(with apologies to Frank Herbert…)
It may be hard to imagine now, but it wasn’t that long ago that discerning business leaders were able to have thoughtful discussions on the synthesis of technology and business strategy while scarcely ever uttering words about cybersecurity.
How times have changed.
Today, cybersecurity concerns touch most every aspect of business operations as companies and governments have deployed substantial digital assets and vulnerabilities abound. In fact, the threat economy now rivals the GDP of advanced countries. By one estimate alone, the World Economic Forum calculates the cost of cybercrime at $10.5 trillion USD in 2023. And it’s rising.
Business leaders are adapting strategies to meet the changing times. For example, the influential Director’s Handbook on Cyber-Risk Oversight, recently released by the National Association of Corporate Directors (NACD), sets its first principle as “Directors need to understand and approach cybersecurity as a strategic, enterprise risk, not just an IT risk.”
Investments in cyber are also changing: 65% of organizations plan to increase cybersecurity spending in 2023. Gartner projects that spending on information security and risk management products and services will grow 11.3% to reach more than $188.3 billion this year alone.
An Occult View of the Cyber-Enabled Economy
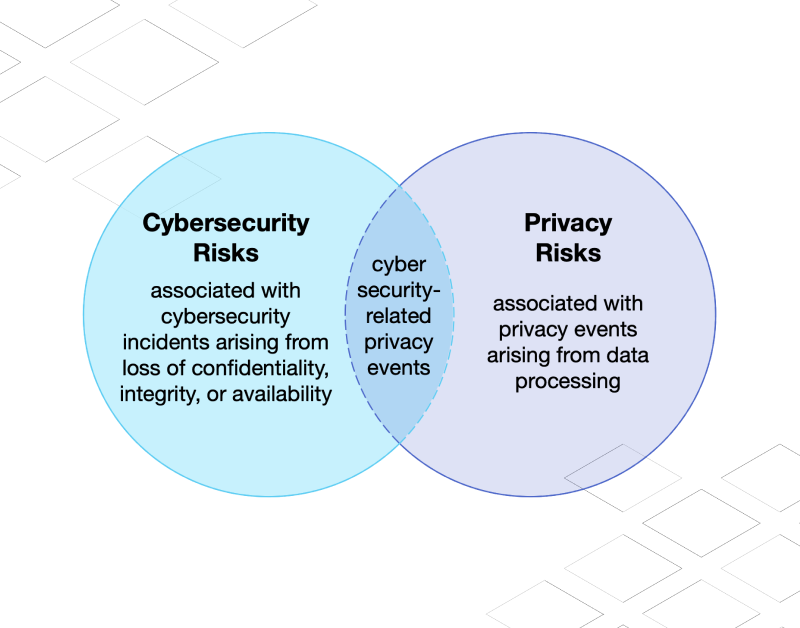
But there’s a deeper level to uncover: the lifeblood of our deeply connected global system is data. At this concealed level, global business is deeply challenged by the complexities of cross-border information flows, cybercrime, data privacy, new frameworks, and increasing or changing cybersecurity regulations.
Business leadership today needs to pay particular attention to data and flows. Consider that a recent McKinsey report notes the fastest-growing global flows are now data, services, intellectual property, and international students. Estimates vary on how much data is flowing at any given second (an “intangible”) but there’s no denying its centrality.
It is also clear that ensuring the free flow of data across borders is a paramount concern to business and government. After all, industry derives exceptional value from its use, allowing for rapid innovation such as what we are now seeing with advancements in AI. It also affords the tantalizing possibility of solving some of the world’s most pressing crises.
But how is data best protected?
Along with technological changes and risks to business operations, it’s critical to understand that it’s the regulatory environment that allows data to flow and businesses to operate at global scale. Regulations also provide an opportunity for businesses and governments to help protect data, whether intellectual property or PII, from cyber-enabled threats.
Indeed, compliance with data regulations can actually help businesses grow and fight the scourge of cybercrime.
Your organization needs to think deeply about the role of data, privacy, protection, and flows. Consider the following acts and regulations and their implications for your organization:
- General Data Protection Regulation (GDPR)
- EU-US Data Privacy Framework
- The SEC’s Proposed Rules
- Digital Operation Resilience Act (DORA)
- California Consumer Privacy Act (CCPA)
- Illinois Biometric Information Privacy Act (BIPA)
- Federal Trade Commission Act (FTC Act)
- Children’s Online Privacy Protection Rule (COPPA)
- Electronic Communications Privacy Act (ECPA)
- Gramm-Leach-Bliley Act (GLBA)
- Fair Credit Reporting Act (FCRA)
- Family Educational Rights and Privacy Act (FERPA)
- Health Insurance Portability and Accountability Act (HIPAA)
Lastly, governments have developed free resources for you to identify and manage privacy and data risks. For example, NIST offers a voluntary Privacy Framework tool. And the EU offers a GDPR checklist tool for data controllers.
In our second blog entry on the centrality of data and the challenges of keeping it secure and flowing, my colleague Dr. Rois Ni Thuama and I have the pleasure of talking with one of the world’s foremost experts on the topic, Linda Priebe of Culhane Meadows, PLLC.