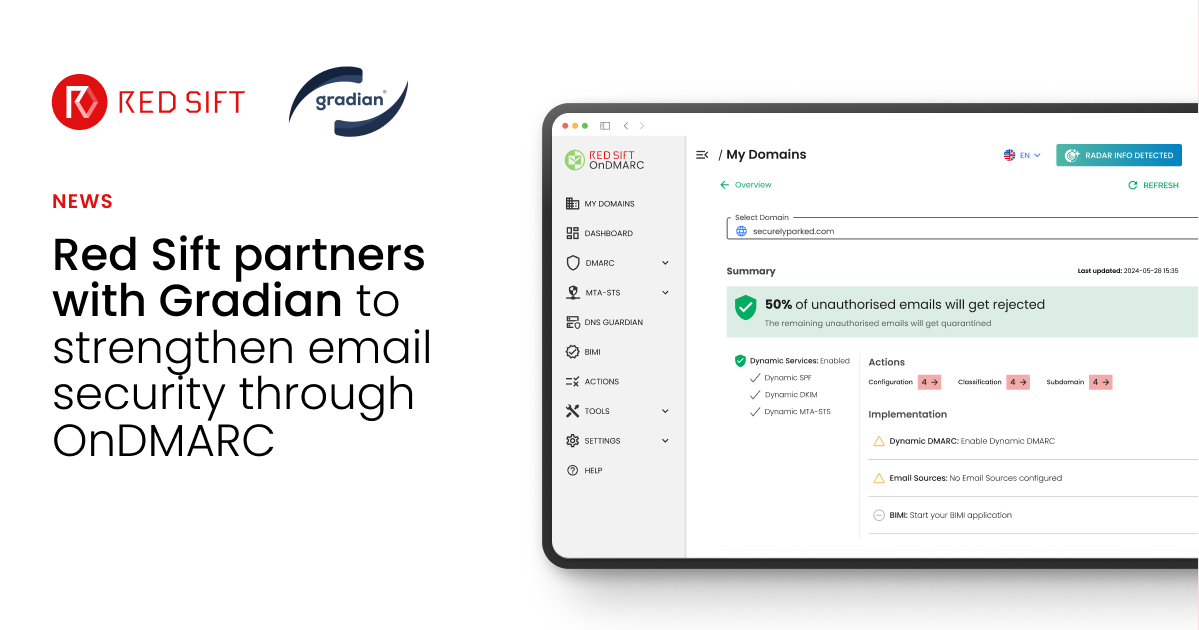
DMARC: The best ROI for your organization
Executive summary: Implementing DMARC delivers one of the clearest, fastest returns on investment in email security. By authenticating outgoing mail and blocking spoofed messages, DMARC cuts the direct costs of phishing and Business Email Compromise, safeguards brand reputation, and boosts deliverability—ultimately driving revenue and trimming operational workload. Key takeaways: Email is a critical communication tool for…
Read more