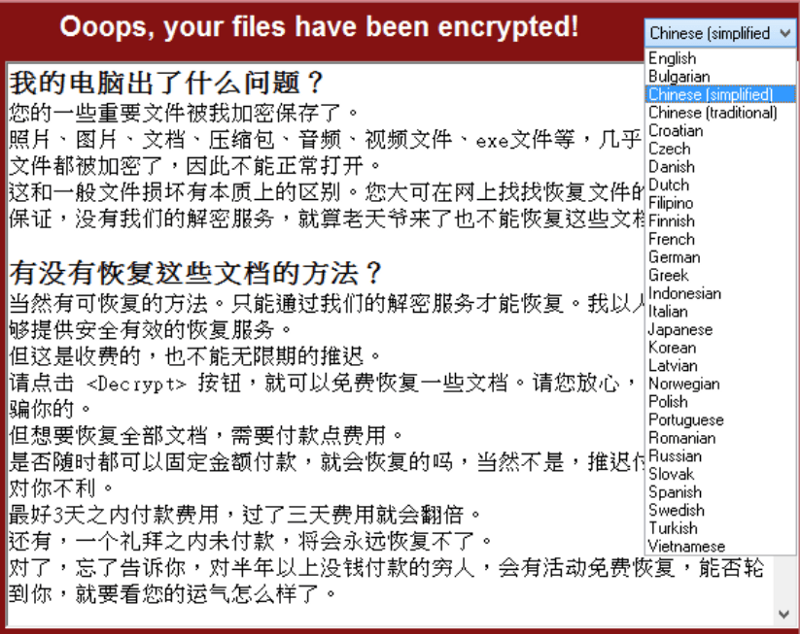
WannaCry is the largest ransomware infection in history with over 70 countries hit with an infection that encrypts the contents of Windows machines and demands bitcoin payment with the promise to unlock the file system and restore access to said files.
How did this happen?
On April 14th, 2017, a group called Shadowbrokers dumped a bunch of internal software tools from the NSA. These are tools nation-states create or purchase to exploit weaknesses in the software you know and use as part of an ongoing digital arms race.
Somehow, Shadowbrokers managed to get hold of some of these bits and released them to the world – think of it as someone making off with weapons-grade plutonium and just giving it away.
The April 2017 dump included 3 groups of exploits. One related to data from the SWIFT payment network, a collection of documents, top-secret PowerPoint presentations, and most interestingly, a care package of exploits for Windows machines. Some of these were exploits that had not been seen before and researchers fully expected to start seeing new attacks built on this, now public, knowledge. Unfortunately, this has now happened.
WannaCry uses an exploit from this trove codenamed ETERNALBLUE & DoublePulsar to rapidly infect Windows machines on a network. Microsoft actually released MS17–010, a security update to fix this, in March. That was a good month before these NSA hacking tools were released to the public. However, at the time these updates were released only for their currently supported operating systems, as per normal commercial practice. We will come back to this.
What’s happening now?
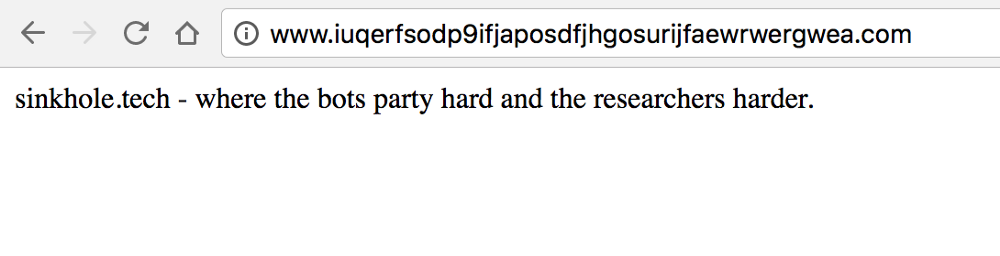
Luckily, as the infection broke, a ‘kill switch’ was discovered. A kill switch is often used to ensure that the creator has some control after the infection is out in the wild. At the very least, they typically want to ensure they can control it while they are actively creating or testing the malware so they don’t demolish their own computers. In this instance, the kill switch was discovered to be a website that the software would check before it started about its business.
Security researchers quickly purchased the domain www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com and it stopped computers that had internet access from further infection.
Microsoft has since released patches for these older operating systems to stem the tide. However, new versions of the worm are out with new kill switches including versions that have NO kill switch. It is clear that this isn’t over yet.
Why did this go so wrong?
To actually get across the organization’s firewall and start spreading, WannaCry needed a backdoor into the system. The innovation for this worm was the use of phishing emails to get it onto the patient zero inside a network. This is the oldest trick in the book and it worked spectacularly well. Most organizations have such a poor posture with regards to their email security that for a hacker, this is an obvious and relatively easy route to achieving their objective.
At the onset of the infection, the NHS in the UK was one of the most significant and public of the organizations affected as real people were put at risk.
We can check the relative health of an organization’s email infrastructure from the outside by measuring the adoption of DMARC, an email cyber security standard. We did a review of domains belonging to around 200 NHS Authorities and Trusts and what we found shocked us.

Our hospitals are not only running unpatched, unsupported installations of the Windows operating system as evidenced by the scale of this infection, but they also have practically no protection to other email-borne threats as they’ve failed to implement DMARC, something the NCSC describes as fundamental for cybersecurity protection. The one organization listed that has DMARC is in the initial ‘reporting’ mode and currently receives no active protection from it.
What next?
WannaCry and its newly forming variants are still spreading and organizations need to clean up. Some variants appear to be dormant but replicating, so it’s safe to say there’s a lot of underreporting of the true extent of the problem. Some of these new variants are not created by the hackers behind the initial WannaCry ransomware so expect to see more takes on this type of attack in the near future. WannaCry isn’t even the only game in town right now, another ransomware dubbed Jaff was being spread at the rate of 5 million emails per hour when WannaCry broke out.
US-CERT, the American Computer Emergency team has been updating an alert on WannaCry and providing a section for Solutions and Recommended Steps for Prevention.
- The first thing they recommend you do is patch your system with the Microsoft patches to stop the spread.
- The second thing they recommended is using technology such as DMARC to prevent email spoofing and start reducing exposure to phishing.
Traditionally, DMARC has been complicated and expensive to deploy but we are working to change that. OnDMARC can test your email infrastructure and help you start your DMARC deployment in minutes.
Of course, the list of actions from US-CERT, including DMARC, isn’t a magic bullet. The reality is that this is one part of a system of tools and processes that need to be in play inside an organization to ensure we don’t fall victim to an increasingly sophisticated and hostile cyber landscape. However, we should all be clear that the time for action is now.
Cybersecurity is now part of the cost of doing business, not just a procedure you invoke when things go wrong. It’s the difference between treatment and vaccination — when possible, prevention is far preferable to cleaning up after the epidemic. This should be a wake-up call for businesses, governments, regulators, and ordinary citizens.
Technology is a companion whose health and safety matter to the way we work, play, and live our lives – we need to treat it as such.
To check your domain health and current security setup, you can use our free Investigate tool and get your results in seconds.