Covid-19 has had a major effect on the world. With millions of people told to self-isolate, the working day for many has been turned on its head. Remote working is now in full swing and companies are running officeless. Whereas this is great for productivity, it increases the danger that cybercriminals pose to companies. With more and more communication being done through email, the opportunity for phishing attacks has never been higher.
Here at Red Sift, we’ve built a machine learning model to distinguish fake COVID-19 messages from the true ones based on the email content. This blog post explains why we took a Machine Learning approach and how we built the model.
Why use Machine Learning?
A traditional rule-based approach to classify email intent isn’t scalable because a large number of rules need to be manually crafted and maintained over time. Attackers are smart and they will constantly find a way to adapt their phishing strategy. For example, to get past a ‘covid-19’ keyword filter, attackers can simply change the keyword to a lookalike one such as ‘côvíd-19’.
Machine Learning uses mathematics and statistics to learn patterns from the data and make educated predictions about unseen data. Machine Learning models need labeled data instead of hand-crafted rules. Machine Learning algorithms can train a model to learn sophisticated and subtle patterns from example phish emails. The model can be easily updated to be more accurate with additional training data collected over time. As a result, an ML-based approach is more robust and dynamic.
Real life examples
This section shows some real-world examples of true and fake COVID-19 messages. Our model correctly classifies them all.
Example 1
Fake WHO message with malicious attachment using accent characters côvíd and misspelling word coronaaviris within the document.

Example 2
Fake government message with malicious links.
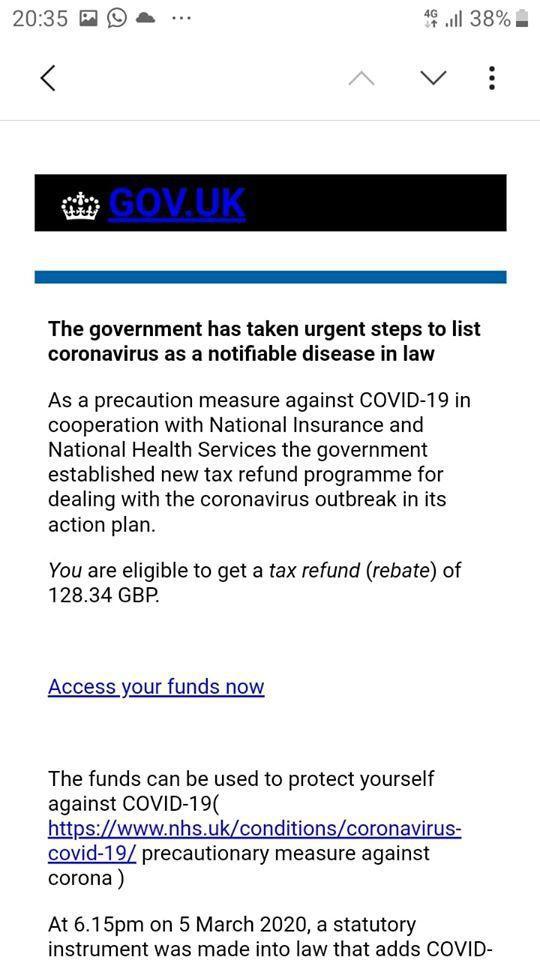
A legitimate Covid-19 email
A true COVID message from an organisation.

How we built the model
There are two important building blocks of a machine learning model: data and algorithm.
Data
To effectively train a model, we need to provide a good collection of examples for both fake and true COVID-19 related messages. For true messages, we crowd-source hundreds of messages sent by a large number of different organizations. For fake messages, we filter them from reliable reported phishing messages. To increase variety, we collect fake messages in image format in a number of articles and extract text from them. Luckily, part of working at a cybersecurity company means that there was no shortage of scam messages!
Algorithm
We investigate a number of preprocessing techniques together with different modelling approaches. The preprocessing techniques include both generic text (stop words removal, lemmatization) and email specific (signature exclusion). The modelling techniques range from standard algorithms (logistic regression, naive Bayes, SVM, random forest) to shallow neural networks (word2vec, fasttext) and deep learning (RNN, LSTM). In particular, we make use of the state-of-the-art research in transfer learning including ULMFiT, transformer and BERT.
At Red Sift, we enable security-first organizations to successfully communicate with and ensure the trust of their employees, vendors, and customers. Our portfolio includes a number of gold-standard email and domain protection products: OnDMARC and Brand Trust. These are designed to work in unison to block outbound phishing attacks and provide domain impersonation defense for company-wide threat protection.







