Phishing is a form of social engineering and one of the most common cyber crimes on the web today. According to Cisco, 86% of organizations had at least one user try to connect to a phishing site in 2021.
Data from Google’s Transparency Report supports this, revealing that the search engine giant detected an average of 46,000 phishing websites weekly in 2020. It’s a staggering number considering the number of phishing sites Google caught already reached 2.02 million at the beginning of the same year.
These numbers show the importance of preventing phishing attacks. Additionally, since 90% of corporate security breaches are due to successful phishing attacks, having an effective phishing remediation plan is also crucial. To give you more insight, we’ve put together a list of what you can do to protect your organization from phishing attacks.
Phishing vs. Spam
To effectively fight against phishing, you must first identify and differentiate it from spam.
- Spam – unsolicited email, text, or social media messages. While most are harmless, they are annoying in their intrusiveness and sheer volume. However, many contain images and other content that some find offensive and triggering. Many consider spam as potentially damaging because of this.
- Phishing – emails, texts, and messages created and sent by cybercriminals to obtain confidential information – specifically, a target’s personal information like email and social media login details, banking information, address, phone number, etc.
Types of phishing attacks
Phishing is also classified into various types according to intent and target:
- Spear phishing – Cybercriminals who obtain enough information about a target to determine their hobbies or preferred brands and service providers can customize phishing emails, texts, or messages to increase their chances of success. Spear phishing mimics a known trusted sender – the target’s bank or a friend, for example – to convince the victim to reveal confidential information.
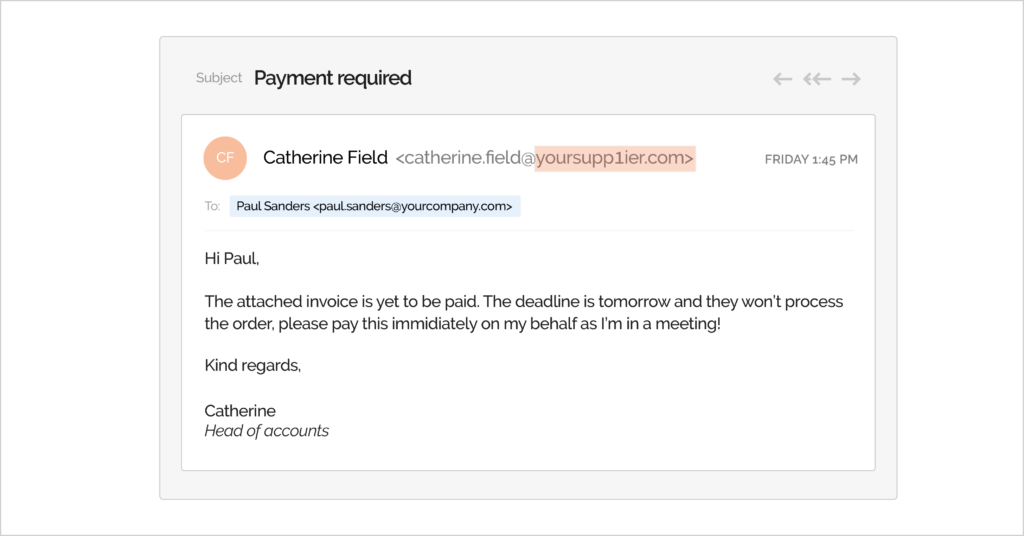
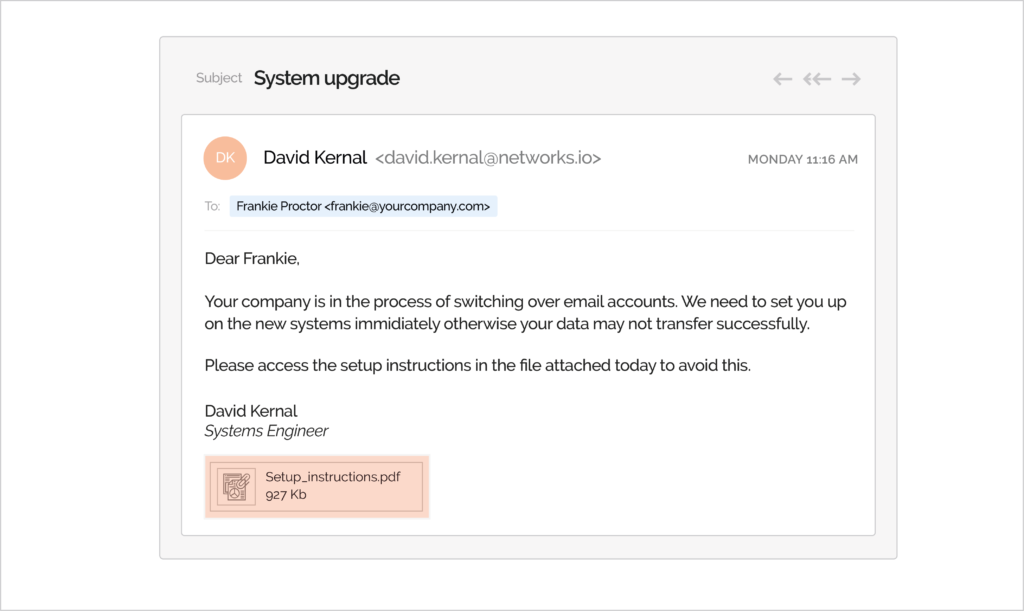
- Clone phishing – A standard modus among cybercriminals, clone phishing replicates a legitimate email from a trusted source, mimicking everything from layout to attachments. They include malware in the attachments, which will harvest login credentials from the target’s device when clicked. Another method is asking the target to fill out a form or reply with their personal information.
