Executive Summary: Advancements in quantum computing threaten existing cryptographic protections. While CRQCs aren’t expected imminently, organizations must proactively transition to quantum-safe cryptography to secure future communications.
This article:
- Explores the threats quantum computing poses to current cryptographic algorithms.
- Discusses the timeline for the emergence of cryptographically relevant quantum computers (CRQCs).
- Emphasizes the need for transitioning to quantum-safe cryptography.
Introduction
Recent advancements in quantum computing pose a substantial threat to the cryptographic algorithms that secure internet communications, particularly public key cryptography. As quantum computers evolve, they could eventually compromise these cryptographic protections, putting all internet communication at risk.
While cryptographically relevant quantum computers (CRQCs) are not expected imminently, the transition to quantum-safe cryptography is extensive and requires long-term planning. One of the biggest risks is “harvest now, decrypt later“—where attackers collect encrypted data today with the intent to decrypt it once quantum computers become powerful enough. This is particularly concerning for data with long-term confidentiality needs, such as financial transactions and government communications. Even if encryption is secure today, it may not remain so in the quantum era, making proactive migration essential.
“Post-quantum cryptography represents one of the most significant shifts in internet security we’ve ever seen. The transition is complex and will take years, but starting early is the key to ensuring a smooth migration. Organizations that begin adopting hybrid cryptographic solutions today will be the ones leading in tomorrow’s secure internet ecosystem.”
Chris Bailey, Cybersecurity Veteran
Why today’s cryptographic algorithms need to evolve
The cryptographic algorithms that secure internet communications today were not designed to withstand quantum attacks. While symmetric encryption and modern hashing algorithms remain secure with minor adjustments, public key cryptography—the backbone of secure key exchanges and digital signatures—is highly vulnerable.
- Current key exchange and signature algorithms are not quantum-safe
- Public key cryptography algorithms like RSA, ECDH, ECDSA, ElGamal, and EdDSA are vulnerable to quantum computers due to Shor’s algorithm. These algorithms must be replaced with post-quantum cryptographic alternatives to ensure long-term security.
- Modern symmetric and hashing algorithms are quantum-safe with minor considerations
- AES-128 and higher, as well as modern hashing algorithms like SHA-256 and SHA-3, are considered quantum-safe.
- While Grover’s algorithm theoretically reduces their effective security by half, these algorithms remain robust against quantum attacks without needing doubled key sizes.
State of NIST PQC standardization
As quantum threats become more pressing, the National Institute of Standards and Technology (NIST) has been leading efforts to establish post-quantum cryptography (PQC) standards. After years of evaluation and collaboration with the cryptographic community, NIST released its first set of PQC standards in August 2024, marking a major milestone in the transition to quantum-resistant security.
The following algorithms have been standardized:
- ML-KEM (CRYSTALS-Kyber), Module-Lattice-Based Key-Encapsulation Mechanism
- ML-DSA (CRYSTALS-Dilithium), Module-Lattice-Based Digital Signature Standard
- SLH-DSA (SPHINCS+), Stateless Hash-Based Digital Signature Standard
Additional algorithms are still in development and expected to be finalized soon:
- FN-DSA (FLACON) Fast-Fourier Lattice based Digital Signature Standard
NIST is also actively evaluating additional signature algorithms. The focus is on post-quantum signatures that extend beyond structured lattices, prioritize short signatures and fast verification, or significantly outperform or provide enhanced security compared to the algorithms adopted so far. It also plans to select one more key encapsulation mechanism (KEM) soon. For more details, visit the NIST post-quantum cryptography project.
How do I prepare?
Even if the timeline for quantum computers with cryptography-breaking capabilities (i.e. CRQCs) remains uncertain, NIST has proposed guidelines for a migration deadline for quantum-vulnerable algorithms.
- 112-bit security ciphers: Deprecated after 2030 and disallowed after 2035. Includes ECC key sizes ≤ 224 bits and RSA key sizes ≤ 2048 bits.
- 128-bit security and higher: Disallowed after 2035. Includes nearly all current public key cryptographic algorithms.
In Australia, the deadline for all quantum-vulnerable algorithms migration is 2030.
Although these deadlines may seem distant, the ‘harvest now, decrypt later’ risk means organizations must begin migrating key exchange algorithms now. Without action, encrypted data could be harvested today, only to be compromised when quantum computers become capable.
To address this, organizations should focus on two key areas of migration: key exchange and digital signatures.
Migration #1 (Key exchange)
The internet is already transitioning to hybrid key exchange using ML-KEM to address immediate threats. Some major browsers, including Chrome, Chromium derivatives, and Firefox, have started supporting it. Cloudflare reports that around 30% of connections to their servers now use quantum-safe key exchange (X25519+MLKEM768).
