In today’s digital landscape, the pace of change is relentless. The number of domains, subdomains, IP addresses, and cloud resources used by each organization increases minute by minute. While this expansion can bring new opportunities, it also opens the door to potential vulnerabilities that, if left unchecked, can pose significant security risks. I’ll talk more about those risks in my upcoming webinar, but in this blog, I explore why the attack surface is expanding, the risks associated with misconfigurations in these assets, and how a real-time view of your estate can help mitigate the dangers that come from risks.
The expanding attack surface
The relentless growth of an organization’s digital presence can be attributed to several factors:
Domains and subdomains: As organizations expand their online presence, they often acquire new domains and subdomains to serve various purposes. Each of these represents a potential entry point for cyberattacks.
Certificates: SSL/TLS certificates are essential for securing web communications. With the rise of HTTPS adoption, organizations are managing an increasing number of certificates, each requiring proper configuration to remain secure.
IP addresses: IP addresses are the building blocks of the internet, and organizations require them to host various services. The proliferation of IP addresses adds complexity to network security management.
Cloud resources: Managing a multitude of cloud resources, such as virtual machines, storage, and databases, can lead to misconfigurations that leave assets exposed and at risk. And it’s getting harder due to the endless numbers of complicated products.
The risks of misconfigurations
Misconfigurations in this expanding attack surface are like silent threats lurking in the shadows. They might go unnoticed for a while, but when exploited, they can have dire consequences. I’ll cover particular risks in detail during the webinar but they broadly cover:
Security compromises: Misconfigured assets can be easy targets for cybercriminals. Attackers can exploit these weaknesses to gain unauthorized access, steal data, or launch attacks within an organization’s infrastructure.
Compliance violations: Many industries have stringent regulatory requirements regarding data protection. Misconfigurations can lead to non-compliance, resulting in legal consequences and hefty fines.
Financial loss: Security breaches and compliance violations can lead to substantial financial losses, including legal fees, fines, and damage to an organization’s reputation.
Reputational damage: News of a data breach or security incident can severely damage an organization’s reputation. Rebuilding trust with customers, partners, and stakeholders can be a long and challenging process.
Cyber insurance issues: There are problems with cyber insurance scope and cost caused by misconfigurations.
Real-time visibility and mitigation
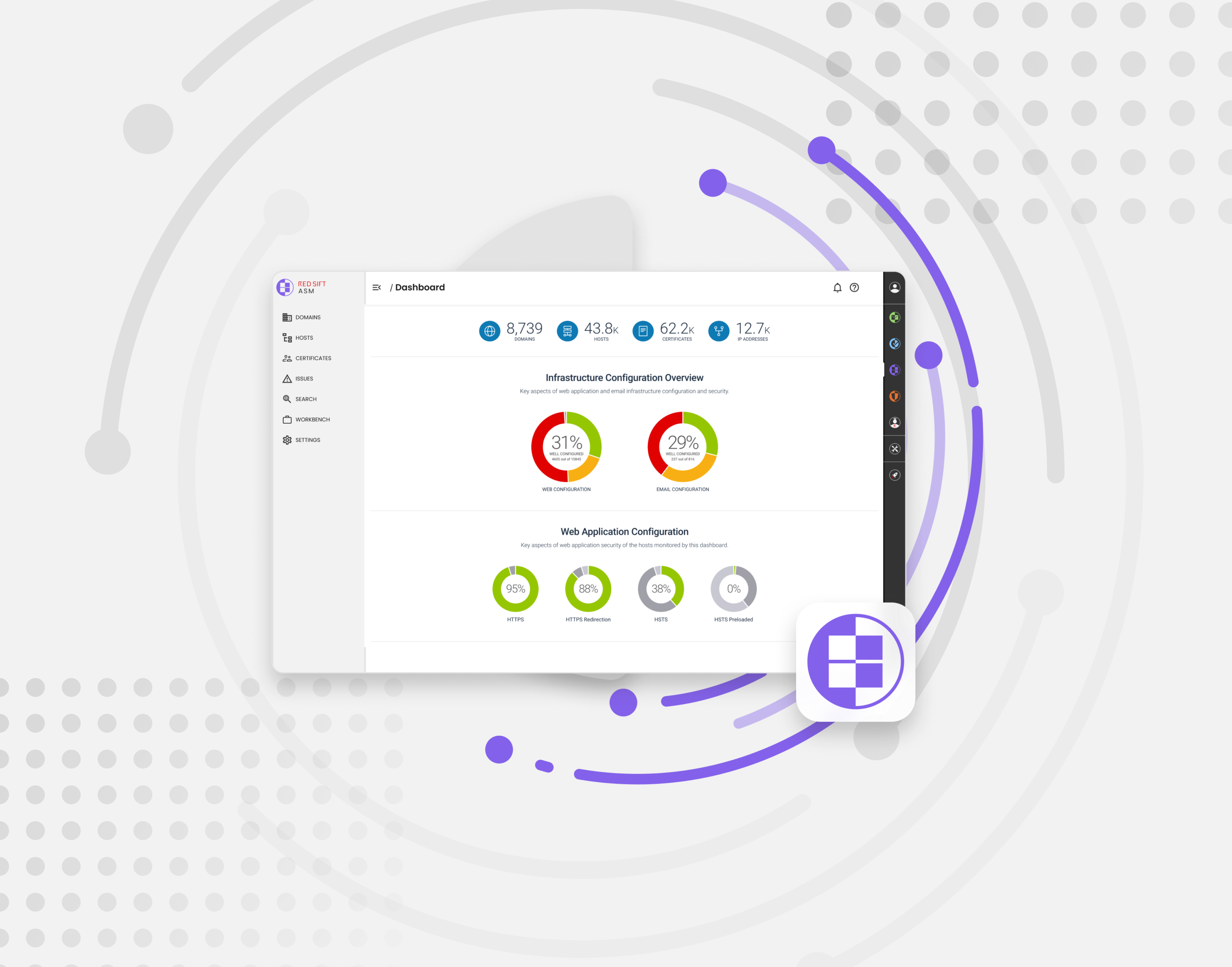
To combat these hidden dangers effectively, organizations need a real-time view of their estate that continuously updates as new assets are published to the internet. This is where Red Sift ASM comes into play.
Red Sift ASM offers a comprehensive solution for identifying and mitigating the risks associated with asset misconfigurations.
Complete visibility: Build an inventory of your external-facing and cloud assets without spreadsheets or manual processes. Connect to cloud providers, certificate authorities, registrars, and managed DNS providers to import and monitor all of your assets.
Monitor continuously to stay secure: Automatically monitor your domains, hosts and IP addresses for misconfigurations to avoid security risk. Real-time internet activity feeds identify new properties that belong to you and automatically adds them to your inventory.
Information to take action: In-depth, real-time data about each asset makes it straightforward to take action as soon as a misconfiguration or unmanaged asset is identified.
In conclusion, the expanding attack surface poses ever-growing risks to organizations. Misconfigurations in domains, subdomains, certificates, IP addresses, and cloud resources can have severe consequences. Red Sift ASM offers a powerful solution to illuminate these hidden dangers.
Join my informative webinar and equip yourself with the knowledge and tools to safeguard your organization’s security, compliance, financial stability, and reputation in today’s dynamic digital world.