
On Tuesday 24th of July 2018, Google took a big step towards making the internet more secure with their release of Chrome 68. It will now flag a warning to users when they visit a website that uses unencrypted HTTP instead of HTTPS. This has been in discussion for a long time and we at Red Sift think that this is a great initiative as it will encourage website owners who use the HTTP to upgrade to the more secure and encrypted HTTPS or risk visitors fleeing when they see the words “Not Secure” appear in the browser bar.
What are HTTP and HTTPS?
HTTP stands for Hypertext Transfer Protocol and is one of the key elements that underpin the internet. This protocol is what allows you to fetch and load pages that are hosted on different servers. The modern HTTPS protocol solves the main problem of HTTP, the fact that it is inherently insecure and does not use encryption to protect users against malicious content and systems.
HTTPS isn’t new, so why now?
HTTPS, or Hypertext Transfer Protocol Secure, has been around for about 10 years, but people have only been using it for certain parts of their websites. You’d usually only find HTTPS used on pages where you filled in passwords or other sensitive information. If you think back to IT class in school, you’ll remember that one of the key things you were told was to never enter passwords or sensitive information into a website unless we saw the padlock symbol in the address bar.
The reason HTTPS wasn’t used more widely sooner was that not so long ago, it would have caused a significant strain on servers and network speed, not to mention you’d actually have to pay for your HTTPS certification. But happily, with modern technology, HTTPS doesn’t cause any server strain or impact speed meaning that in most cases, you won’t experience any loss in performance. Furthermore, initiatives such as “Let’s Encrypt” have brought together forces such as Google, Facebook, Github, and Cisco to offer free HTTPS certification.
So why does Red Sift love this development?
From now on, Google’s newest version of Chrome will warn users when they land on HTTP page with a note in the browser bar – compare this to what you see when you visit a site secured with HTTPS. Additionally, users may also see a popup that explains why the site is not secure.
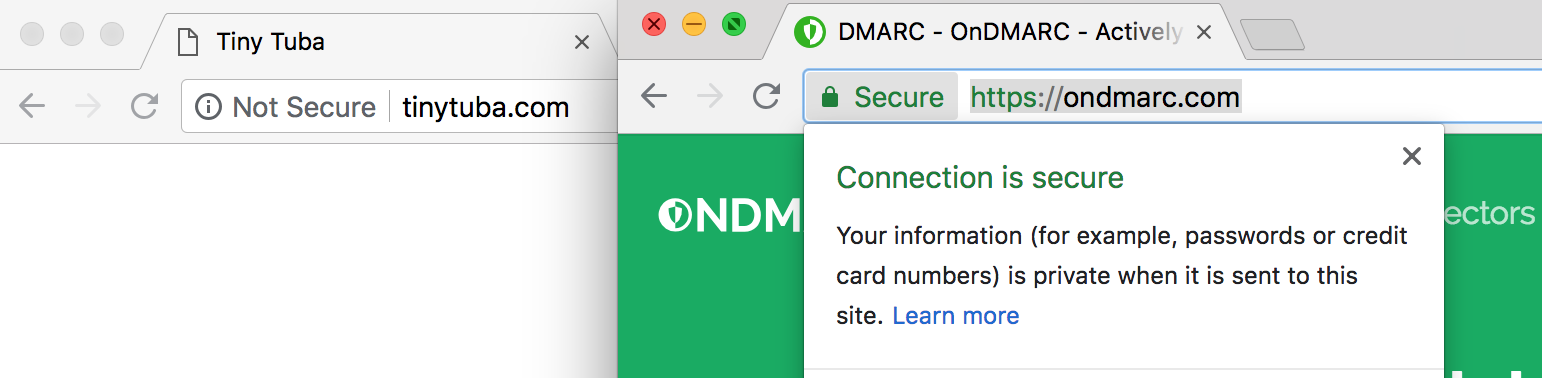
As a cybersecurity company with a mission to democratize it for all, we’re really happy to see initiatives like this being rolled out. They proactively encourage website owners to update their security or risk being labeled as an untrusted site. Although approaches like this may seem harsh to some there is no arguing that this approach will have a greater impact and contribute to a more secure online environment for all of us.
So how do you get your hands on Chrome 68?
You can update your Chrome version to 68 by:
- On your computer, open Chrome
- At the top right, click More
- Click Update Google Chrome. If you don’t see this button, you’re on the latest version.
- Click Relaunch
Simple! Now, the next time you unknowingly visit an HTTP website you’ll see the warning and can decide for yourself if you still want to carry on browsing.
Find out more about Red Sift
Keen to find out more about Red Sift, what we do, and how our products help businesses keep their email infrastructure and domains secure? Get in touch with us below!