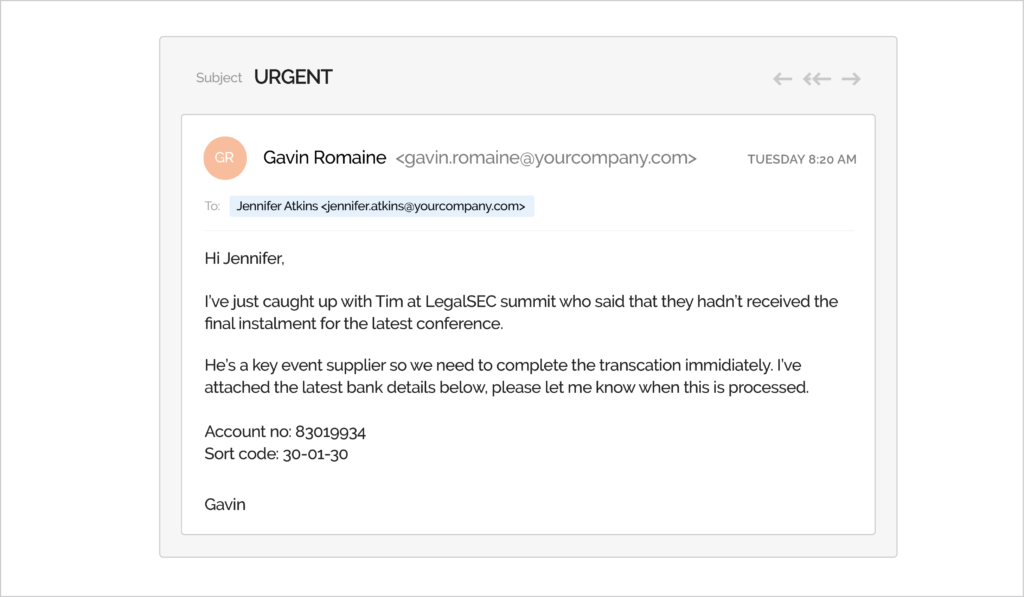
- Executive phishing – Also known as whaling, executive phishing is a more sophisticated strategy as it targets top-level executives. Instead of sending generic spam emails, hackers pretend to be company executives asking for information from subordinate officials in the company. One example was a Mattel finance executive who was fooled into believing that the newly appointed CEO sent an email authorizing a large transfer in 2017. Mattel lost nearly $3 million that year.
Having defined phishing vs. spam and identified various phishing methods, you’ll have a better idea of how to prevent them.
