Sometimes referred to as “brand exploitation” or “brandjacking”, brand abuse can come in many forms. But, ultimately the term describes the infringement of a company’s brand by an outside party or attacker. This party will use your business’ reputation for its own gain, at the expense of your brand equity.
1. Brand abuse is growing
Unfortunately, recent statistics show that brand abuse is becoming more and more prevalent.
- During the third quarter of 2021, the number of fake sites, apps, and social media pages impersonating brand-name companies jumped 274% on an annualized basis.
- There was an 85% increase in consumer losses associated with brand abuse from October 2020 through to September 2021. This cost more than $2 billion in the US alone.
2. Brand abuse thrives in a digital landscape
Today’s world is overwhelmingly digital. The shift to eCommerce that we’ve seen in recent years holds a host of benefits for businesses. But with these benefits comes a downside: the bigger the digital footprint a business has, the larger the surface area for brand abuse becomes.
It’s also very easy to impersonate a brand over the Internet. Attackers can send emails that appear to be from a trusted business. Furthermore, anyone can register a domain that resembles that of an organization. The difference between “arnazon.com” and “amazon.com” is easy to miss. Because of this, many fake websites are successful at impersonating reputable brands to commit fraud, stealing data and money from unsuspecting victims.
3. Brand abuse is everyone’s problem
Brand abuse affects everyone. But how?
Consumers can be affected if a trusted company is impersonated. They may give away credentials or be scammed out of money.
Organizations can lose hard-earned trust due to brand abuse and impersonation. Data shows that 72% of customers will switch brands after just one bad experience. This means that brand abuse can significantly impact revenue.
Traditionally, the responsibility for ensuring a company’s brand protection has sat with legal and brand professionals. However, brand protection should also be a concern for several other departments within a company, including marketing and IT.
4. Brand abuse often occurs due to gaps in email security
Over 333 billion emails are sent every day. Emails are widely used by businesses for everything from operations to communications and offers. So it’s no surprise that email is a key attack vector for brand abuse.
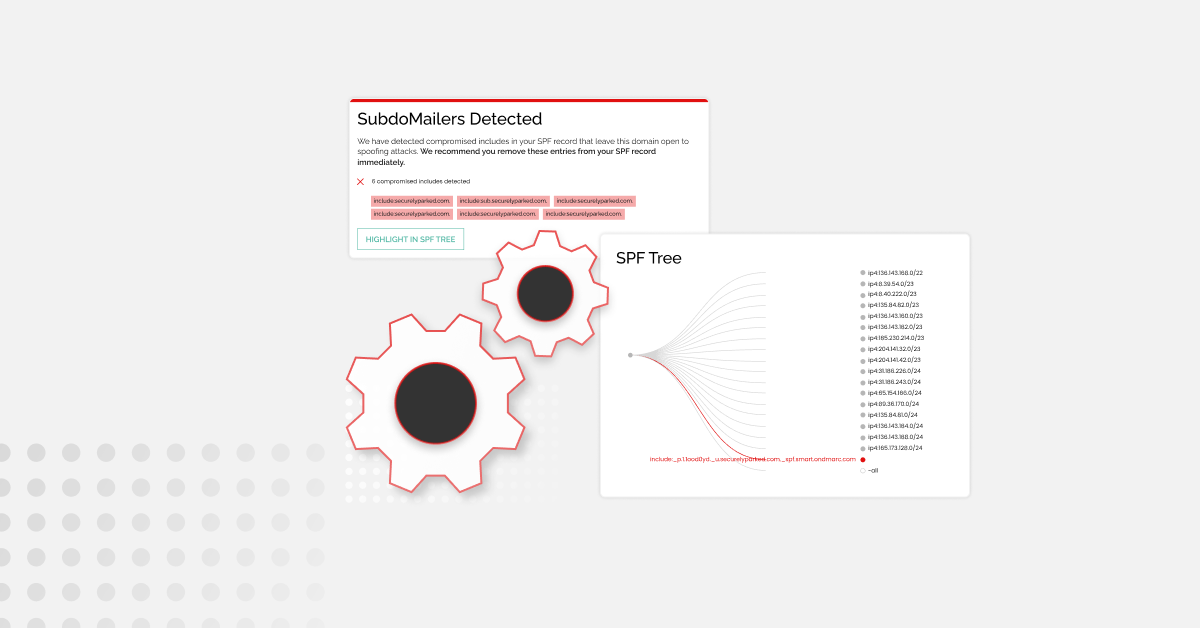
If you don’t have DMARC implemented at its strongest policy of p=reject, attackers can send emails that appear to come from your organization’s domain. This allows them to impersonate your brand to launch phishing attacks on your customers.