For organizations assessing their post-quantum readiness, Red Sift Certificates already detects quantum-safe key exchange. This information is available for all Hosts and Endpoints in the Certificates dashboard.
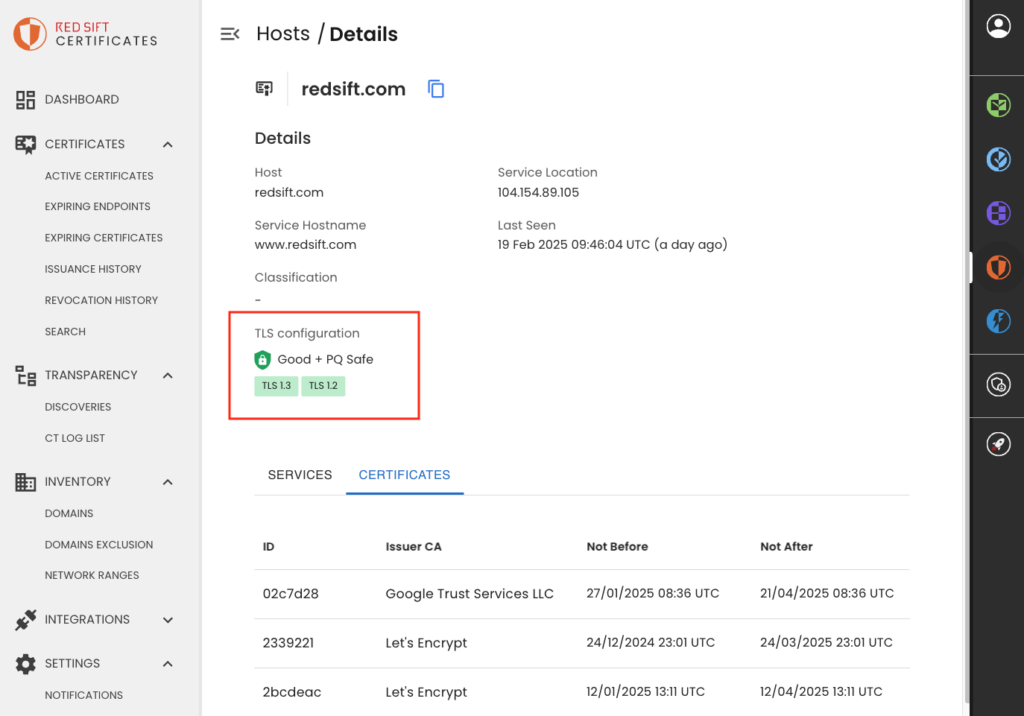
Red Sift Certificates
Migration #2 (Digital signatures)
Migrating digital signatures is not urgent but presents significant challenges. The large key sizes of PQC cryptographic algorithms pose concerns for TLS performance. These post-quantum algorithms need to operate on larger mathematical objects to maintain security against quantum computers, resulting in increased key and signature sizes compared to classical cryptographic algorithms.
Signature migration in the WebPKI ecosystem is a complex process involving various stakeholders, including library developers, browser vendors, server operators, CAs and HSM manufacturers. The TLS protocol includes numerous signatures—a design choice driven by the efficiency and compact size of widely used elliptic curve signatures—resulting in multiple signatures throughout the WebPKI, including those in the server certificate chain.
As discussed earlier, NIST is still evaluating additional algorithms. Some alternate proposals are also being discussed, namely KEMTLS which uses post-quantum KEMs instead of signatures for handshake authentication, and Merkle Tree Certificates that integrate the roles of X.509 and Certificate Transparency.
IETF standard for PQC certificates
Efforts are underway to standardize PQC certificates, with several proposals being discussed:
- Hybrid certificates: Extend the current X.509 standard by adding three non-critical extensions, allowing PQC algorithms to be used alongside traditional public key algorithms.
- Chameleon certificates: Expand on hybrid certificates by introducing Base and Delta certificates, optimizing flexibility in quantum-safe implementations.
- Composite certificates: Depart from the X.509 standard entirely, proposing a new certificate format designed specifically for post-quantum security.
Staying ahead in the post-quantum transition
With standards being finalized and migration deadlines approaching, organizations that start preparing now will be best positioned for a smooth transition.
At Red Sift, we’re tracking these developments and equipping customers with the tools to navigate this shift, from detecting quantum-safe key exchanges to supporting emerging standards. If you require support or assistance, please reach out to us and we’d be happy to help.
This overview reflects the current state of PQC for Internet/WebPKI, including insights from the Public Key Infrastructure Consortium’s Post-Quantum Cryptography Conference in Austin, TX, January 2025. We’ll continue to monitor the landscape and provide guidance to ensure businesses stay prepared.