Phishing remediation and prevention must-do’s
Preventative measures are always worth the time and effort, and if something valuable is at stake, consider investing in technology and more stringent protections. Here are some examples:
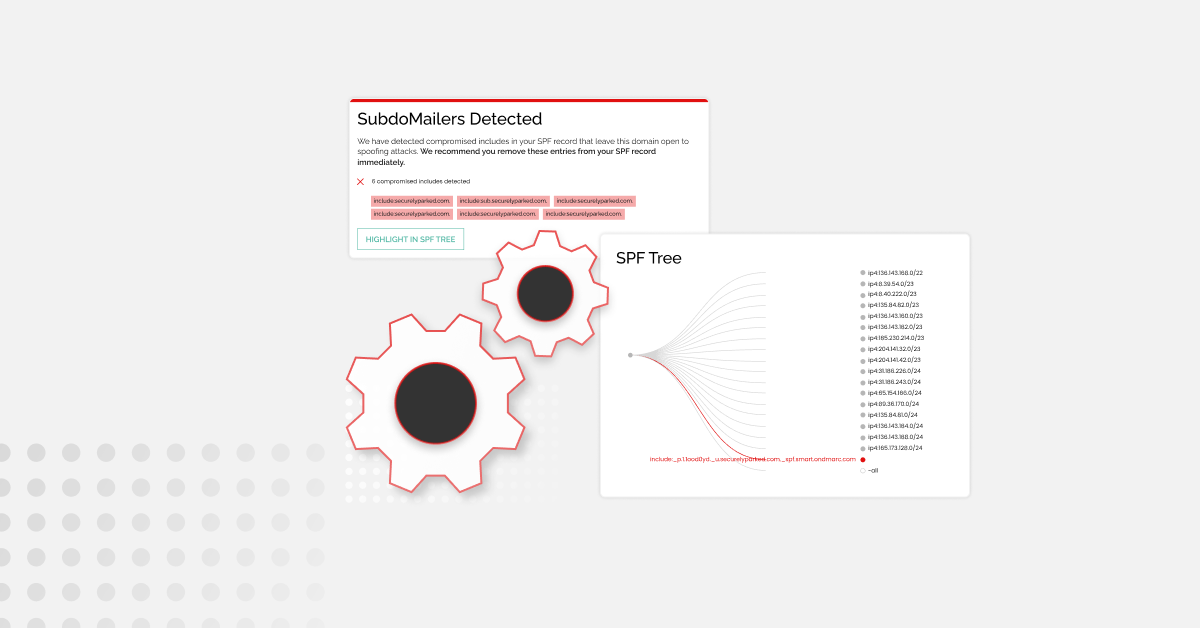
- Implement DMARC – When we think about what makes a phishing email successful, we’ll often jump to social engineering or well-written copy. But by and large, the most successful phishing attacks occur because a cybercriminal ‘spoofs’ an organization’s exact domain, making it almost indistinguishable from the real thing. DMARC stands for Domain-based Message Authentication, Reporting, and Conformance. It’s a globally recognized email security standard that works by using existing protocols SPF and DKIM to stop bad actors and cybercriminals from spoofing an organization’s domain to send emails. To work effectively, the DMARC standard needs to be implemented at a policy of p=reject, and this is most reliably and easily done by using a good DMARC application.
- Install anti-phishing software – Many free browser add-ons screen websites for potential malware and phishing activity. Alternatively, you can invest in email security software to automatically screen unsolicited emails and check them for malware. Email security software also notifies users of possible brand impersonation and other suspicious content in emails. You should also invest in domain perimeter protection, which gives you visibility into lookalike domains that could be used for phishing, as well as swift takedown functionality.
- Phishing and security awareness training – Verizon’s 2021 Data Breach Investigations Report revealed that 82% of all data breaches were successful because of human negligence or error. Lack of awareness, therefore, is a huge security liability. Phishing training isn’t the only solution, but it does help to solve this by increasing awareness and teaching phishing prevention. It empowers employees to be active participants in protecting your network. It only takes one person to overlook a malware attachment in a phishing email for the entire organization and the business’s future to be at risk. So educate everyone who regularly uses your network, and implement the right software to help spot threats too. Make it as easy as possible for employees to recognize phishing emails and know what to do when they encounter them.
- Make password rotation a policy – Reminding employees to practice password hygiene can only do so much: you can never be sure that they won’t use their mother’s maiden name or child’s birthday as their email password. Enforcing password rotation will be helpful. Schedule password resets every quarter, for example, and set requirements like a character limit and alphanumeric requirements. This ensures employees will make “strong” passwords and change them regularly. If password rotation isn’t achievable for all tools and programs, could also use a reputable password manager.
- Install firewalls and pop-up blockers – Companies can install these features network-wide, but it helps to encourage employees to have firewalls and pop-up blockers on their laptops and desktops.
- Invest in network perimeter security software – Adding a robust layer of protection throughout your network will keep malware-ridden phishing emails at bay. Perimeter security software protects your network’s boundaries, not just the physical network consisting of on-site computers, data banks, and other hardware. So if you have employees working remotely, it won’t be a problem if some only have basic firewalls and anti-malware in their personal computers.
- Keep your security programs and browsers updated – Pressing that update button doesn’t take a second, but it is crucial for maintaining the integrity of your network security. Your service provider constantly updates security patches because cyber threats and hackers continuously evolve. They get smarter and more sophisticated as time passes. Your organization needs to keep up, and keeping your programs up to date is the key to achieving that.
Protect your network with reliable security solutions
If a phishing attempt successfully breaches your network, immediately scan your network, servers, applications, and connected devices for malware. Next, you must identify the breach to reinforce that weak spot and avoid a recurrence. Consider the tips above to strengthen your network security if you haven’t done so already.
It’s also best to consult a cybersecurity expert and seek advice on upgrading your current security or investing in one.
Red Sift, a digital resilience platform offering cutting-edge products and services to companies and organizations, can provide what you need to secure your confidential business data, employee information, and overall operations resilient against evolving cyber threats. We also anticipate technological and human threats, making our anti-phishing solutions effective.
Contact us today to learn more about the Red Sift platform and obtain robust anti-phishing cybersecurity.