DMARC also has the added benefit of allowing you to implement BIMI. BIMI is a standard that displays validated trademarked logos for all DMARC-authenticated emails. We found that the use of BIMI increases consumer confidence in the legitimacy of an email by 90%.
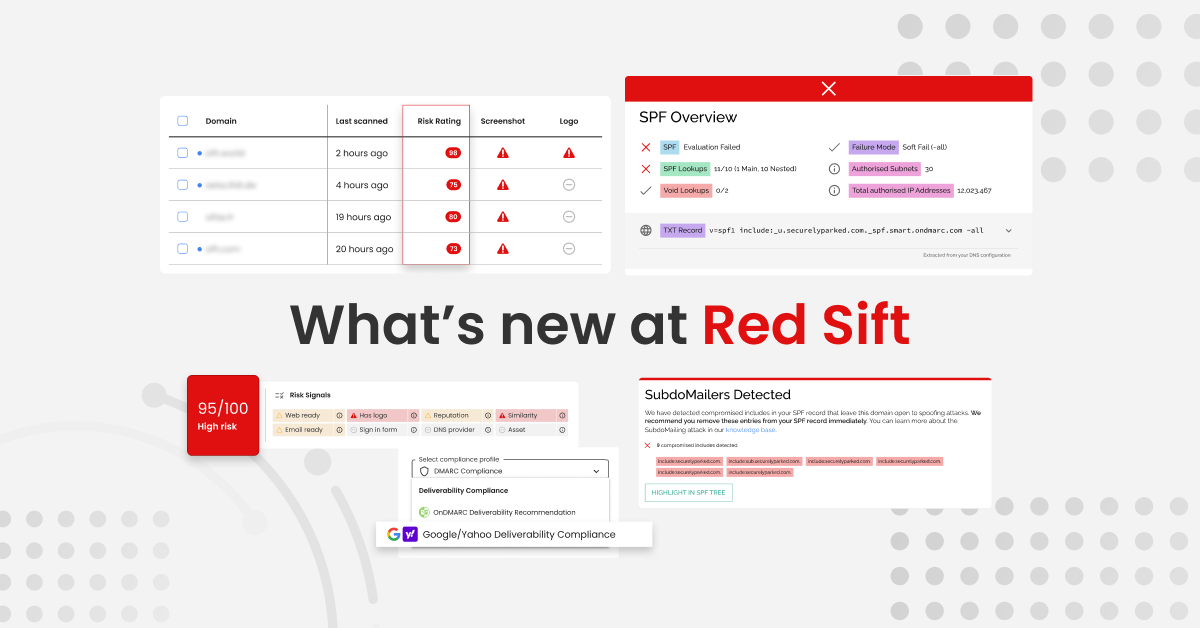
Not sure if you have DMARC configured correctly? You can use our free Investigate Tool to check your email security setup.
5. Automation can help protect your brand from abuse
Brand protection software that employs machine learning and automation should form part of your online brand protection strategy.
A logo detection service can scan the Internet for unauthorized use of a company’s assets. It then flags these uses to you, increasing the speed with which a takedown can be initiated.
Lookalike domain discovery and takedown functionality can stop domains from impersonating your organization. Research shows that a new phishing website goes live every 20 seconds. To combat this, businesses should use software to scan for lookalike domains and assist you in getting them taken down.
Inbound email threat detection and response can give your employees the tools they need to spot phishing attacks. Brand protection software of this kind is able to assess whether an email’s sender is who they claim to be. It can also employ machine learning to detect suspicious content.
Make Red Sift’s platform part of your brand protection strategy
As the only Integrated Email Security and Brand Protection Platform, Red Sift automates BIMI and DMARC processes, makes it easy to identify and stop business email compromise, and secures domains from impersonation to prevent attacks.
To find out more about how our platform can contribute to your organization’s brand protection strategy, download our eBook today.