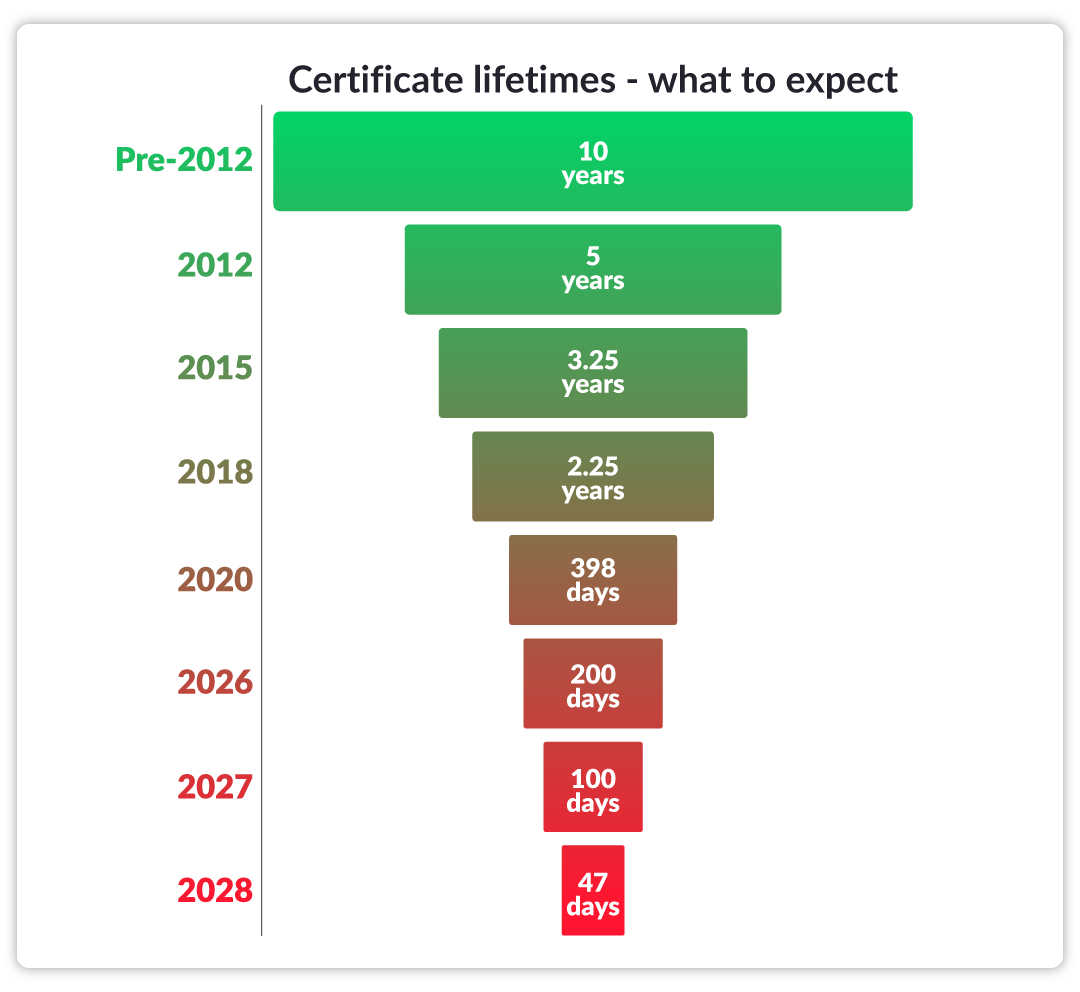
The lifetime of SSL/ TLS certificates continues to grow shorter. Chrome initially proposed reducing certificate lifespans to 90 days to enhance security and mitigate risks associated with compromised certificates. Apple took this initiative further, proposing a draft ballot to shorten the maximum validity period for public SSL/TLS certificates to just 47 days by 2028.
The move is expected to make a significant impact on digital security by pushing for even stricter measures to ensure the authenticity and safety of certificates. It could also reshape industry standards for certificate management, and if rumors are true, other prominent internet providers may support further efforts to reduce certificate lifespans.
The announcement adds to a series of ecosystem changes that teams are already navigating, such as Entrust distrust and the upcoming PCI-DSS 4 mandate.
The downside of lifespan reduction
A rapidly expanding digital ecosystem brings the challenge of managing ongoing changes, not to mention the significant increase to certificate management by a staggering eightfold (up from x4 increase by Google). By reducing certification lifespans to just 47 days, Apple has significantly increased the pressure on security teams already concerned with Google’s 90-day limit.
In addition, existing automation tools could lead to workflow failure, with end-to-end processes missing certificates that need to be replaced. This includes an increased risk of mismanagement, leading to certificate expiry and costly service downtime alongside reputational damage.
What benefits are expected?
It’s not all doom and gloom, as shorter certificate lifetimes come with strong advantages. Organizations will be better equipped to keep pace with changes in the ecosystem, especially as we move toward Post-Quantum Cryptography (PQC). A shorter life cycle promotes better security hygiene by encouraging more automation, resulting in frequent key rotations. This means compromised assets can be swiftly replaced, helping with revocations and reducing overall risk.
Reducing certificate lifetime will also lead to enhanced security, shortening the window for attackers to exploit compromised certificates. In larger organizations, automation is expected to grow, particularly through the use of AI to manage the volume of certificates in rotation. This shift reduces the potential of human error leading to tighter cybersecurity overall.
Let Red Sift Certificates support you
At Red Sift, we understand the pain that comes with new updates and the pressure on your organization to adapt. Our Red Sift Certificates application continuously ingests and monitors every public certificate issued, tracking real-time changes to provide comprehensive oversight and immediate alerts for potential security risks.
Preventing downtime from expired or misconfigured certificates will be critical to an organization’s risk management. While options for mitigation through cloud provider tools or certificate authorities exist, automation isn’t foolproof. Red Sift Certificates provides a more comprehensive solution, offering complete discovery, expiration monitoring, and configuration checks—all in one package. This level of visibility and control is something that other solutions simply can’t match.
Chrome and Apple may have fired the starting gun on the reduction of certificate lifetimes, but Red Sift is here to ensure you win the race. Reduce the pressure to adapt by adopting Red Sift Certificates and streamline your organization’s certification management. By automating your inventory, you can prevent misuse, avoid downtime and stay compliant—speak to the Red Sift team today.






